Download Oracle Cloud Infrastructure (OCI) 2019 Architect Professional.1Z0-997.CertDumps.2020-06-25.72q.vcex
| Vendor: | Oracle |
| Exam Code: | 1Z0-997 |
| Exam Name: | Oracle Cloud Infrastructure (OCI) 2019 Architect Professional |
| Date: | Jun 25, 2020 |
| File Size: | 2 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
A company has an urgent requirement to migrate 300 TB of data to Oracle Cloud Infrastructure (OCI) In two weeks. Their data center has been recently struck by a massive hurricane and the building has been badly damaged, although still operational. They have a 100 Mbps Internet line but the connection is Intermittent due to the damages caused to the electrical grid in this scenario, what is the most effective service to use to migrate the data to OCI given the time constraints?
- Setup a OCI Storage Gateway to connect your data center and your VCN. Once the connection has been established, upload all data to OCI using OCI Storage Gateway Cloud Sync tool.
- Setup a hybrid network by launching aIGbpsFastConnect virtual circuit between your data center and OCI. Use OCI Object storage multipart upload tool to automate the migration of your data to OCI.
- Use multiple OCI Data Transfer Appliances to transfer data to OCI.
- Upload the data to OCI using OCI Object Storage multipart upload tool.
- Storage Gateway to connect your data center and your VCN. Once the connection has been established, upload all data to OCI.
Correct answer: C
Explanation:
Due to the network speed is not good enough and the connection is Intermittent due to the damages caused to the electrical grid Oracle offers offline data transfer solutions that let you migrate data to Oracle Cloud Infrastructure. You have 2 Options of Data Transfer DISK-BASED DATA TRANSFER You send your data as files on encrypted commodity disk to an Oracle transfer site. Operators at the Oracle transfer site upload the files into your designated Object Storage bucket in your tenancy. APPLIANCE-BASED DATA TRANSFER you send your data as files on secure, high-capacity, Oracle-supplied storage appliances to an Oracle transfer site. Operators at the Oracle transfer site upload the data into your designated Object Storage bucket in your tenancy. Due to the network speed is not good enough and the connection is Intermittent due to the damages caused to the electrical grid Oracle offers offline data transfer solutions that let you migrate data to Oracle Cloud Infrastructure.
You have 2 Options of Data Transfer DISK-BASED DATA TRANSFER
You send your data as files on encrypted commodity disk to an Oracle transfer site. Operators at the Oracle transfer site upload the files into your designated Object Storage bucket in your tenancy.
APPLIANCE-BASED DATA TRANSFER
you send your data as files on secure, high-capacity, Oracle-supplied storage appliances to an Oracle transfer site. Operators at the Oracle transfer site upload the data into your designated Object Storage bucket in your tenancy.
Question 2
A hospital in Austin has hosted its web based medical records portal entirely In Oracle cloud Infrastructure (OCI) using Compute Instances for its web-tier and DB system database for its data tier. To validate compliance with Health Insurance Portability and Accountability (HIPAA), the security professional to check their systems it was found that there are a lot of unauthorized coming requests coming from a set of IP addresses originating from a country in Southeast Asia.
Which option can mitigate this type of attack?
- Block the attacking IP address by creating by Network Security Group rule to deny access to the compute Instance where the web server Is running
- Block the attacking IP address by implementing a OCI Web Application Firewall policy using Access Control Rules
- Mitigate the attack by changing the Route fable to redirect the unauthorized traffic to a dummy Compute instance
- Block the attacking IP address by creating a Security List rule to deny access to the subnet where the web server Is running
Correct answer: B
Explanation:
WAF can protect any internet facing endpoint, providing consistent rule enforcement across a customer's applications. WAF provides you with the ability to create and manage rules for internet threats including Cross-Site Scripting (XSS), SQL Injection and other OWASP-defined vulnerabilities. Unwanted bots can be mitigated while tactically allowed desirable bots to enter. Access rules can limit based on geography or the signature of the request. As a WAF administrator you can define explicit actions for requests that meet various conditions. Conditions use various operations and regular expressions. A rule action can be set to log and allow, detect, or block requests WAF can protect any internet facing endpoint, providing consistent rule enforcement across a customer's applications.
WAF provides you with the ability to create and manage rules for internet threats including Cross-Site Scripting (XSS), SQL Injection and other OWASP-defined vulnerabilities. Unwanted bots can be mitigated while tactically allowed desirable bots to enter. Access rules can limit based on geography or the signature of the request.
As a WAF administrator you can define explicit actions for requests that meet various conditions. Conditions use various operations and regular expressions. A rule action can be set to log and allow, detect, or block requests
Question 3
You are working as a security consultant with a global insurance organization which is using Microsoft Azure Active Directory (AD) as identity provided to manager user login/passwords. When a user logs in to Oracle Cloud infrastructure (OCI) console, it should get authenticated by Azure AD. Which set of steps are required to configure at OCI side in order to get it enabled
- Setup Azure AD as an Enterprise Application, map Azure AD users and groups and policies to OCI groups and users
- Setup Azure AD as an Identity Provider, Import users and groups from Azure AD to OCI, set up IAM policies to govern access to Azure AD groups
- Setup Azure AD as an Enterprise Application, configure OCI for single sign-on, map Azure AD groups to OCI groups, set up the IAM policies to govern access to Azure AD groups
- Setup Azure AD as an Identity Provider, map Azure AD groups to OCI groups, set up the IAM policies to govern access to Azure AD groups
Correct answer: D
Explanation:
Federating with Microsoft Azure Active Directory To federate with Azure AD, you set up Oracle Cloud Infrastructure as a basic SAML single sign-on application in Azure AD. To set up this application, you perform some steps in the Oracle Cloud Infrastructure Console and some steps in Azure AD. Following is the general process an administrator goes through to set up the federation. Details for each step are given in the next section. In Oracle Cloud Infrastructure, download the federation metadata document. In Azure AD, set up Oracle Cloud Infrastructure Console as an enterprise application. In Azure AD, configure the Oracle Cloud Infrastructure enterprise application for single sign-on. In Azure AD, set up the user attributes and claims. In Azure AD, download the Azure AD SAML metadata document. In Azure AD, assign user groups to the application. In Oracle Cloud Infrastructure, set up Azure AD as an identity provider. In Oracle Cloud Infrastructure, map your Azure AD groups to Oracle Cloud Infrastructure groups. In Oracle Cloud Infrastructure, set up the IAM policies to govern access for your Azure AD groups. Share the Oracle Cloud Infrastructure sign-in URL with your user Federating with Microsoft Azure Active Directory
To federate with Azure AD, you set up Oracle Cloud Infrastructure as a basic SAML single sign-on application in Azure AD. To set up this application, you perform some steps in the Oracle Cloud Infrastructure Console and some steps in Azure AD.
Following is the general process an administrator goes through to set up the federation. Details for each step are given in the next section.
In Oracle Cloud Infrastructure, download the federation metadata document. In Azure AD, set up Oracle Cloud Infrastructure Console as an enterprise application. In Azure AD, configure the Oracle Cloud Infrastructure enterprise application for single sign-on.
In Azure AD, set up the user attributes and claims.
In Azure AD, download the Azure AD SAML metadata document. In Azure AD, assign user groups to the application.
In Oracle Cloud Infrastructure, set up Azure AD as an identity provider. In Oracle Cloud Infrastructure, map your Azure AD groups to Oracle Cloud Infrastructure groups. In Oracle Cloud Infrastructure, set up the IAM policies to govern access for your Azure AD groups. Share the Oracle Cloud Infrastructure sign-in URL with your user
Question 4
You want to automate the processing of new Image files to generate thumbnails. the expected rate is 10 new files every hour.
Which of the following is the most cost effective option to meet this requirement in Oracle Cloud Infrastructure (OCI)?
- Upload files to an OCI Object storage bucket. Every time a file is uploaded, an event is emitted.Write a rule to filter these events with an action to trigger a function in Oracle Functions.The function processes the image in the file and stores the thumbnails back in an Object storage bucket.
- Upload files to an OCI Object storage bucket.Every time a file is uploaded, trigger an event with an action to provision a compute instance with a cloud-init script to access the file, process it and store it back in an Object storage bucket.Terminate the instance using Autoscaling policy after the processing is finished.
- Build a web application to ingest the files and save them to a NoSQL Database.Configure OCI Events service to trigger a notification using Oracle Notification Service (ONS).ONS invokes a custom application to process the image files to generate thumbnails. Store thumbnails in a NoSQL Database table.
- Upload all files to an Oracle Streaming Service (OSS) stream.Set up a cron job to invoke a function in Oracle Functions to fetch data from the stream.Invoke another function to process the image files and generate thumbnails.Store thumbnails in another OSS stream.
Correct answer: A
Explanation:
You can invoke a function that you've deployed to Oracle Functions by triggered by an event in the Events service when update the Object storage to fetch the data then the function can process the File and store back to Object storage You can invoke a function that you've deployed to Oracle Functions by triggered by an event in the Events service when update the Object storage to fetch the data then the function can process the File and store back to Object storage
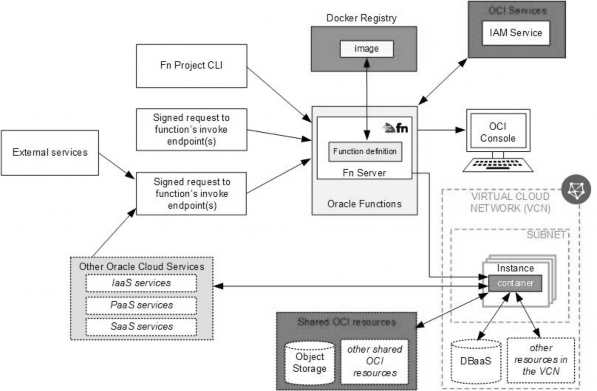
Question 5
A new International hacktivfst group based in London, launched a wide scale cyber attacks Including SQL Injection and Cross-Site Scripting (XSS) across multiple websites which are hosted in Oracle Cloud Infrastructure (OCI). As an IT consultant, you must configure a Web Application Firewall (WAF) to protect these website against the attacks.
How should you configure your WAF to protect the website against those attacks?
- Enable an Access Rule that contains XSS Filters Categories and SQL Filters Categories.
- Enable a Protection Rule to block the attacks based on HTTP Headers that contain XSS and SQL strings.
- Enable a Protection Rule that contains XSS Filters Categories and SQL Filters Categories.
- Enable an Access Rule to block the IP Address range from London.
- Enable a Protection Rule to block requests that came from London.
Correct answer: C
Explanation:
https://www.ateam-oracle.com/using-oci-waf-web-application-firewall-with-oracle-e-business-suite https://www.ateam-oracle.com/using-oci-waf-web-application-firewall-with-oracle-e-business-suite
Question 6
Your customer has gone through a recent departmental re structure. As part of this change, they are organizing their Oracle Cloud Infrastructure (OCI) compartment structure to align with the company's new organizational structure.
They have made the following change:
Compartment x Is moved, and its parent compartment is now compartment c.
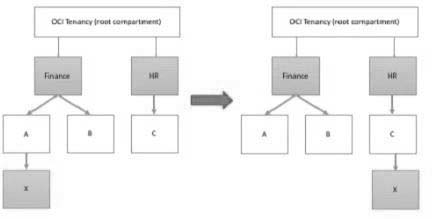
Policy defined in compartment A: Allow group networkadmins to manage subnets in compartment X Policy defined in root compartment: Allow group admins to read subnets in compartment Finance:A:X After the compartment move, which action will provide users of group networkadmins and admins with similar privileges as before the move?
- Define a policy in Compartment C as follows: Allow group network admins to manage subnets in compartment X.
- No change in any policy statement is required as compartments move automatically moves alt the policy statements associated with compartments as well.
- Define a policy in compartment C as follows: Allow group admins to read subnets in compartment HR:C:X
- Define a policy in compartment HR as follows: Allow group network admins to manage subnets in compartment X.
- Define a policy in compartment C as follows Allow group admins to read subnets in compartment HR:C:X
Correct answer: A
Explanation:
You can move a compartment to a different parent compartment within the same tenancy. When you move a compartment, all its contents (subcom partments and resources) are moved with it. After you move a compartment to a new parent compartment, the access policies of the new parent take effect and the policies of the previous parent no longer apply. Before you move a compartment, ensure that:- You are aware of the policies that govern access to the compartment in its current position. - You are aware of the polices in the new parent compartment that will take effect when you move the compartment. 1- Policy that defined in root compartment: Allow group admins to read subnets in compartment Finance:A:X you move compartment X from Finance:A to HR:C. The policy that governs compartment X is attached to the shared parent, root compartment. When the compartment X is moved, the policy statement is automatically updated by the IAM service to specify the new compartment location. The policy Allow group admins to read subnets in compartment Finance:A:X is updated to Allow group admins to read subnets in compartment HR:C:X so the admins group will have the same access after the compartment X is moved 2- Policy that defined in compartment A: Allow group networkadmins to manage subnets in compartment X you move compartment X from Finance:A to HR:C. However, the policy that governs compartment X here is attached directly to the A compartment. When the compartment is moved, the policy is not automatically updated. The policy that specifies compartment X is no longer valid and must be manually removed. Group networkadmins no longer has access to compartment X in its new location under HR:C. Unless another existing policy grants access to group networkadmins , you must create a new policy to allow networkadmins to continue to manage buckets in compartment X. You can move a compartment to a different parent compartment within the same tenancy. When you move a compartment, all its contents (subcom partments and resources) are moved with it. After you move a compartment to a new parent compartment, the access policies of the new parent take effect and the policies of the previous parent no longer apply. Before you move a compartment, ensure that:
- You are aware of the policies that govern access to the compartment in its current position.
- You are aware of the polices in the new parent compartment that will take effect when you move the compartment.
1- Policy that defined in root compartment: Allow group admins to read subnets in compartment Finance:A:X you move compartment X from Finance:A to HR:C. The policy that governs compartment X is attached to the shared parent, root compartment. When the compartment X is moved, the policy statement is automatically updated by the IAM service to specify the new compartment location.
The policy
Allow group admins to read subnets in compartment Finance:A:X is updated to Allow group admins to read subnets in compartment HR:C:X so the admins group will have the same access after the compartment X is moved 2- Policy that defined in compartment A: Allow group networkadmins to manage subnets in compartment X you move compartment X from Finance:A to HR:C. However, the policy that governs compartment X here is attached directly to the A compartment. When the compartment is moved, the policy is not automatically updated. The policy that specifies compartment X is no longer valid and must be manually removed. Group networkadmins no longer has access to compartment X in its new location under HR:C. Unless another existing policy grants access to group networkadmins , you must create a new policy to allow networkadmins to continue to manage buckets in compartment X.
Question 7
A cloud consultant is working on implementation project on OCI. As part of the compliance requirements, the objects placed in object storage should be automatically archived first and then deleted. He is testing a Lifecycle Policy on Object Storage and created a policy as below:
[ { "name": "Archive_doc", "action": "ARCHIVE", "objectNameFilter": { "inclusionPrefixes": "doc"] }, "timeAmount": 5,"timeunit": "DAYS", "isEnabled": true }, { "name": "Delete_doc", "action": "DELETE", "objectNameFilter": "inclusionPrefixes": ["doc"] 1."timeAmount": 5, "timeunit": "DAYS", "isEnabled": true } What will happen after this policy is applied?
- All objects with names starting with "doc" will be deleted after 5 days of object creation
- All the objects having file extension ".doc" will be archived for 5 days and will be deleted 10 days after object creation
- All the objects having file extension ".doc" will be archived 5 days after object creation
- All the objects with names starting with "doc" will be archived 5 days after object creation and will be deleted 5 days after archival
Correct answer: A
Explanation:
Object Lifecycle Management works by defining rules that instruct Object Storage to archive or delete objects on your behalf within a given bucket. A bucket's lifecycle rules are collectively known as an object lifecycle policy. You can use a rule to either archive or delete objects and specify the number of days until the specified action is taken. A rule that deletes an object always takes priority over a rule that would archive that same object. Object Lifecycle Management works by defining rules that instruct Object Storage to archive or delete objects on your behalf within a given bucket. A bucket's lifecycle rules are collectively known as an object lifecycle policy.
You can use a rule to either archive or delete objects and specify the number of days until the specified action is taken.
A rule that deletes an object always takes priority over a rule that would archive that same object.
Question 8
A startup company is looking for a solution for processing of data transmitted by the IOT devices fitted to transport vehicles that carry frozen foods. The data should be consumed and processed in real time. The processed data should be archived to OCI Object Storage bucket. and use Autonomous Data warehouse (ADW) to handle analytics.
Which architecture will help you meet this requirement?
- Use OCI Streaming Service to collect the incoming biometric data. Use an open source Hadoop cluster to analyze the data horn streaming service. Store the results to OCI Autonomous Data warehouse (ADW) to handle complex analytics
- Use OCI Streaming Service to collect the incoming biometric data. Use Oracle Functions to process the date and show the results on a real-time dashboard and store the results lo OCI Object Storage Store the data In OCI Autonomous Data warehouse (ADW) to handle analytics.
- Create an OCI Object Storage bucket to collect the incoming biometric data from the smart pet collar Fetch the data horn OC\ Object storage to OCI Autonomous Data Warehouse (ADW) every day and run analytics Jobs with it
- Launch an open source Hadoop cluster to collect the Incoming biometrics data Use an Open source Fluentd cluster to analyze the- data me results to OCI Autonomous Transaction Processing (ADW)to handle complex analytics
Correct answer: B
Explanation:
Real-time processing of high-volume streams of data - OCI Streaming service provides a fully managed, scalable, durable storage option for continuous, highvolume streams of data that you can consume and process in real-time - Use cases Log and Event data collection Web/Mobile activity data ingestion IoT Data streaming for processing and alerts Messaging: use streaming to decouple components of large systems- Oracle managed service with REST APIs (Create, Put, Get, Delete) - Integrated Monitoring Real-time processing of high-volume streams of data
- OCI Streaming service provides a fully managed, scalable, durable storage option for continuous, highvolume streams of data that you can consume and process in real-time
- Use cases
Log and Event data collection Web/Mobile activity data ingestion
IoT Data streaming for processing and alerts
Messaging: use streaming to decouple components of large systems
- Oracle managed service with REST APIs (Create, Put, Get, Delete)
- Integrated Monitoring
Question 9
You are currently working for a public health care company based in the United Stats. Their existing patient records runs in an on-premises data center and the customer is sending tape backups offsite as part of their recovery planning.
You have developed an alternative archival solution using Oracle Cloud Infrastructure (OCI) that will save the company a significant amount of mom on a yearly basis. The solution involves storing data in an OCI Object Storage bucket After reviewing your solution with the customer global Compliance (GRC) team they have highlighted the following security requirements:
- All data less than 1 year old must be accessible within 2 hour.
- All data must be retained for at least 10 years and be accessible within 48 hours
- AH data must be encrypted at rest
- No data may be transmitted across the public Internet
Which two options meet the requirements outlined by the customer GRC team?
- Provision a FastConnect link to the closest OCI region and configure a private peering virtual circuit.
- Create an OCI Object Storage Standard tier bucket Configure a lifecycle policy to archive any object that Is older than 365 days
- Create a VPN connection between your on premises data center and OCI. Create a Virtual Cloud Network (VCN) along with an OCI Service Gateway for OCI Object Storage.
- Provision a FastConnect link to the closest OCI region and configure a public peering virtual circuit
- Create an OCI Object Storage Standard tier bucket. Configure a lifecycle policy to delete any object that is older than 7 years
Correct answer: BD
Explanation:
The Oracle Services Network is a conceptual network in Oracle Cloud Infrastructure that is reserved for Oracle services. These services have public IP addresses that you typically reach over the internet. However, you can access the Oracle Services Network without the traffic going over the internet. There are different ways, depending on which of your hosts need the access: Hosts in your on-premises network:- Private access through a VCN with FastConnect private peering or VPN Connect: The on-premises hosts use private IP addresses and reach the Oracle Services Network by way of the VCN and the VCN's service gateway. - Public access with FastConnect public peering: The on-premises hosts use public IP addresses. regarding which Fastconnect Public peering: To access public services in Oracle Cloud Infrastructure without using the internet. For example, Object Storage, the Oracle Cloud Infrastructure Console and APIs, or public load balancers in your VCN. Communication across the connection is with IPv4 public IP addresses. Without FastConnect, the traffic destined for public IP addresses would be routed over the internet. With FastConnect, that traffic goes over your private physical connection. so Answer 4 will be the best answer that meets the customer requirement A service gateway lets your virtual cloud network (VCN) privately access specific Oracle services without exposing the data to the public internet. No internet gateway or NAT is required to reach those specific services. The resources in the VCN can be in a private subnet and use only private IP addresses. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet. Object Lifecycle Management lets you automatically manage the archiving and deletion of objects. By using Object Lifecycle Management to manage your Object Storage and Archive Storage data, you can reduce your storage costs and the amount of time you spend managing data. The Oracle Services Network is a conceptual network in Oracle Cloud Infrastructure that is reserved for Oracle services.
These services have public IP addresses that you typically reach over the internet. However, you can access the Oracle Services Network without the traffic going over the internet.
There are different ways, depending on which of your hosts need the access: Hosts in your on-premises network:
- Private access through a VCN with FastConnect private peering or VPN Connect: The on-premises hosts use private IP addresses and reach the Oracle Services Network by way of the VCN and the VCN's service
gateway.
- Public access with FastConnect public peering: The on-premises hosts use public IP addresses. regarding which Fastconnect Public peering: To access public services in Oracle Cloud Infrastructure without using the internet. For example, Object Storage, the Oracle Cloud Infrastructure Console and APIs, or public load balancers in your VCN. Communication across the connection is with IPv4 public IP addresses. Without FastConnect, the traffic destined for public IP addresses would be routed over the internet. With FastConnect, that traffic goes over your private physical connection. so Answer 4 will be the best answer that meets the customer requirement A service gateway lets your virtual cloud network (VCN) privately access specific Oracle services without exposing the data to the public internet. No internet gateway or NAT is required to reach those specific services. The resources in the VCN can be in a private subnet and use only private IP addresses. The traffic from the VCN to the Oracle service travels over the Oracle network fabric and never traverses the internet. Object Lifecycle Management lets you automatically manage the archiving and deletion of objects. By using Object Lifecycle Management to manage your Object Storage and Archive Storage data, you can reduce your storage costs and the amount of time you spend managing data.
Question 10
An online Stock trading application is deployed to multiple Availability Domains in the us phoenix-1 region. Considering the high volume of transactions that the trading application handles, the company has hired you to ensure that the data stored by the application available, and disaster resilient. In the event of failure, the Recovery lime Objective (UK)) must be less than 2 hours to meet regulator requirements.
Which Disaster Recovery strategy should be used to achieve the RTO requirement In the event of system failure?
- Configure hourly block volumes backups through the Storage Gateway service.
- Configure hourly block volumes backups using the Oracle Cloud Infrastructure (OCI) Command Line Interface (CLI)
- Store hourly block volumes backup to NVMe device under a compute instance and generate a custom Image every 5 minutes.
- Configure your application to use synchronous master slave data replication between Availability Domains.
Correct answer: B
Explanation:
You can use the CLI, REST APIs, or the SDKs to automate, script, and manage volume backups and their lifecycle. Planning Your Backup The primary use of backups is to support business continuity, disaster recovery, and long-term archiving requirements. When determining a backup schedule, your backup plan and goals should consider the following:Frequency: How often you want to back up your data.Recovery time: How long you can wait for a backup to be restored and accessible to the applications that use it. The time for a backup to complete varies on several factors, but it will generally take a few minutes or longer, depending on the size of the data being backed up and the amount of data that has changed since your last backup. Number of stored backups: How many backups you need to keep available and the deletion schedule for those you no longer need. You can only create one backup at a time, so if a backup is underway, it will need to complete before you can create another one. For details about the number of backups you can store You can use the CLI, REST APIs, or the SDKs to automate, script, and manage volume backups and their lifecycle.
Planning Your Backup
The primary use of backups is to support business continuity, disaster recovery, and long-term archiving requirements. When determining a backup schedule, your backup plan and goals should consider the following:
Frequency: How often you want to back up your data.
Recovery time: How long you can wait for a backup to be restored and accessible to the applications that use it. The time for a backup to complete varies on several factors, but it will generally take a few minutes or longer, depending on the size of the data being backed up and the amount of data that has changed since your last backup.
Number of stored backups: How many backups you need to keep available and the deletion schedule for those you no longer need. You can only create one backup at a time, so if a backup is underway, it will need to complete before you can create another one. For details about the number of backups you can store
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



