Download Palo Alto Networks Certified Network Security Administrator.PCNSA.Prep4Sure.2019-09-11.38q.vcex
| Vendor: | Palo Alto Networks |
| Exam Code: | PCNSA |
| Exam Name: | Palo Alto Networks Certified Network Security Administrator |
| Date: | Sep 11, 2019 |
| File Size: | 742 KB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Which two configuration settings shown are not the default? (Choose two.)
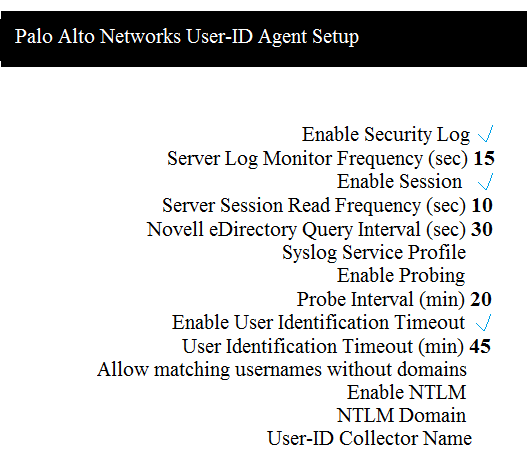
- Enable Security Log
- Server Log Monitor Frequency (sec)
- Enable Session
- Enable Probing
Correct answer: BC
Explanation:
Reference: https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-web-interface-help/user-identification/device-user-identification-user-mapping/enable-server-monitoring Reference: https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-web-interface-help/user-identification/device-user-identification-user-mapping/enable-server-monitoring
Question 2
Which data-plane processor layer of the graphic shown provides uniform matching for spyware and vulnerability exploits on a Palo Alto Networks Firewall?
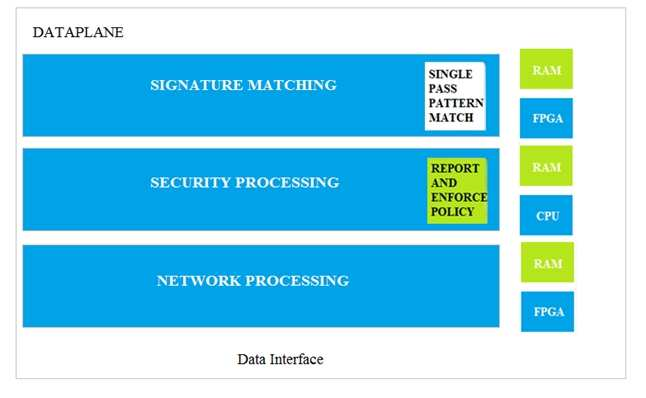
- Signature Matching
- Network Processing
- Security Processing
- Security Matching
Correct answer: A
Question 3
Which option shows the attributes that are selectable when setting up application filters?
- Category, Subcategory, Technology, and Characteristic
- Category, Subcategory, Technology, Risk, and Characteristic
- Name, Category, Technology, Risk, and Characteristic
- Category, Subcategory, Risk, Standard Ports, and Technology
Correct answer: B
Explanation:
Reference: https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-web-interface-help/objects/objects-application-filters Reference: https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-web-interface-help/objects/objects-application-filters
Question 4
Actions can be set for which two items in a URL filtering security profile? (Choose two.)
- Block List
- Custom URL Categories
- PAN-DB URL Categories
- Allow List
Correct answer: AD
Question 5
Which statement is true regarding a Best Practice Assessment?
- The BPA tool can be run only on firewalls
- It provides a percentage of adoption for each assessment area
- The assessment, guided by an experienced sales engineer, helps determine the areas of greatest risk where you should focus prevention activities
- It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture
Correct answer: B
Explanation:
Reference: https://docs.paloaltonetworks.com/best-practices/8-1/data-center-best-practices/data-center-best-practice-security-policy/use-palo-alto-networks-assessment-and-review-tools Reference: https://docs.paloaltonetworks.com/best-practices/8-1/data-center-best-practices/data-center-best-practice-security-policy/use-palo-alto-networks-assessment-and-review-tools
Question 6
Employees are shown an application block page when they try to access YouTube. Which security policy is blocking the YouTube application?
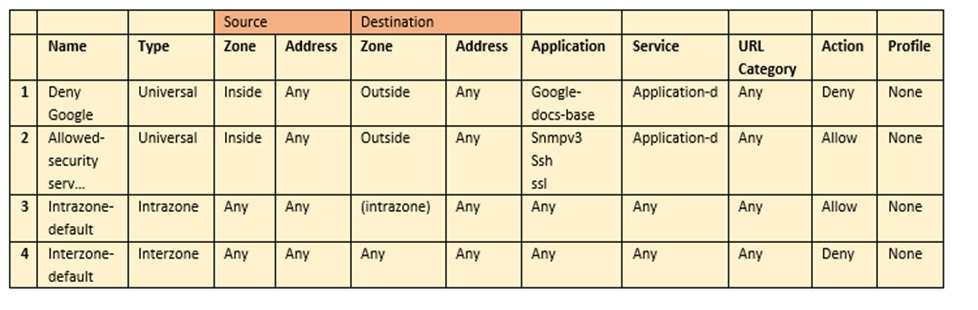
- intrazone-default
- Deny Google
- allowed-security services
- interzone-default
Correct answer: D
Explanation:
Question 7
Which interface does not require a MAC or IP address?
- Virtual Wire
- Layer3
- Layer2
- Loopback
Correct answer: A
Question 8
A company moved its old port-based firewall to a new Palo Alto Networks NGFW 60 days ago. Which utility should the company use to identify out-of-date or unused rules on the firewall?
- Rule Usage Filter > No App Specified
- Rule Usage Filter >Hit Count > Unused in 30 days
- Rule Usage Filter > Unused Apps
- Rule Usage Filter > Hit Count > Unused in 90 days
Correct answer: D
Question 9
Order the steps needed to create a new security zone with a Palo Alto Networks firewall.
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
Question 10
What are two differences between an implicit dependency and an explicit dependency in App-ID? (Choose two.)
- An implicit dependency does not require the dependent application to be added in the security policy
- An implicit dependency requires the dependent application to be added in the security policy
- An explicit dependency does not require the dependent application to be added in the security policy
- An explicit dependency requires the dependent application to be added in the security policy
Correct answer: AD
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



