Download Palo Alto Networks Certified XSIAM Analyst.XSIAM-Analyst.Braindump2go.2025-11-05.30q.vcex
| Vendor: | Palo Alto Networks |
| Exam Code: | XSIAM-Analyst |
| Exam Name: | Palo Alto Networks Certified XSIAM Analyst |
| Date: | Nov 05, 2025 |
| File Size: | 178 KB |
| Downloads: | 2 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Which type of task can be used to create a decision tree in a playbook?
- Sub-playbook
- Job
- Standard
- Conditional
Correct answer: D
Explanation:
Conditional tasks let you define multiple outcome branches based on evaluated expressions, enabling decision-tree logic within a playbook. Conditional tasks let you define multiple outcome branches based on evaluated expressions, enabling decision-tree logic within a playbook.
Question 2
A Cortex XSIAM analyst is investigating a security incident involving a workstation after having deployed a Cortex XDR agent for 45 days. The incident details include the Cortex XDR Analytics Alert “Uncommon remote scheduled task creation.”
Which response will mitigate the threat?
- Revoke user access and conduct a user audit.
- Allow list the processes to reduce alert noise.
- Initiate the endpoint isolate action to contain the threat.
- Prioritize blocking the source IP address to prevent further login attempts.
Correct answer: C
Explanation:
An “Uncommon remote scheduled task creation” suggests possible remote code execution or persistence. Isolating the affected endpoint immediately cuts it off from the network, stopping command-and-control or lateral movement while you investigate and remediate. An “Uncommon remote scheduled task creation” suggests possible remote code execution or persistence. Isolating the affected endpoint immediately cuts it off from the network, stopping command-and-control or lateral movement while you investigate and remediate.
Question 3
Which Cytool command will re-enable protection on an endpoint that has Cortex XDR agent protection paused?
- cytool security enable
- cytool service start
- cytool runtime start
- cytool protect enable
Correct answer: C
Explanation:
cytool runtime start resumes the Cortex XDR agent’s protection modules after they’ve been paused, re-enabling active enforcement on the endpoint. cytool runtime start resumes the Cortex XDR agent’s protection modules after they’ve been paused, re-enabling active enforcement on the endpoint.
Question 4
A Cortex XSIAM analyst is reading a blog that references an unfamiliar critical zero-day vulnerability. This vulnerability has been weaponized, and there is evidence that it is being exploited by threat actors targeting a customer’s industry.
Where can the analyst go within Cortex XSIAM to learn more about this vulnerability and any potential impacts on the customer environment?
- Threat Intel Management –> Sample Analysis
- Attack Surface –> Threat Response Center
- Attack Surface –> Attack Surface Rules
- Threat Intel Management –> Indicator
Correct answer: B
Explanation:
The Threat Response Center centralizes emerging/zero-day vulnerability intelligence and correlates it with your environment, showing impact, affected assets, and recommended actions. The Threat Response Center centralizes emerging/zero-day vulnerability intelligence and correlates it with your environment, showing impact, affected assets, and recommended actions.
Question 5
While investigating an alert, an analyst notices that a URL indicator has a related alert from a previous incident. The related alert has the same URL, but it resolved to a different IP address.
Which combination of two actions should the analyst take to resolve this issue? (Choose two.)
- Enrich the IP address indicator associated with the previous alert.
- Expire the URL indicator.
- Remove the relationship between the URL and the older IP address.
- Enrich the URL indicator.
Correct answer: CD
Explanation:
Removing the outdated URL-IP relationship clears the incorrect linkage, and enriching the URL indicator updates it with the current resolution and context so future alerts reflect the right association. Removing the outdated URL-IP relationship clears the incorrect linkage, and enriching the URL indicator updates it with the current resolution and context so future alerts reflect the right association.
Question 6
Which two actions will allow a security analyst to review updated commands from the core pack and interpret the results without altering the incident audit? (Choose two.)
- Create a playbook with the commands and run it from within the War Room.
- Run the core commands directly by typing them into the playground CLI.
- Run the core commands directly from the Command and Scripts menu inside playground.
- Run the core commands directly from the playground and invite other collaborators.
Correct answer: BC
Explanation:
Executing core pack commands in the Playground — either by typing them in the CLI or selecting them from Command & Scripts — lets you test and view results without writing anything to an incident’s War Room audit trail. Executing core pack commands in the Playground — either by typing them in the CLI or selecting them from Command & Scripts — lets you test and view results without writing anything to an incident’s War Room audit trail.
Question 7
Based on the artifact details in the image below, what can an analyst infer from the hexagon-shaped object with the exclamation mark (!) at the center?
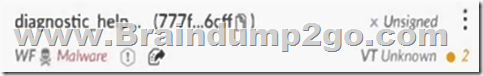
- The malicious artifact was injected.
- The malware requires further analysis.
- The WildFire verdict returned is “Low Confidence.”
- The artifact verdict has changed from a previous state to “Malware.”
Correct answer: D
Explanation:
In Cortex XSIAM, the hexagon with an exclamation mark denotes a verdict change. Seeing it next to the artifact means its status was updated—now classified as Malware. In Cortex XSIAM, the hexagon with an exclamation mark denotes a verdict change. Seeing it next to the artifact means its status was updated—now classified as Malware.
Question 8
An analyst is responding to a critical incident involving a potential ransomware attack. The analyst immediately initiates full isolation on the compromised endpoint using Cortex XSIAM to prevent the malware from spreading across the network. However, the analyst now needs to collect additional forensic evidence from the isolated machine, including memory dumps and disk images, without reconnecting it to the network.
Which action will allow the analyst to collect the required forensic evidence while ensuring the endpoint remains fully isolated?
- Using the management console to remotely run a predefined forensic playbook on the associated alert
- Collecting the evidence manually through the agent by accessing the machine directly and running “Generate Support File”
- Using the endpoint isolation feature to create a secure tunnel for evidence collection
- Disabling full isolation temporarily to allow forensic tools to communicate with the endpoint
Correct answer: A
Explanation:
Full isolation still permits the Cortex agent to communicate with the console, so you can execute a forensic playbook (memory dump, disk/image collection actions) remotely without lifting isolation, keeping the endpoint contained while gathering evidence. Full isolation still permits the Cortex agent to communicate with the console, so you can execute a forensic playbook (memory dump, disk/image collection actions) remotely without lifting isolation, keeping the endpoint contained while gathering evidence.
Question 9
In addition to defining the Rule Name and Severity Level, which step or set of steps accurately reflects how an analyst should configure an indicator prevention rule before reviewing and saving it?
- Filter and select file, IP address, and domain indicators.
- Filter and select indicators of any type.
- Select profiles for prevention.Filter and select one or more file, IP address, and domain indicators.
- Select profiles for prevention.Filter and select one or more SHA256 and MD5 indicators.
Correct answer: C
Explanation:
An indicator prevention rule must bind supported indicator types (file hashes, IPs, domains) to specific prevention profiles so the agent can enforce blocking; after naming and setting severity, you choose the profiles and then pick those indicators before saving. An indicator prevention rule must bind supported indicator types (file hashes, IPs, domains) to specific prevention profiles so the agent can enforce blocking; after naming and setting severity, you choose the profiles and then pick those indicators before saving.
Question 10
During an investigation, an analyst runs the reputation script for an indicator that is listed as Suspicious. The new reputation results display in the War Room as Malicious; however, the indicator verdict does not change.
What is the cause of this behavior?
- The indicator is expired.
- The indicator verdict was manually set to Suspicious.
- The indicator has been excluded.
- The indicator exists as an IOC rule.
Correct answer: B
Explanation:
A manually assigned verdict locks the indicator’s status; automated reputation updates (like the script result showing Malicious) do not override a manual verdict, so it remains Suspicious. A manually assigned verdict locks the indicator’s status; automated reputation updates (like the script result showing Malicious) do not override a manual verdict, so it remains Suspicious.
Question 11
Which two statements apply to IOC rules? (Choose two.)
- They can be uploaded using REST API.
- They can have an expiration date of up to 180 days.
- They can be used to detect a specific registry key.
- They can be excluded using suppression rules but not alert exclusions.
Correct answer: AB
Explanation:
IOC rules can be bulk-uploaded through the REST API, and each rule can include an expiration date — capped at 180 days — to ensure stale indicators age out automatically. IOC rules can be bulk-uploaded through the REST API, and each rule can include an expiration date — capped at 180 days — to ensure stale indicators age out automatically.
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!




