Download Palo Alto Networks Certified Network Security Engineer.PCNSE.TestKing.2019-04-26.95q.vcex
| Vendor: | Palo Alto Networks |
| Exam Code: | PCNSE |
| Exam Name: | Palo Alto Networks Certified Network Security Engineer |
| Date: | Apr 26, 2019 |
| File Size: | 3 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Which CLI command is used to simulate traffic going through the firewall and determine which Security policy rule, NAT translation, static route, or PBF rule will be triggered by the traffic?
- check
- find
- test
- sim
Correct answer: C
Explanation:
Reference: http://www.shanekillen.com/2014/02/palo-alto-useful-cli-commands.html Reference: http://www.shanekillen.com/2014/02/palo-alto-useful-cli-commands.html
Question 2
Refer to exhibit.
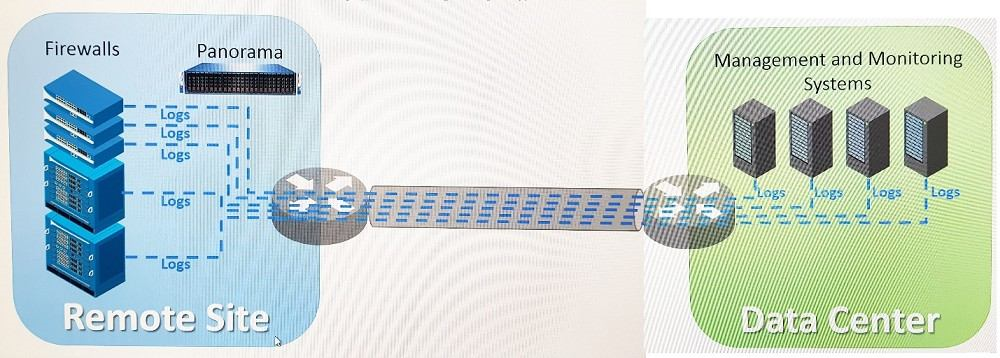
An organization has Palo Alto Networks NGFWs that send logs to remote monitoring and security management platforms. The network team has reported excessive traffic on the corporate WAN.
How could the Palo Alto Networks NGFW administrator reduce WAN traffic while maintaining support for all the existing monitoring/security platforms?
- Forward logs from firewalls only to Panorama and have Panorama forward logs to other external services.
- Forward logs from external sources to Panorama for correlation, and from Panorama send them to the NGFW.
- Configure log compression and optimization features on all remote firewalls.
- Any configuration on an M-500 would address the insufficient bandwidth concerns.
Correct answer: C
Question 3
A customer wants to set up a VLAN interface for a Layer 2 Ethernet port.
Which two mandatory options are used to configure a VLAN interface? (Choose two.)
- Virtual router
- Security zone
- ARP entries
- Netflow Profile
Correct answer: AB
Question 4
An administrator has been asked to configure a Palo Alto Networks NGFW to provide protection against worms and trojans.
Which Security Profile type will protect against worms and trojans?
- Anti-Spyware
- Instruction Prevention
- File Blocking
- Antivirus
Correct answer: D
Explanation:
Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/policy/security-profiles Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/policy/security-profiles
Question 5
A company needs to preconfigure firewalls to be sent to remote sites with the least amount of preconfiguration. Once deployed, each firewall must establish secure tunnels back to multiple regional data centers to include the future regional data centers.
Which VPN configuration would adapt to changes when deployed to the future site?
- Preconfigured GlobalProtect satellite
- Preconfigured GlobalProtect client
- Preconfigured IPsec tunnels
- Preconfigured PPTP Tunnels
Correct answer: A
Question 6
If a template stack is assigned to a device and the stack includes three templates with overlapping settings, which settings are published to the device when the template stack is pushed?
- The settings assigned to the template that is on top of the stack.
- The administrator will be promoted to choose the settings for that chosen firewall.
- All the settings configured in all templates.
- Depending on the firewall location, Panorama decides with settings to send.
Correct answer: A
Question 7
To connect the Palo Alto Networks firewall to AutoFocus, which setting must be enabled?
- Device>Setup>Services>AutoFocus
- Device> Setup>Management >AutoFocus
- AutoFocus is enabled by default on the Palo Alto Networks NGFW
- Device>Setup>WildFire>AutoFocus
- Device>Setup> Management> Logging and Reporting Settings
Correct answer: B
Explanation:
Reference: https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/getting-started/enable-autofocus-threat-intelligence Reference: https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/getting-started/enable-autofocus-threat-intelligence
Question 8
Which two virtualization platforms officially support the deployment of Palo Alto Networks VM-Series firewalls? (Choose two.)
- Red Hat Enterprise Virtualization (RHEV)
- Kernel Virtualization Module (KVM)
- Boot Strap Virtualization Module (BSVM)
- Microsoft Hyper-V
Correct answer: BD
Explanation:
Reference: https://www.paloaltonetworks.com/products/secure-the-network/virtualized-next-generation-firewall/vm-series Reference: https://www.paloaltonetworks.com/products/secure-the-network/virtualized-next-generation-firewall/vm-series
Question 9
Which User-ID method maps IP addresses to usernames for users connecting through an 802.1x-enabled wireless network device that has no native integration with PAN-OS® software?
- XML API
- Port Mapping
- Client Probing
- Server Monitoring
Correct answer: A
Explanation:
Captive Portal and the other standard user mapping methods might not work for certain types of user access. For example, the standard methods cannot add mappings of users connecting from a third-party VPN solution or users connecting to a 802.1x-enabled wireless network. For such cases, you can use the PAN-OS XML API to capture login events and send them to the PAN-OS integrated User-ID agent Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/user-id/user-id-concepts/group-mapping#id93306080-fd9b-4f1b-96a6-4bfe1c8e69df Captive Portal and the other standard user mapping methods might not work for certain types of user access. For example, the standard methods cannot add mappings of users connecting from a third-party VPN solution or users connecting to a 802.1x-enabled wireless network. For such cases, you can use the PAN-OS XML API to capture login events and send them to the PAN-OS integrated User-ID agent
Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/user-id/user-id-concepts/group-mapping#id93306080-fd9b-4f1b-96a6-4bfe1c8e69df
Question 10
Decrypted packets from the website https://www.microsoft.com will appear as which application and service within the Traffic log?
- web-browsing and 443
- SSL and 80
- SSL and 443
- web-browsing and 80
Correct answer: B
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



