Download Security Fundamentals.98-367.PrepAway.2020-12-08.166q.vcex
| Vendor: | Microsoft |
| Exam Code: | 98-367 |
| Exam Name: | Security Fundamentals |
| Date: | Dec 08, 2020 |
| File Size: | 4 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Windows Firewall is a built-in. host-based, stateless firewall.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text makes the statement correct.
- Stateful
- Network layer
- Packet filter
- No change is needed
Correct answer: A
Question 2
Alice sends her password to the game server in plaintext. Chuck is able to observe her password as shown in the following image:
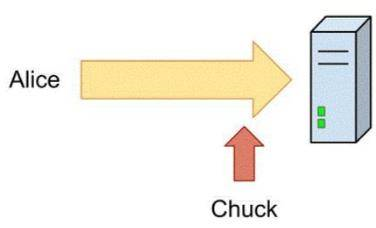
Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Question 3
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Question 4
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Explanation:
Question 5
Bridging is a process of sending packets from source to destination on OSI layer 3.
Select the correct answer if the underlined text does not make the statement correct. Select "No change is needed" if the underlined text makes the statement correct.
- Routing
- Switching
- Repeating
- No change is needed.
Correct answer: A
Question 6
The primary purpose of Network Access Protection (NAP) is to prevent:
- Loss of data from client computers on a network.
- Non-compliant systems from connecting to a network.
- Users on a network from installing software.
- Unauthorized users from accessing a network.
Correct answer: B
Explanation:
NAP enforces health policies by inspecting and assessing the health of client computers, restricting network access when client computers are noncompliant with health policy, and remediating noncompliant client computers to bring them into compliance with health policy before they are granted full network access. NAP enforces health policies on client computers that are attempting to connect to a network; NAP also provides ongoing health compliance enforcement while a client computer is connected to a network. Reference: http://technet.microsoft.com/en-us/library/cc754378(v=ws.10).aspx NAP enforces health policies by inspecting and assessing the health of client computers, restricting network access when client computers are noncompliant with health policy, and remediating noncompliant client computers to bring them into compliance with health policy before they are granted full network access. NAP enforces health policies on client computers that are attempting to connect to a network; NAP also provides ongoing health compliance enforcement while a client computer is connected to a network.
Reference: http://technet.microsoft.com/en-us/library/cc754378(v=ws.10).aspx
Question 7
You want to make your computer resistant to online hackers and malicious software.
What should you do?
- Configure a forward proxy.
- Install anti-virus software.
- Enable spam filtering.
- Turn on Windows Firewall.
Correct answer: B
Question 8
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Correct answer: To work with this question, an Exam Simulator is required.
Question 9
Your company requires that users type a series of characters to access the wireless network.
The series of characters must meet the following requirements:
Contains more than 15 characters
Contains at least one letter
Contains at least one number
Contains at least one symbol
Which security technology meets these requirements?
- WEP
- WPA2 PSK
- WPA2 Enterprise
- MAC filtering
Correct answer: B
Explanation:
Pre-shared key mode (PSK, also known as Personal mode) is designed for home and small office networks that don't require the complexity of an 802.1X authentication server.[9] Each wireless network device encrypts the network traffic using a 256 bit key. This key may be entered either as a string of 64 hexadecimal digits, or as a passphrase of 8 to 63 printable ASCII characters Pre-shared key mode (PSK, also known as Personal mode) is designed for home and small office networks that don't require the complexity of an 802.1X authentication server.[9] Each wireless network device encrypts the network traffic using a 256 bit key. This key may be entered either as a string of 64 hexadecimal digits, or as a passphrase of 8 to 63 printable ASCII characters
Question 10
Many Internet sites that you visit require a user name and password.
How should you secure these passwords?
- Save them to a text file
- Enable session caching
- Configure the browser to save passwords
- Save them to an encrypted file
- Reuse the same password
Correct answer: D
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



