Download Palo Alto Networks Certified Network Security Engineer.PCNSE.NewDumps.2021-03-11.310q.vcex
| Vendor: | Palo Alto Networks |
| Exam Code: | PCNSE |
| Exam Name: | Palo Alto Networks Certified Network Security Engineer |
| Date: | Mar 11, 2021 |
| File Size: | 25 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
When configuring a GlobalProtect Portal, what is the purpose of specifying an Authentication Profile?
- To enable Gateway authentication to the Portal
- To enable Portal authentication to the Gateway
- To enable user authentication to the Portal
- To enable client machine authentication to the Portal
Correct answer: C
Explanation:
The additional options of Browser and Satellite enable you to specify the authentication profile to use for specific scenarios. Select Browser to specify the authentication profile to use to authenticate a user accessing the portal from a web browser with the intent of downloading the GlobalProtect agent (Windows and Mac). Select Satellite to specify the authentication profile to use to authenticate the satellite. https://www.paloaltonetworks.com/documentation/71/pan-os/web-interface-help/globalprotect/network-globalprotect-portals The additional options of Browser and Satellite enable you to specify the authentication profile to use for specific scenarios. Select Browser to specify the authentication profile to use to authenticate a user accessing the portal from a web browser with the intent of downloading the GlobalProtect agent (Windows and Mac). Select Satellite to specify the authentication profile to use to authenticate the satellite.
https://www.paloaltonetworks.com/documentation/71/pan-os/web-interface-help/globalprotect/network-globalprotect-portals
Question 2
For which two functions is the management plane responsible? (Choose two.)
- Protocol decoding
- Reassembling packets
- Forwarding logs
- Answering HTTP requests
Correct answer: CD
Question 3
In order to route traffic between layer 3 interfaces on the PAN firewall you need:
- VLAN
- Vwire
- Security Profile
- Virtual Router
Correct answer: D
Question 4
Which User-ID method maps IP addresses to usernames for users connecting through an 802.1x-enabled wireless network device that has no native integration with PAN-OS software?
- XML API
- Port Mapping
- Client Probing
- Server Monitoring
Correct answer: A
Explanation:
Captive Portal and the other standard user mapping methods might not work for certain types of user access. For example, the standard methods cannot add mappings of users connecting from a third-party VPN solution or users connecting to a 802.1x-enabled wireless network. For such cases, you can use the PAN-OS XML API to capture login events and send them to the PAN-OS integrated User-ID agent 2 IT Certification Guaranteed, The Easy Way! Captive Portal and the other standard user mapping methods might not work for certain types of user access. For example, the standard methods cannot add mappings of users connecting from a third-party VPN solution or users connecting to a 802.1x-enabled wireless network. For such cases, you can use the PAN-OS XML API to capture login events and send them to the PAN-OS integrated User-ID agent 2 IT Certification Guaranteed, The Easy Way!
Question 5
When using the predefined default antivirus profile, the policy will inspect for viruses on the decoders. Match each decoder with its default action. Answer options may be used more than once or not at all. (select four)
- IMAP - Alert
- IMAP - Reset-both
- HTTP - Alert
- HTTP - Reset-both
- FTP, SMB - Alert
- FTP, SMB - Reset-both
- POP3, SMTP - Alert
- POP3, SMTP - Reset-both
Correct answer: ADFG
Explanation:
The default profile inspects all of the listed protocol decoders for viruses, and generates alerts for SMTP, IMAP, and POP3 protocols while blocking for FTP, HTTP, and SMB protocols. https://www.paloaltonetworks.com/documentation/70/pan-os/pan-os/policy/antivirus-profiles The default profile inspects all of the listed protocol decoders for viruses, and generates alerts for SMTP, IMAP, and POP3 protocols while blocking for FTP, HTTP, and SMB protocols.
https://www.paloaltonetworks.com/documentation/70/pan-os/pan-os/policy/antivirus-profiles
Question 6
Company.com has an in-house application that the Palo Alto Networks device doesn't identify correctly.
A Threat Management Team member has mentioned that this in-house application is very sensitive and all traffic being identified needs to be inspected by the Content-ID engine.
Which method should company.com use to immediately address this traffic on a Palo Alto Networks device?
- Create a custom Application without signatures, then create an Application Override policy that includes the source, Destination, Destination Port/Protocol and Custom Application of the traffic.
- Wait until an official Application signature is provided from Palo Alto Networks.
- Modify the session timer settings on the closest referanced application to meet the needs of the in-house application
- Create a Custom Application with signatures matching unique identifiers of the in-house application traffic
Correct answer: D
Question 7
Which Security Policy Rule configuration option disables antivirus and anti-spyware scanning of server-to-client flows only?
- Disable Server Response Inspection
- Apply an Application Override
- Disable HIP Profile
- Add server IP Security Policy exception
Correct answer: A
Explanation:
In the Other Settings section, select the option to Disable Server Response Inspection. This setting disables the antivirus and anti-spyware scanning on the server-side responses, and thus reduces the load on the firewall. https://www.paloaltonetworks.com/documentation/60/pan-os/pan-os/getting-started/set-up-basic-security-policies In the Other Settings section, select the option to Disable Server Response Inspection. This setting disables the antivirus and anti-spyware scanning on the server-side responses, and thus reduces the load on the firewall.
https://www.paloaltonetworks.com/documentation/60/pan-os/pan-os/getting-started/set-up-basic-security-policies
Question 8
View the GlobalProtect configuration screen capture. What is the purpose of this configuration?
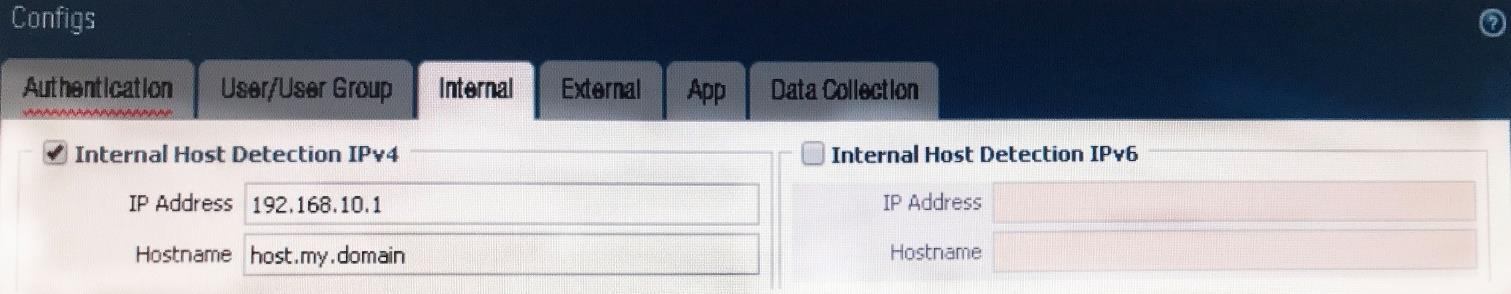
- It configures the tunnel address of all internal clients to an IP address range starting at 192.168.10.1.
- It forces an internal client to connect to an internal gateway at IP address 192.168.10.1.
- It enables a client to perform a reverse DNS lookup on 192.168.10.1 to detect that it is an internal client.
- It forces the firewall to perform a dynamic DNS update, which adds the internal gateway's hostname and IP address to the DNS server.
Correct answer: C
Question 9
In which two types of deployment is active/active HA configuration supported? (Choose two.)
- Layer 3 mode
- TAP mode
- Virtual Wire mode
- Layer 2 mode
Correct answer: AC
Question 10
Which two actions would be part of an automatic solution that would block sites with untrusted certificates without enabling SSL Forward Proxy? (Choose two.)
- Create a no-decrypt Decryption Policy rule.
- Configure an EDL to pull IP addresses of known sites resolved from a CRL.
- Create a Dynamic Address Group for untrusted sites
- Create a Security Policy rule with vulnerability Security Profile attached.
- Enable the "Block sessions with untrusted issuers" setting.
Correct answer: AD
Explanation:
https://www.paloaltonetworks.com/documentation/71/pan-os/web-interface-help/objects/objects-decryption-profile https://www.paloaltonetworks.com/documentation/71/pan-os/web-interface-help/objects/objects-decryption-profile
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



