Download Security, Professional (JNCIP-SEC).JN0-634.CertDumps.2018-07-24.35q.vcex
| Vendor: | Juniper |
| Exam Code: | JN0-634 |
| Exam Name: | Security, Professional (JNCIP-SEC) |
| Date: | Jul 24, 2018 |
| File Size: | 1 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Which Junos security feature is used for signature-based attack prevention?
- RADIUS
- AppQoS
- IPS
- PIM
Correct answer: C
Question 2
Using content filtering on an SRX Series device, which three types of HTTP content are able to be blocked? (Choose three.)
- PDF files
- ZIP files
- Java applets
- Active X
- Flash
Correct answer: BCD
Question 3
After using Security Director to add a new firewall policy rule on an SRX Series device, you notice that the hit count on the policy is not increasing. Upon further investigation, you find that the devices listed in the new rule are able to communicate as expected. Your firewall policy consists of hundreds of rules.
Using only Security Director, how do you find the rule that is allowing the communication to occur in this scenario?
- Generate a Top Firewall Rules report.
- Generate a Policy Analysis report.
- Generate a Top Source IPs report.
- Generate a Top Firewall Events report.
Correct answer: D
Question 4
Your network includes SRX Series devices at the headquarters location. The SRX Series devices at this location are part of a high availability chassis cluster and are configured for IPS. There has been a node failover.
In this scenario, which statement is true?
- Existing sessions continue to be processed by IPS because of table synchronization.
- Existing sessions are no longer processed by IPS and become firewall sessions.
- Existing session continue to be processed by IPS as long as GRES is configured.
- Existing sessions are dropped and must be reestablished so IPS processing can occur.
Correct answer: A
Question 5
You are scanning files that are being transferred from the Internet to hosts on your internal network with Sky ATP. However, you notice that files that are 1 GB in size are not being scanned by Sky ATP.
In this scenario, which two statements are true? (Choose two.)
- The Sky ATP failback option is set to permit.
- The Sky ATP engine or the SRX Series device is too busy.
- The 1 GB file size is larger than the scan size limit for Sky ATP.
- The Sky ATP policy on the SRX Series device is misconfigured.
Correct answer: CD
Question 6
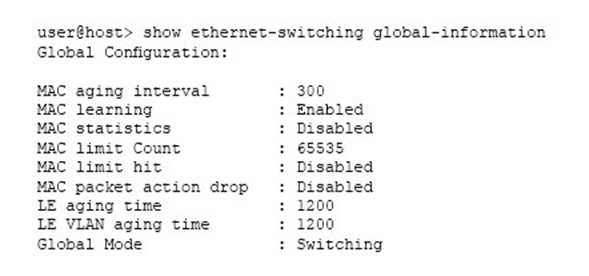
Referring to the exhibit, which two statements are true? (Choose two.)
- You can secure inter-VLAN traffic with a security policy on this device.
- You can secure intra-VLAN traffic with a security policy on this device.
- The device can pass Layer 2 and Layer 3 traffic at the same time.
- The device cannot pass Layer 2 and Layer 3 traffic at the same time.
Correct answer: AC
Question 7
Your network includes SRX Series devices at the headquarters location. The SRX Series devices at this location are part of a high available chassis cluster and are configured for IPS. There has been a node failover.
In this scenario, which two statements are true? (Choose two.)
- The IP action table is synchronized between the chassis cluster nodes.
- Cached SSL session ID information for existing sessions is not synchronized between nodes.
- The IP action table is not synchronized between the chassis cluster nodes.
- Cached SSL session ID information for existing session is synchronized between nodes.
Correct answer: CD
Question 8
While reviewing the Log and Reporting portion of Security Director, you find that multiple objects reference the same address. You want to use a standardized name for all of the objects.
In this scenario, how would you create a standardized object name without searching the entire policy?
- Remove the duplicate objects.
- Merge the duplicate objects.
- Rename the duplicate objects.
- Replace the duplicate objects.
Correct answer: B
Question 9
Which statement about transparent mode on an SRX340 is true?
- You must reboot the device after configuring transparent mode.
- Security policies applied to transparent mode zones require Layer 2 address matching.
- Screens are not supported in transparent mode security zones.
- All interfaces on the device must be configured with the ethernet-switching protocol family.
Correct answer: A
Question 10
A customer has recently deployed a next-generation firewall, sandboxing software, cloud access security brokers (CASB), and endpoint protection.
In this scenario, which tool would provide the customer with additional attack prevention?
- Junos Space Cross Provisioning Platform
- Contrail
- Security Director Policy Enforcer
- Network Director Inventory Manager
Correct answer: C
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



