Download Oracle Linux 6 Advanced System Administration.1z0-105.CertKey.2019-02-20.97q.vcex
| Vendor: | Oracle |
| Exam Code: | 1z0-105 |
| Exam Name: | Oracle Linux 6 Advanced System Administration |
| Date: | Feb 20, 2019 |
| File Size: | 1 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Examine the dtrace command:
dtrace -P syscall
Which statement is true about this command?
- It enables all probes available in the syscall provider.
- It lists all probes available in the syscall provider.
- It returns an error. The command is incomplete. You must specify a probe to enable.
- It enables all probes available in the syscall provider, and produces no output.
Correct answer: B
Explanation:
Reference: http://docs.oracle.com/cd/E19253-01/819-5488/gbxwv/index.html (Example 2-7, probes by provider) Reference: http://docs.oracle.com/cd/E19253-01/819-5488/gbxwv/index.html (Example 2-7, probes by provider)
Question 2
Examine this extract from /etc/httpd/conf/httpd.conf for virtual hosts:
<VirtualHost *:80>
ServerAdmin [email protected]
DocumentRoot /www/docs/site1.example.com
ServerName site1.example.com
</VirtualHost>
<VirtualHost *:80>
ServerAdmin [email protected]
DocumentRoot /www/docs/site2.example.com
ServerName site2.example.com
</VirtualHost>
Which three statements are true about the configuration extract?
- To connect to the website, site1.example.com must resolve to a different IP address than site2.example.com.
- site1.example.com and site2.example.com can share the same IP address.
- The web server attempts a DHCP discover to assign one IP address per virtual host.
- It is possible but not mandatory to have unique IP addresses for each virtual host.
- The site1.example.com virtual host shares and error logs with site2.example.com.
Correct answer: ACE
Question 3
Examine the code fragment from /etc/tgt/targets.conf:
<target iqn.2013-03.com.example.mypc:1>
backing-store /iSCSIsharedDisk/physDisk1.img
write-cache off
</target>
<target iqn.2013-03.com.example.myps:2>
backing-store / iSCSIsharedDisk/physDisk2.img
initiator-address 192.0.2.105
initiator address 192.0.2.106
write-cache off
</target>
<target iqn.2013-03.com.example.mypc:3>
backing-store /iSCSIsharedDisk/physDisk3.img
write-cache off
</target>
Which statement is true?
- Only the target identified by the iqn ending with mypc:2 is visible. This target is visible to the specific clients identified by the initiator address.
- The initiator-address syntax in not valid. The address value should be specified as an iqn, not an IP address. This causes an error, and only iqns ending with mypc:1 and mypc:3 are visible.
- All targets are visible to prospective clients, but the target iqn ending with mypc:2 is visible exclusively to the specified IP addresses.
- The initiator-address syntax is not valid. The address value must be specified as an iqn, not an IP address. The initiator-address parameters are ignored and all targets are visible without restriction.
Correct answer: B
Question 4
Which three statements are true about an RPM SPEC file?
- It is mandatory for building a binary RPM using rpmbuild.
- It is a Shell script that can be used to build a binary RPM.
- It contains metadata that will be part of a binary RPM.
- It contains metadata and helper scripts that are required during the build process of a binary RPM.
Correct answer: ABD
Explanation:
Reference: http://www.thegeekstuff.com/2015/02/rpm-build-package-example/? utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+TheGeekStuff+ (The+Geek+Stuff) Reference: http://www.thegeekstuff.com/2015/02/rpm-build-package-example/? utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+TheGeekStuff+ (The+Geek+Stuff)
Question 5
Examine the parameters shown using the sysctl command relating to panic situations:
[root@WAYOUT etc]# sysctl –a |grep panic |grep –v hung
kernel.panic = 0
kernel.panic_on_oops = 0
kernel.softlockup_panic = 0
kernel.unknown_nmi_panic = 0
kernel.panic_on_unrecovered_nmi = 0
kernel.panic_on_io_nmi = 0
kernel.panic_on_oom = 2
[root@WAYOUT etc]# sysctl –a |grep hung
kernel.hung_task_panic = 0
kernel.hung_task_chek_count – 4194304
kernel.hung_task_timeout_secs = 120
kernel.hung_task_warnings = 10
Which two statements are true about system behavior?
- The kernel delays panic for a few seconds if a bug is encountered to allow the klogd kernel logging daemon to log the oops output.
- The kernel panics if a kernel thread sleeps in the TASK_UNINTERRUPTABLE state for more than 120 seconds.
- The kernel attempts to continue if a bug is encountered.
- The kernel always panics if an out-of-memory condition arises.
- The kernel tries to kill some memory-consuming processes to avoid a panic if an out-of- memory condition arises.
- The kernel panics if a user thread sleeps in the TASK_UNINTERRUPTABLE state for more than 120 seconds.
Correct answer: BF
Question 6
Which two options prevent unauthorized access to the named service from the rndc utility on Oracle Linux?
- running rndc-confgen –a to generate a key that can be used by both the named service and the rndc utility
- running rndc-confgen –a to generate a key that can be used only by the named service
- running rndc –k /etc/rndc.key to generate a key to be used only by the rndc utility
- the presence of /etc/named.conf with the line include “/etc/rndc.key”; to allow the named service to check for a matching key from the rndc utility
Correct answer: AD
Explanation:
Reference: http://www.oracle.com/us/technologies/linux/suse-linux-to-oracle-linux-wp- 1898710.pdf (page 49) Reference: http://www.oracle.com/us/technologies/linux/suse-linux-to-oracle-linux-wp- 1898710.pdf (page 49)
Question 7
After creating empty mount point /xfs1, you execute the command:
# mkfs –t xfs –L /xfs1 –l logdev=/dev/sdd1 /dev/sdh1
Which two statements are true about the effects of executing the mkfs command?
- It fails if there is an existing XFS file system on /dev/sdh1.
- It fails if there is an existing XFS log on /dev/sdd1.
- It fails if there is an existing XFS file system on /dev/sdd1.
- It fails because there is no size specified for the XFS log.
- The xfs1 file system is mounted automatically during system startup.
- It creates and mounts the /xfs1 file system.
Correct answer: DF
Question 8
Examine the contents of /etc/mail/access:
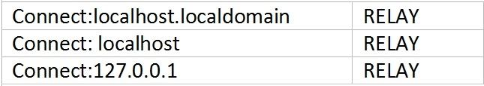
This system is to be used as an MTA or mail gateway for the local LAN network address 192.168.1.0/24.
Which two actions allow this mail host to route email for the network?
- Run sendmail again; and the updated file can be accessed automatically.
- Add this line to /etc/mail/access:

- Add this line to /etc/mail/access:

- Add this line to /etc/mail/access:

- Rebuild the access database file after the source files have been modified. Restarting the sendmail service automatically rebuilds the maps.
Correct answer: DE
Question 9
Which two statements are true about recursive nameservers that are supported by Oracle Linux?
- They may be authoritative.
- They may forward requests to authoritative name servers on some occasions.
- They may be primary nameservers.
- They cache replies from previous name resolution requests.
- They may be secondary nameservers.
Correct answer: BC
Question 10
What is function of the System Security Service Daemon (SSSD)?
- It permits single-user accounts by maintaining credentials for back-end systems on behalf of local users.
- It enables fingerprint reader support for Kerberos clients.
- It enables Smart Card Authentication for Kerberos clients.
- It permits Kerberos authentication to be done offline by caching user identities.
Correct answer: A
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



