Download Kubernetes and Cloud Native Associate.KCNA.Pass4Success.2026-01-25.64q.vcex
| Vendor: | Linux Foundation |
| Exam Code: | KCNA |
| Exam Name: | Kubernetes and Cloud Native Associate |
| Date: | Jan 25, 2026 |
| File Size: | 4 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
What framework does Kubernetes use to authenticate users with JSON Web Tokens?
- OpenID Connect
- OpenID Container
- OpenID Cluster
- OpenID CNCF
Correct answer: A
Explanation:
Kubernetes commonly authenticates users using OpenID Connect (OIDC) when JSON Web Tokens (JWTs) are involved, so A is correct. OIDC is an identity layer on top of OAuth 2.0 that standardizes how clients obtain identity information and how JWTs are issued and validated.In Kubernetes, authentication happens at the API server. When OIDC is configured, the API server validates incoming bearer tokens (JWTs) by checking token signature and claims against the configured OIDC issuer and client settings. Kubernetes can use OIDC claims (such as sub, email, groups) to map the authenticated identity to Kubernetes RBAC subjects. This is how enterprises integrate clusters with identity providers such as Okta, Dex, Azure AD, or other OIDC-compliant IdPs.Options B, C, and D are fabricated phrases and not real frameworks. Kubernetes documentation explicitly references OIDC as a supported method for token-based user authentication (alongside client certificates, bearer tokens, static token files, and webhook authentication). The key point is that Kubernetes does not ''invent'' JWT auth; it integrates with standard identity providers through OIDC so clusters can participate in centralized SSO and group-based authorization.Operationally, OIDC authentication is typically paired with:RBAC for authorization (''what you can do'')Audit logging for traceabilityShort-lived tokens and rotation practices for securityGroup claim mapping to simplify permission managementSo, the verified framework Kubernetes uses with JWTs for user authentication is OpenID Connect. Kubernetes commonly authenticates users using OpenID Connect (OIDC) when JSON Web Tokens (JWTs) are involved, so A is correct. OIDC is an identity layer on top of OAuth 2.0 that standardizes how clients obtain identity information and how JWTs are issued and validated.
In Kubernetes, authentication happens at the API server. When OIDC is configured, the API server validates incoming bearer tokens (JWTs) by checking token signature and claims against the configured OIDC issuer and client settings. Kubernetes can use OIDC claims (such as sub, email, groups) to map the authenticated identity to Kubernetes RBAC subjects. This is how enterprises integrate clusters with identity providers such as Okta, Dex, Azure AD, or other OIDC-compliant IdPs.
Options B, C, and D are fabricated phrases and not real frameworks. Kubernetes documentation explicitly references OIDC as a supported method for token-based user authentication (alongside client certificates, bearer tokens, static token files, and webhook authentication). The key point is that Kubernetes does not ''invent'' JWT auth; it integrates with standard identity providers through OIDC so clusters can participate in centralized SSO and group-based authorization.
Operationally, OIDC authentication is typically paired with:
RBAC for authorization (''what you can do'')
Audit logging for traceability
Short-lived tokens and rotation practices for security
Group claim mapping to simplify permission management
So, the verified framework Kubernetes uses with JWTs for user authentication is OpenID Connect.
Question 2
To specify a Kubernetes object which language is used?
- JSON
- Go
- YAML
- Node
- Python
Correct answer: C
Explanation:
https://kubernetes.io/docs/concepts/overview/working-with-objects/kubernetes-objects/ https://kubernetes.io/docs/concepts/overview/working-with-objects/kubernetes-objects/

Question 3
Which of the following is used to request storage in Kubernetes?
- PersistentVolume 'PV'
- PersistentVolumeClaim 'PVC'
- Container Storage Interface 'CSI'
- StorageClasses
Correct answer: B
Explanation:
https://kubernetes.io/docs/concepts/storage/persistent-volumes/ https://kubernetes.io/docs/concepts/storage/persistent-volumes/
Question 4
What kind of limitation cgroups allows?
- Prioritization
- Resource limiting
- Accounting
- None of the options
- Control
- Server cpu and memory
Correct answer: A, B, C, E
Question 5
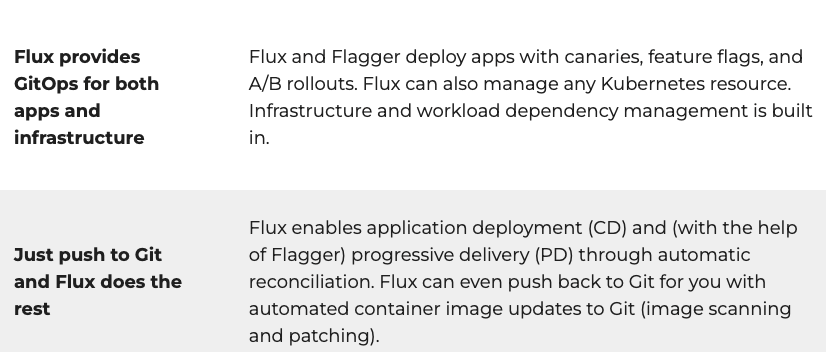
Flux is built using which toolkit?
- CI/CD
- DevSecOps
- GitOps
- DevOps
Correct answer: C
Explanation:
https://fluxcd.io/ https://fluxcd.io/
Question 6
What is Open Container Initiative 'OCI'?
- A protocol for communicating with the kubernetes api
- The governing body of the Cloud Native Computing Foundation 'CNCF'
- An open standard for managing service mesh in kubernetes
- An organization that creates open standards for containers
Correct answer: D
Explanation:
https://opencontainers.org/ https://opencontainers.org/

Question 7
Which style of operations are preferred for kubernetes and cloud-native applications?
- Imperative
- None of the above
- Declarative
Correct answer: C
Explanation:
https://kubernetes.io/docs/tasks/manage-kubernetes-objects/declarative-config/#trade-offs https://kubernetes.io/docs/tasks/manage-kubernetes-objects/declarative-config/#trade-offs
Question 8
Which command is used to expose Kubernetes service
- kubectl expose
- kubectl create
- kubectl run
Correct answer: A
Explanation:
https://kubernetes.io/docs/reference/generated/kubectl/kubectl-commands#expose https://kubernetes.io/docs/reference/generated/kubectl/kubectl-commands#expose

Question 9
How should folks new to the cloud native ecosystem, go about learning the different aspects of the ecosystem?
- by signing up the CNCF slack
- by reading the Kubernetes documentation
- by looking at the cloud native landscape
- by looking at the cloud native trail-map
Correct answer: D
Explanation:
https://github.com/cncf/landscape#trail-map https://github.com/cncf/landscape#trail-map
Question 10
An application that is nearing its usage limit. To increase the amount of users it can handle, you allo-cate additional memory resources to each instance of the application. What type of scaling is this?
- Horizontal Scaling
- Cluster Autoscaling
- Recursive Scaling
- Vertical Scaling
Correct answer: D
Question 11
Which of the following best describes a cloud-native app?
- An application where all logic is coded into a single large binary.
- An application that publishes an HTTPS web front-end.
- An application that takes advantages of cloud computing fromworks and their loosely coupled cloud services.
- An application that leverages services that are native to public cloud platforms such as Azure, GCP, and/or AWS.
Correct answer: C
Explanation:
Cloud-native apps leverage cloud computing frameworks and tend to be microservices based, where individual components of the app are coded as individual. Cloud-native apps leverage cloud computing frameworks and tend to be microservices based, where individual components of the app are coded as individual.
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!




