Download Oracle Cloud Infrastructure 2020 Cloud Operations Associate.1Z0-1067-20.NewDumps.2021-04-12.65q.vcex
| Vendor: | Oracle |
| Exam Code: | 1Z0-1067-20 |
| Exam Name: | Oracle Cloud Infrastructure 2020 Cloud Operations Associate |
| Date: | Apr 12, 2021 |
| File Size: | 3 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
You have been asked to update the lifecycle policy for object storage using the Oracle Cloud Infrastructure (OCI) Command Line Interface (CLI).
Which command can successfully update the policy?
- oci os object-lifecycle-policy get -ns <object_storage_namespace> -bn <bucket_name>
- oci os object-lifecycle-policy put -ns <object_storage_namespace> -bn <bucket_name> O
- oci os object-lifecycle-policy put -ns <object_storage_namespace> -bn <bucket_name> -Items <json_formated_lifecycle_policy>
- oci os object-lifecycle-policy delete -ns <object_storage_namespace> -bn <bucket_name>
Correct answer: C
Question 2
You have been asked to update the lifecycle policy for object storage using the Oracle Cloud Infrastructure (OCI) Command Line Interface (CLI).
Which command can successfully update the policy?
- oci os object-lifecycle-policy delete -ns <object_storage_namespace> -bn <bucket_name>
- oci os object-lifecycle-policy put -ns <object_storage_namespace> -bn <bucket_name> -Items <json_formated_lifecycle_policy>
- oci os object-lifecycle-policy put -ns <object_storage_namespace> -bn <bucket_name> O
- oci os object-lifecycle-policy get -ns <object_storage_namespace> -bn <bucket_name>
Correct answer: B
Explanation:
To create or replace a lifecycle policy for a bucket Open a command prompt and run oci os object-lifecycle-policy put to create or replace the object lifecycle policy for a bucket. To edit individual rules, replace the bucket's existing policy with a new version of the policy that includes the changes to your rules. oci os object-lifecycle-policy put -ns <object_storage_namespace> -bn<bucket_name> --items <json_formatted_lifecycle_policy> The --items option requires that you provide key-value pair input as valid formatted JSON https://docs.cloud.oracle.com/en-us/iaas/Content/Object/Tasks/usinglifecyclepolicies.htm To create or replace a lifecycle policy for a bucket
Open a command prompt and run oci os object-lifecycle-policy put to create or replace the object lifecycle policy for a bucket. To edit individual rules, replace the bucket's existing policy with a new version of the policy that includes the changes to your rules. oci os object-lifecycle-policy put -ns <object_storage_namespace> -bn<bucket_name> --items <json_formatted_lifecycle_policy> The --items option requires that you provide key-value pair input as valid formatted JSON
https://docs.cloud.oracle.com/en-us/iaas/Content/Object/Tasks/usinglifecyclepolicies.htm
Question 3
You are configuring on alarm In Oracle Cloud Infrastructure (OCI) for a compute instance named vision.
The metric needs to be triggered when the ingress network rate is greater than 1MB.
Which statement will accomplish this?
- NetworksBytesIn[1MB]{resourceDisplayName - "vision"}.rate() > 1
- NetworksBytesIn[1m]{resourceDisplayName - "vision"}.rate() > 1024
- {resourceDisplayName = "vision"}(NetworksBytesIn[lm]).rate() > 1024
- {resourceDisplayName = Hvision"}(NetworksBytesIn[1MB]).rate() > 1
Correct answer: B
Explanation:
NetworkBytesIn is aggregated across all the instance's attached VNICs Example The query components appear in the following order:metric[interval]{dimensionname="dimensionvalue"}.groupingfunction.statistic https://docs.cloud.oracle.com/en-us/iaas/Content/Monitoring/Reference/mql.htm NetworkBytesIn is aggregated across all the instance's attached VNICs Example
The query components appear in the following order:
metric[interval]{dimensionname="dimensionvalue"}.groupingfunction.statistic
https://docs.cloud.oracle.com/en-us/iaas/Content/Monitoring/Reference/mql.htm
Question 4
You are asked to Implement the disaster recovery (DR) and business continuity requirements for Oracle Cloud Infrastructure (OCI) Block Volumes. Two OCI regions being used: a primary/source region and a DR/destination region.
The requirements are:
- There should be a copy of data in the destination region to use If a region-wide disaster occurs in the source region
- Minimize costs
Which of the following design will help you meet these requirements?
- Clone block volumes. Copy block volume clones from source region to destination region at regular intervals.
- Back up block volumes. Use Object Storage lifecycle management to automatically move backup objects to Archive Storage. Copy Archive Storage buckets from source region to destination at regular Intervals.
- Back up block volumes. Copy block volume backups from source region to destination region at regular intervals.
- Clone block volumes. Use Object Storage lifecycle management to automatically move clone object Archive Storage. Copy Archive Storage buckets from source region to destination at regular intervals.
Correct answer: C
Explanation:
You can copy block volume backups between regions using the Console, command line interface (CLI), SDKs,or REST APIs. For steps, see Copying a Volume Backup Between Regions. This capability enhances the following scenarios:Disaster recovery and business continuity: By copying block volume backups to another region at regular intervals, it makes it easier for you to rebuild applications and data in the destination region if a region-wide disaster occurs in the source region. Migration and expansion: You can easily migrate and expand your applications to another region. You can also enable scheduled cross-region automated backups with user defined policies, To copy volume backups between regions, you must have permission to read and copy volume backups in the source region, and permission to create volume backups in the destination region. You can copy block volume backups between regions using the Console, command line interface (CLI), SDKs,or REST APIs. For steps, see Copying a Volume Backup Between Regions. This capability enhances the following scenarios:
Disaster recovery and business continuity: By copying block volume backups to another region at regular intervals, it makes it easier for you to rebuild applications and data in the destination region if a region-wide disaster occurs in the source region.
Migration and expansion: You can easily migrate and expand your applications to another region. You can also enable scheduled cross-region automated backups with user defined policies, To copy volume backups between regions, you must have permission to read and copy volume backups in the source region, and permission to create volume backups in the destination region.
Question 5
A subscriber of on Oracle Cloud Infrastructure (OCI) Notifications service topic complained about not receiving messages from the service.
Which of the following options can help you debug this issue?
- If OCI Notifications service does not receive an acknowledgement from a subscription endpoint, the service tries to redeliver messages for up to two hours. Configure an alarm on the NumberofNotificationFailed metric through the OCI Monitoring service to help debug the issue.
- If OCI Notifications service does not receive an acknowledgement from a subscription endpoint, the service drops the message. Confirm that the subscriber is always online to receive messages to help debug the issue.
- If OCI Notifications service does not receive an acknowledgement from a subscription endpoint, the service tries to redeliver messages for up to one day. Make sure that the subscriber is online at least once a day to help debug the Issue.
- If OCI Notifications service does not receive an acknowledgement from a subscription endpoint, check the NumberofNotificationFailed metric through the OCI Monitoring service for failed messages. Copy these messages to an OCI Object Storage bucket. Make sure the subscriber has the required credentials to access this bucket to help debug the Issue
Correct answer: A
Explanation:
The Oracle Cloud Infrastructure Notifications service broadcasts messages to distributed components through a publish-subscribe pattern, delivering secure, highly reliable, low latency and durable messages for applications hosted on Oracle Cloud Infrastructure and externally. Use Notifications to get notified when event rules are triggered or alarms are breached, or to directly publish a message.If Notifications doesn't receive an acknowledgement from a subscription endpoint, the service tries to redeliver messages for up to two hours. This situation can occur when the endpoint is offline. You can configure an alarm on the NumberOfNotificationFailed metric through the Monitoring service The Oracle Cloud Infrastructure Notifications service broadcasts messages to distributed components through a publish-subscribe pattern, delivering secure, highly reliable, low latency and durable messages for applications hosted on Oracle Cloud Infrastructure and externally. Use Notifications to get notified when event rules are triggered or alarms are breached, or to directly publish a message.
If Notifications doesn't receive an acknowledgement from a subscription endpoint, the service tries to redeliver messages for up to two hours. This situation can occur when the endpoint is offline. You can configure an alarm on the NumberOfNotificationFailed metric through the Monitoring service
Question 6
Your company has restructured its HR departments. As part of this change, you also need to re- organize compartments within Oracle Cloud Infrastructure (OCI) to align them to the company's new organizational structure.
The following change is required:
Comportment Team_x needs to be moved under a new parent compartment, Project_B
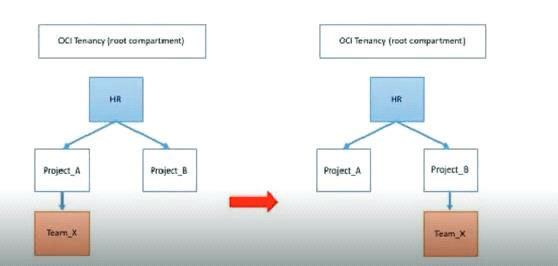
The tenancy has the following policies defined for compartments Project_A and Project_B:Policy1 Allow group G1 to manage instance-family in compartment HR:Project_A Policy2 Allow group G2 to manage instance-family in compartment HR:Project_B
Which two statements describe the impacts after the compartment Team_x is moved?
- Group G2 can now manage instance-families in compartment Project_B compartment Project_A and compartment Team_x
- Group G1 can now manage instance-families in compartment Project_A but not in compartment Team_x
- Group G1 can now manage instance-families in compartment project_A,compartment project_B and compartment Team_x
- Group G2 can now manage instance-families in compartment Project_B and compartment Team_x
- Group G2 can now manage instance-families in compartment Project_A but not in compartment Team_x
Correct answer: BD
Explanation:
Understanding the Policy Implications When You Move a Compartment After you move a compartment to a new parent compartment, the access policies of the new parent take effect and the policies of the previous parent no longer apply. Before you move a compartment, ensure that:You are aware of the policies that govern access to the compartment in its current position. You are aware of the polices in the new parent compartment that will take effect when you move the compartment. Groups with Permissions in the Current Compartment Lose Access; Groups with Permissions in the Destination Compartment Gain Access Understanding the Policy Implications When You Move a Compartment After you move a compartment to a new parent compartment, the access policies of the new parent take effect and the policies of the previous parent no longer apply. Before you move a compartment, ensure that:
- You are aware of the policies that govern access to the compartment in its current position.
- You are aware of the polices in the new parent compartment that will take effect when you move the compartment.
Groups with Permissions in the Current Compartment Lose Access; Groups with Permissions in the Destination Compartment Gain Access
Question 7
What is a key benefit of using Oracle Cloud Infrastructure's Resource Manager for your Terraform provisioning and management activities?
- Resource Manager has administrative privileges by design. Even if your IAM user does not have access,you can leverage Resource Manage provision new resources to any compartment in the Tenancy.
- You can use Resource Manager to identify and maintain an Inventory of all Compute and Database Instances across your tenancy.
- You can use Resource Manager to apply patches to all existing Oracle Linux Instances In a specified compartment.
- Resource Manager manages the Terraform state file for your infrastructure and locks the file so that only one Job at a time can run on a given stack.
Correct answer: D
Explanation:
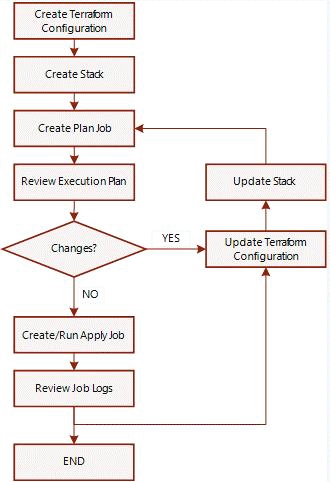
Resource Manager is an Oracle Cloud Infrastructure service that allows you to automate the process of provisioning your Oracle Cloud Infrastructure resources. Using Terraform, Resource Manager helps you install, configure, and manage resources through the "infrastructure-as-code" model. A Terraform configuration codifies your infrastructure in declarative configuration files. Resource Manager allows you to share and manage infrastructure configurations and state files across multiple teams and platforms. This infrastructure management can't be done with local Terraform installations and Oracle Terraform modules alone. JOB: Instructions to perform the actions defined in your configuration. Only one job at a time can run on a given stack; further, you can have only one set of Oracle Cloud Infrastructure resources on a given stack. To provision a different set of resources, you must create a separate stack and use a different configuration. The following image represents a generalized view of the Resource Manager workflow. Resource Manager is an Oracle Cloud Infrastructure service that allows you to automate the process of provisioning your Oracle Cloud Infrastructure resources. Using Terraform, Resource Manager helps you install, configure, and manage resources through the "infrastructure-as-code" model. A Terraform configuration codifies your infrastructure in declarative configuration files. Resource Manager allows you to share and manage infrastructure configurations and state files across multiple teams and platforms. This infrastructure management can't be done with local Terraform installations and Oracle Terraform modules alone.
JOB: Instructions to perform the actions defined in your configuration. Only one job at a time can run on a given stack; further, you can have only one set of Oracle Cloud Infrastructure resources on a given stack. To provision a different set of resources, you must create a separate stack and use a different configuration. The following image represents a generalized view of the Resource Manager workflow.
Question 8
The boot volume on your Oracle Linux instance has run out of space. Your application has crashed due to a lack of swap space, forcing you to Increase the size of the boot volume. Which step should NOT be Included In the process used to solve the Issue?
- Resize the boot volume by specifying a larger value than the boot volume's current size.
- Create a RAID 0 configuration to extend the boot volume file system onto another block volume.
- Attach the resized boot volume to a second instance as a data volume; Extend the partition and grow the file system on the resized boot volume.
- Reattach the boot volume and restart the instance.
- Stop the instance and detach the boot volume.
Correct answer: B
Explanation:
The Oracle Cloud Infrastructure Block Volume service lets you expand the size of block volumes and boot volumes. You have three options to increase the size of your volumes:Expand an existing volume in place with offline resizing. See Resizing a Volume Using the Console for the steps to do this. Restore from a volume backup to a larger volume. See Restoring a Backup to a New Volume and Restoring a Boot Volume. Clone an existing volume to a new, larger volume. See Cloning a Volume and Cloning a Boot Volume . The Oracle Cloud Infrastructure Block Volume service lets you expand the size of block volumes and boot volumes. You have three options to increase the size of your volumes:
- Expand an existing volume in place with offline resizing. See Resizing a Volume Using the Console for the steps to do this.
- Restore from a volume backup to a larger volume. See Restoring a Backup to a New Volume and Restoring a Boot Volume.
- Clone an existing volume to a new, larger volume. See Cloning a Volume and Cloning a Boot Volume .
Question 9
Which three statements are true about Object Storage data security and encryption in Oracle Cloud Infrastructure (OCI)?
- OCI Key Management is used by default to provide data security.
- Server side encryption uses per-object keys which are managed by Oracle.
- All traffic to and from Object Storage service is encrypted using TLS.
- A VPN connection to OCI is required to ensure security data transfer to an object storage bucket.
- Client-side encryption is managed by the customer.
Correct answer: BCE
Explanation:
All data in Object Storage is encrypted at rest by using AES-256. Encryption is on by default and cannot be turned off. Each object is encrypted with its encryption key, and the object encryption keys are encrypted with a master encryption key. In addition, customers can use client-side encryption to encrypt objects with their encryption keys before storing them in Object Storage buckets. An available option for customers is to use the Amazon S3 Compatibility API, along with client-side object encryption support available in AWS SDK for Java.Data in transit between customer clients (for example, SDKs and CLIs) and Object Storage public endpoints is encrypted with TLS 1.2 by default. FastConnect public peering allows on-premises access to Object Storage to go over a private network, rather than the public internet. Oracle Cloud Infrastructure Key Management is a managed service the enables you, the customer, to manage and control AES symmetric keys used to encrypt your data-at-rest. Keys are stored in a FIPS 140-2, Level 3-certified, Hardware Security Module (HSM) that is durable and highly available. The Key Management service is integrated with many Oracle Cloud Infrastructure services, including Block Volumes, File Storage, Oracle Container Engine for Kubernetes, and Object Storage.Use the Key Management service if you need to store your Master Encryption Keys in an HSM to meet governance and regulatory compliance requirements or when you want more control over the cryptoperiod of the encryption keys used for your data. When you store your data with Oracle Cloud Infrastructure Block Volumes, File Storage Service, and Object Storage and don't use Key Management, your data is protected using encryption keys that are securely stored and controlled by Oracle. All data in Object Storage is encrypted at rest by using AES-256. Encryption is on by default and cannot be turned off. Each object is encrypted with its encryption key, and the object encryption keys are encrypted with a master encryption key. In addition, customers can use client-side encryption to encrypt objects with their encryption keys before storing them in Object Storage buckets. An available option for customers is to use the Amazon S3 Compatibility API, along with client-side object encryption support available in AWS SDK for Java.Data in transit between customer clients (for example, SDKs and CLIs) and Object Storage public endpoints is encrypted with TLS 1.2 by default. FastConnect public peering allows on-premises access to Object Storage to go over a private network, rather than the public internet. Oracle Cloud Infrastructure Key Management is a managed service the enables you, the customer, to manage and control AES symmetric keys used to encrypt your data-at-rest. Keys are stored in a FIPS 140-2, Level 3-certified, Hardware Security Module (HSM) that is durable and highly available. The Key Management service is integrated with many Oracle Cloud Infrastructure services, including Block Volumes, File Storage, Oracle Container Engine for Kubernetes, and Object Storage.Use the Key Management service if you need to store your Master Encryption Keys in an HSM to meet governance and regulatory compliance requirements or when you want more control over the cryptoperiod of the encryption keys used for your data. When you store your data with Oracle Cloud Infrastructure Block Volumes, File Storage Service, and Object Storage and don't use Key Management, your data is protected using encryption keys that are securely stored and controlled by Oracle.
Question 10
You set up a bastion host in your VCN to only allow your IP address (140.19.2.140) to establish SSH connections to your Compute instances that are deployed private subnet. The Compute instances have an attached Network Security Group with a Source Type: Network security Group (NSG) , Source NSG: -050504.
To secure the bastion host, you added the following ingress rules to its Network Security Group:
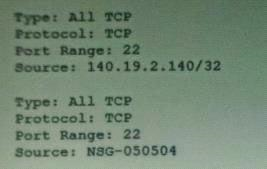
However, after checking the bastion host logs, you discovered that there are IP addresses other than your own that can access your bastion host.
What is the root cause of this issue?
- A netmask of /32 allows all IP address in the 140.19.2.0 network, other than your IP 110.19.2.140
- The port 22 provides unrestricted access to 140.19.2.140 and to other IP address
- Al compute instances associated with NSG-050504 are also able to connect to the bastion host.
- The Security List allows access to all IP address which overrides the Network Security Group ingress rules.
Correct answer: C
Explanation:
As per security rules that allow ssh on port 22 and source will be NSG-050504, so any compute instance that attached to this NSG will able to access the bastion host as it includes in the same NSG As per security rules that allow ssh on port 22 and source will be NSG-050504, so any compute instance that attached to this NSG will able to access the bastion host as it includes in the same NSG
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



