Download Security, Specialist.JN0-335.ExamTopics.2025-10-14.99q.vcex
| Vendor: | Juniper |
| Exam Code: | JN0-335 |
| Exam Name: | Security, Specialist |
| Date: | Oct 14, 2025 |
| File Size: | 2 MB |
| Downloads: | 1 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Click the Exhibit button.
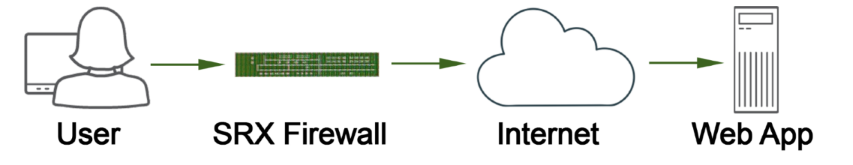
Referring to the exhibit, which two statements describe the type of proxy used? (Choose two.)
- forward proxy
- client protection proxy
- server protection proxy
- reverse proxy
Correct answer: AB
Explanation:
AB: 5 - MostedAC: 2 AB: 5 - MostedAC: 2
Question 2
Which three statements about SRX Series device chassis clusters are true? (Choose three.)
- Chassis cluster control links must be configured using RFC 1918 IP addresses.
- Chassis cluster member devices synchronize configuration using the control link.
- A control link failure causes the secondary cluster node to be disabled.
- Recovery from a control link failure requires that the secondary member device be rebooted.
- Heartbeat messages verify that the chassis cluster control link is working.
Correct answer: BCE
Explanation:
BCE: 2BE: 2 - Mosted BCE: 2BE: 2 - Mosted
Question 3
Which two statements are correct about the fab interface in a chassis cluster? (Choose two.)
- Real-time objects (RTOs) are exchanged on the fab interface to maintain session synchronization.
- In an active/active configuration, inter-chassis transit traffic is sent over the fab interface.
- The fab interface enables configuration synchronization.
- Heartbeat signals sent on the fab interface monitor the health of the control plane link.
Correct answer: AB
Explanation:
AB: 3 - Mosted AB: 3 - Mosted
Question 4
When a security policy is deleted, which statement is correct about the default behavior for active sessions allowed by that policy?
- The active sessions allowed by the policy will be dropped.
- The active sessions allowed by the policy will be marked as a legacy flow and will continue to be forwarded.
- The active sessions allowed by the policy will be reevaluated by the cached policy rules.
- The active sessions allowed by the policy will continue unchanged.
Correct answer: A
Explanation:
A: 6 - MostedB: 2D: 1 A: 6 - MostedB: 2D: 1
Question 5
Which two statements are true about mixing traditional and unified security policies? (Choose two.)
- When a packet matches a unified security policy, the evaluation process terminates.
- Traditional security policies must come before unified security policies.
- Unified security policies must come before traditional security policies.
- When a packet matches a traditional security policy, the evaluation process terminates.
Correct answer: BD
Explanation:
AD: 2BD: 2 - Mosted AD: 2BD: 2 - Mosted
Question 6
Which two features are configurable on Juniper Secure Analytics (JSA) to ensure that alerts are triggered when matching certain criteria? (Choose two.)
- building blocks
- assets
- events
- tests
Correct answer: AC
Explanation:
AC: 4 - MostedAD: 2BC: 1 AC: 4 - MostedAD: 2BC: 1
Question 7
Which two statements are correct about Juniper ATP Cloud? (Choose two.)
- Once the target threshold is met, Juniper ATP Cloud continues looking for threats from 0 to 5 minutes.
- Once the target threshold is met, Juniper ATP Cloud continues looking for threats from 0 to 10 minutes.
- The threat levels range from 0-10.
- The threat levels range from 0-100.
Correct answer: AC
Explanation:
AC: 5 - MostedBC: 1 AC: 5 - MostedBC: 1
Question 8
You are experiencing excessive packet loss on one of your two WAN links, each link coming from a different provider. You want to automatically route traffic from the degraded link to the working link.
Which AppSecure component would you use to accomplish this task?
- AppFW
- AppQoE
- AppQoS
- APBR
Correct answer: B
Explanation:
B: 4 - MostedD: 3 B: 4 - MostedD: 3
Question 9
Which statement defines the function of an Application Layer Gateway (ALG)?
- The ALG uses software processes for permitting or disallowing specific IP address ranges.
- The ALG uses software that is used by a single TCP session using the same port numbers as the application.
- The ALG contains protocols that use one application session for each TCP session.
- The ALG uses software processes for managing specific protocols.
Correct answer: D
Explanation:
D: 6 - Mosted D: 6 - Mosted
Question 10
Which two statements are correct when considering IPS rule base evaluation? (Choose two.)
- IPS evaluates rules concurrently.
- IPS applies the most severe action to traffic matching multiple rules.
- IPS evaluates rules sequentially.
- IPS applies the least severe action to traffic matching multiple rules.
Correct answer: BC
Explanation:
BC: 7 - Mosted BC: 7 - Mosted
Question 11
How does the SSL proxy detect if encryption is being used?
- It uses application identity services.
- It verifies the length of the packet.
- It queries the client device.
- It looks at the destination port number.
Correct answer: A
Explanation:
A: 4 - Mosted A: 4 - Mosted
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!




