Download Security, Specialist.JN0-335.CertDumps.2023-07-07.65q.vcex
| Vendor: | Juniper |
| Exam Code: | JN0-335 |
| Exam Name: | Security, Specialist |
| Date: | Jul 07, 2023 |
| File Size: | 5 MB |
| Downloads: | 3 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Regarding static attack object groups, which two statements are true? (Choose two.)
- Matching attack objects are automatically added to a custom group.
- Group membership automatically changes when Juniper updates the IPS signature database.
- Group membership does not automatically change when Juniper updates the IPS signature database.
- You must manually add matching attack objects to a custom group.
Correct answer: BC
Explanation:
static attack object groups are predefined groups of attack objects that are included in Juniper’s IPS signature database. These groups do not change automatically when Juniper updates the database2. static attack object groups are predefined groups of attack objects that are included in Juniper’s IPS signature database. These groups do not change automatically when Juniper updates the database2.
Question 2
You are deploying a new SRX Series device and you need to log denied traffic.
In this scenario, which two policy parameters are required to accomplish this task? (Choose two.)
- session-init
- session-close
- deny
- count
Correct answer: BC
Explanation:
you need to create a global firewall rulebase that matches RT_FLOW_SESSION_DENY events2. To do this, you need to specify two policy parameters: deny and session-close3. you need to create a global firewall rulebase that matches RT_FLOW_SESSION_DENY events2. To do this, you need to specify two policy parameters: deny and session-close3.
Question 3
You are asked to reduce the load that the JIMS server places on your Which action should you take in this situation?
- Connect JIMS to the RADIUS server
- Connect JIMS to the domain Exchange server
- Connect JIMS to the domain SQL server.
- Connect JIMS to another SRX Series device.
Correct answer: D
Explanation:
JIMS server is a Juniper Identity Management Service that collects user identity information from different authentication sources for SRX Series devices12. It can connect to SRX Series devices and CSO platform in your network1. JIMS server is a service that protects corporate resources by authenticating and restricting user access based on roles2. It connects to SRX Series devices and CSO platform to provide identity information for firewall policies1. To reduce the load that JIMS server places on your network, you should connect JIMS to another SRX Series device1. This way, you can distribute the identity information among multiple SRX Series devices and reduce network traffic. JIMS server is a Juniper Identity Management Service that collects user identity information from different authentication sources for SRX Series devices12. It can connect to SRX Series devices and CSO platform in your network1.
JIMS server is a service that protects corporate resources by authenticating and restricting user access based on roles2. It connects to SRX Series devices and CSO platform to provide identity information for firewall policies1. To reduce the load that JIMS server places on your network, you should connect JIMS to another SRX Series device1. This way, you can distribute the identity information among multiple SRX Series devices and reduce network traffic.
Question 4
Which two statements about unified security policies are correct? (Choose two.)
- Unified security policies require an advanced feature license.
- Unified security policies are evaluated after global security policies.
- Traffic can initially match multiple unified security policies.
- APPID results are used to determine the final security policy
Correct answer: CD
Explanation:
unified security policies are security policies that enable you to use dynamic applications as match conditions along with existing 5-tuple or 6-tuple matching conditions12. They simplify applicationbased security policy management at Layer 7 and provide greater control and extensibility to manage dynamic applications traffic3 unified security policies are security policies that enable you to use dynamic applications as match conditions along with existing 5-tuple or 6-tuple matching conditions12. They simplify applicationbased security policy management at Layer 7 and provide greater control and extensibility to manage dynamic applications traffic3
Question 5
Exhibit
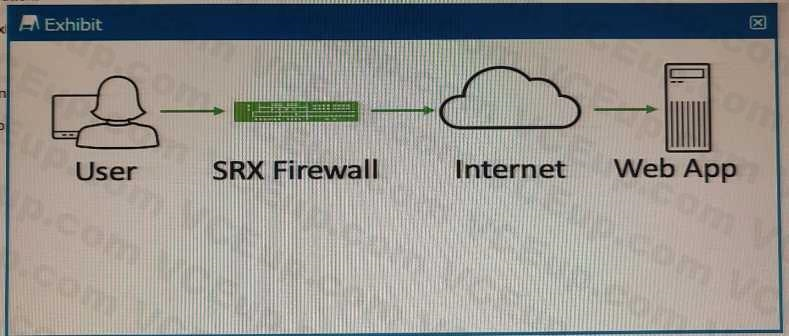
Referring to the exhibit, which two statements describe the type of proxy used? (Choose two.)
- forward proxy
- client protection proxy
- server protection proxy
- reverse proxy
Correct answer: BC
Explanation:
1. Client protection proxy: This statement is correct because a forward proxy can also be called a client protection proxy since it protects the user’s identity and computer information from the web server4. 2. Server protection proxy: This statement is correct because a reverse proxy can also be called a server protection proxy since it protects the web server’s identity and location from the user4. 1. Client protection proxy: This statement is correct because a forward proxy can also be called a client protection proxy since it protects the user’s identity and computer information from the web server4.
2. Server protection proxy: This statement is correct because a reverse proxy can also be called a server protection proxy since it protects the web server’s identity and location from the user4.
Question 6
You have deployed an SRX300 Series device and determined that files have stopped being scanned.
In this scenario, what is a reason for this problem?
- The software license is a free model and only scans executable type files.
- The infected host communicated with a command-and-control server, but it did not download malware.
- The file is too small to have a virus.
- You have exceeded the maximum files submission for your SRX platform size.
Correct answer: D
Explanation:
You have exceeded the maximum files submission for your SRX platform size: This statement is correct because file scanning on SRX300 Series device has a limit on the number of files that can be submitted per minute based on the platform size3. For example, SRX320 has a limit of 10 files per minute3. You have exceeded the maximum files submission for your SRX platform size: This statement is correct because file scanning on SRX300 Series device has a limit on the number of files that can be submitted per minute based on the platform size3. For example, SRX320 has a limit of 10 files per minute3.
Question 7
Which three statements about SRX Series device chassis clusters are true? (Choose three.)
- Chassis cluster control links must be configured using RFC 1918 IP addresses.
- Chassis cluster member devices synchronize configuration using the control link.
- A control link failure causes the secondary cluster node to be disabled.
- Recovery from a control link failure requires that the secondary member device be rebooted.
- Heartbeat messages verify that the chassis cluster control link is working.
Correct answer: BCE
Explanation:
1. Chassis cluster member devices synchronize configuration using the control link: This statement is correct because the control link is used for configuration synchronization among other functions. 2. A control link failure causes the secondary cluster node to be disabled: This statement is correct because a control link failure causes the secondary node to become ineligible for primary role and remain in secondary role until the control link is restored. 3. Heartbeat messages verify that the chassis cluster control link is working: This statement is correct because heartbeat messages are sent periodically over the control link to monitor its status. 1. Chassis cluster member devices synchronize configuration using the control link: This statement is correct because the control link is used for configuration synchronization among other functions.
2. A control link failure causes the secondary cluster node to be disabled: This statement is correct because a control link failure causes the secondary node to become ineligible for primary role and remain in secondary role until the control link is restored.
3. Heartbeat messages verify that the chassis cluster control link is working: This statement is correct because heartbeat messages are sent periodically over the control link to monitor its status.
Question 8
Which two statements are correct about security policy changes when using the policy rematch feature? (Choose two.)
- When a policy change includes changing the policy's action from permit to deny, all existing sessions are maintained
- When a policy change includes changing the policy's source or destination address match condition, all existing sessions are dropped.
- When a policy change includes changing the policy's action from permit to deny, all existing sessions are dropped.
- When a policy change includes changing the policy's source or destination address match condition, all existing sessions are reevaluated.
Correct answer: CD
Explanation:
policy rematch is a feature that enables the device to reevaluate an active session when its associated security policy is modified. The session remains open if it still matches the policy that allowed the session initially. The session is closed if its associated policy is renamed, deactivated, or deleted1. policy rematch is a feature that enables the device to reevaluate an active session when its associated security policy is modified. The session remains open if it still matches the policy that allowed the session initially. The session is closed if its associated policy is renamed, deactivated, or deleted1.
Question 9
You are asked to block malicious applications regardless of the port number being used.
In this scenario, which two application security features should be used? (Choose two.)
- AppFW
- AppQoE
- APPID
- AppTrack
Correct answer: AC
Explanation:
you can block applications and users based on network access policies, users and their job roles, time, and application signatures2. You can also use Juniper Advanced Threat Prevention (ATP) to find and block commodity and zero-day cyberthreats within files, IP traffic, and DNS requests1 you can block applications and users based on network access policies, users and their job roles, time, and application signatures2. You can also use Juniper Advanced Threat Prevention (ATP) to find and block commodity and zero-day cyberthreats within files, IP traffic, and DNS requests1
Question 10
A client has attempted communication with a known command-and-control server and it has reached the configured threat level threshold.
Which feed will the clients IP address be automatically added to in this situation?
- the command-and-control cloud feed
- the allowlist and blocklist feed
- the custom cloud feed
- the infected host cloud feed
Correct answer: D
Explanation:
Infected hosts are internal hosts that have been compromised by malware and are communicating with external C&C servers3. Juniper ATP Cloud provides infected host feeds that list internal IP addresses or subnets of infected hosts along with a threat level3. Once the Juniper ATP Cloud global threshold for an infected host is met, that host is added to the infected host feed and assigned a threat level of 10 by the cloud4. You can also configure your SRX Series device to block traffic from these IP addresses using security policies4. Infected hosts are internal hosts that have been compromised by malware and are communicating with external C&C servers3. Juniper ATP Cloud provides infected host feeds that list internal IP addresses or subnets of infected hosts along with a threat level3. Once the Juniper ATP Cloud global threshold for an infected host is met, that host is added to the infected host feed and assigned a threat level of 10 by the cloud4. You can also configure your SRX Series device to block traffic from these IP addresses using security policies4.
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



