Download Security, Professional (JNCIP-SEC).JN0-634.PracticeTest.2019-01-28.39q.vcex
| Vendor: | Juniper |
| Exam Code: | JN0-634 |
| Exam Name: | Security, Professional (JNCIP-SEC) |
| Date: | Jan 28, 2019 |
| File Size: | 1 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
You want to review AppTrack statistics to determine the characteristics of the traffic being monitored.
Which operational mode command would accomplish this task on an SRX Series device?
- show services application-identification statistics applications
- show services application-identification application detail
- show security application-tracking counters
- show services security-intelligence statistics
Correct answer: A
Explanation:
Question 2
Which AppSecure feature identifies applications that are present in traffic?
- AppID
- AppTrack
- AppFW
- AppQoS
Correct answer: A
Question 3
What is the correct application mapping sequence when a user goes to Facebook for the first time through an SRX Series device?
- first packet > process packet > check application system cache > classify application > process packet > match and identify application
- first packet > check application system cache > process packet > classify application > match and identify application
- first packet > check application system cache > classify application > process packet > match and identify application
- first packet > process packet > check application system cache > classify application > match and identify application
Correct answer: D
Question 4
You have been notified by your colocation provider that your infrastructure racks will no longer be adjacent to each other.
In this scenario, which technology would you use to secure all Layer 2 and Layer 3 traffic between racks?
- IPsec
- GRE
- 802.1BR
- MACsec
Correct answer: D
Question 5
You need to add all of the sites in the domain example.com to urllist2. You decide to use wildcards to account for any changes made to the domain in the future.
In this scenario, which two commands would you use to meet this requirement? (Choose two.)
- set custom-objects url-pattern urllist2 value http://*.example.com
- set custom-objects url-pattern urllist2 value http://*example.com
- set custom-objects url-pattern urllist2 value http://*.example.???
- set custom-objects url-pattern urllist2 value http://*.example.*
Correct answer: AC
Question 6
What is a function of UTM?
- AppFW
- IPsec
- content filtering
- bridge mode
Correct answer: C
Explanation:
Question 7
You are configuring transparent mode on an SRX Series device. You must permit IP-based traffic only, and BPDUs must be restarted to the VLANs from which they originate.
Which configuration accomplishes these objectives?
- bridge {block-non-ip-all;bpdu-vlan-flooding;}
- bridge {block-non-ip-all;bypass-non-ip-unicast;no-packet-flooding;}
- bridge {bypass-non-ip-unicast;bpdu-vlan-flooding;}
- bridge {block-non-ip-all;bypass-non-ip-unicast;bpdu-vlan-flooding;}
Correct answer: A
Question 8
You have configured a log collector VM and Security Director. System logging is enabled on a branch SRX Series device, but security logs do not appear in the monitor charts.
How would you solve this problem?
- Configure a security policy to forward logs to the collector.
- Configure application identification on the SRX Series device.
- Configure security logging on the SRX Series device.
- Configure J-Flow on the SRX Series device.
Correct answer: C
Question 9
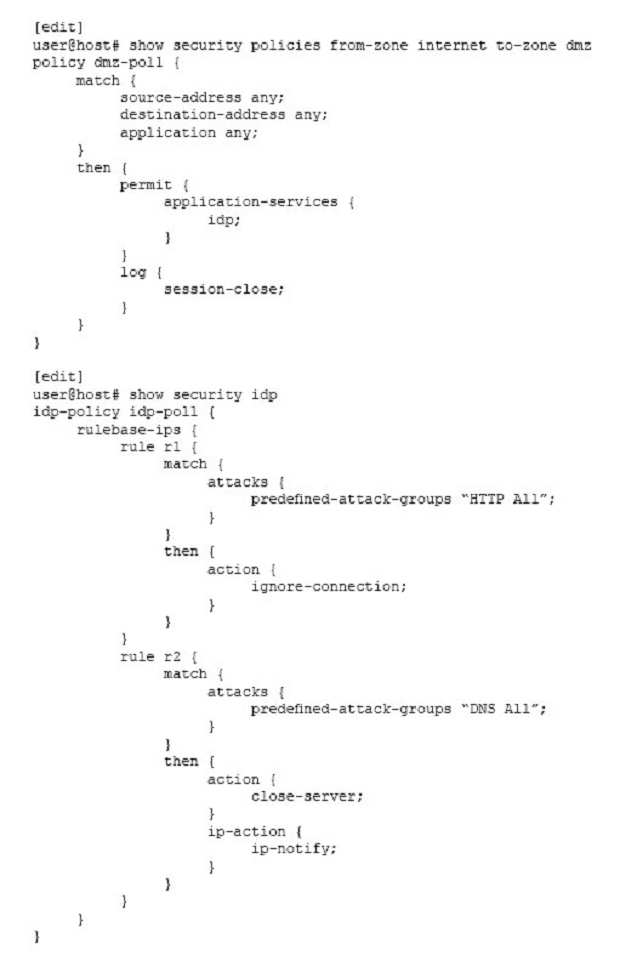
Referring to the configuration shown in the exhibit, which statement explains why traffic matching the IDP signature DNS:OVERFLOW:TOO-LONG-TCP-MSG is not being stopped by the SRX Series device?
- The security policy dmz-pol1 has an action of permit.
- The IDP policy idp-pol1 is not configured as active.
- The IDP rule r2 has an ip-action value of notify.
- The IDP rule r1 has an action of ignore-connection.
Correct answer: B
Question 10
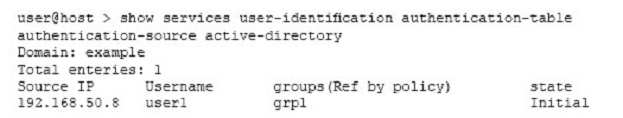
Which statement explains the current state value of the command output shown in the exhibit?
- A valid response was received from a domain PC probe, and the user is a valid domain user programmed in the PFE.
- An invalid response was received from a domain PC probe, and the user is an invalid domain user.
- A probe event generated an entry in the authentication table, but no probe response has been received from the domain PC.
- The user-to-address mapping was successfully read from the domain controller event logs, and an entry was added to the authentication table witch currently resides on the Routing Engine.
Correct answer: A
Explanation:
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



