Download Data Center-Associate.JN0-280.VCEplus.2024-10-29.32q.vcex
| Vendor: | Juniper |
| Exam Code: | JN0-280 |
| Exam Name: | Data Center-Associate |
| Date: | Oct 29, 2024 |
| File Size: | 197 KB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Which statement is correct about member interfaces when creating a LAG?
- The interface's MTU settings must match on all member interfaces.
- The interface's duplex settings and link speed must be the same on all member interfaces.
- Member interfaces must all be allocated on the same chassis when using a Virtual Chassis.
- Member interfaces must all be allocated on the same PFE.
Correct answer: B
Explanation:
When creating a LAG (Link Aggregation Group) in Junos, the duplex settings and link speed must be the same across all member interfaces.Step-by-Step Breakdown:LAG Overview:A LAG combines multiple physical interfaces into a single logical interface to increase bandwidth and provide redundancy. All member links must act as a single cohesive unit.Interface Requirements:Duplex: All member interfaces must operate in the same duplex mode (either full-duplex or half-duplex). Mismatched duplex settings can cause performance issues, packet drops, or interface errors.Link Speed: All interfaces in the LAG must have the same link speed (e.g., all interfaces must be 1 Gbps or 10 Gbps). Mismatched speeds would prevent the interfaces from functioning correctly within the LAG.Configuration and Validation: Ensure that all member interfaces have identical settings before adding them to the LAG. These settings can be checked using the show interfaces command, and the LAG can be configured using:set interfaces ae0 aggregated-ether-options link-speed 10gset interfaces ge-0/0/1 ether-options 802.3ad ae0JuniperReference:LAG Configuration: Duplex and link speed must be consistent across member interfaces to ensure proper LAG operation in Juniper devices. When creating a LAG (Link Aggregation Group) in Junos, the duplex settings and link speed must be the same across all member interfaces.
Step-by-Step Breakdown:
LAG Overview:
A LAG combines multiple physical interfaces into a single logical interface to increase bandwidth and provide redundancy. All member links must act as a single cohesive unit.
Interface Requirements:
Duplex: All member interfaces must operate in the same duplex mode (either full-duplex or half-duplex). Mismatched duplex settings can cause performance issues, packet drops, or interface errors.
Link Speed: All interfaces in the LAG must have the same link speed (e.g., all interfaces must be 1 Gbps or 10 Gbps). Mismatched speeds would prevent the interfaces from functioning correctly within the LAG.
Configuration and Validation: Ensure that all member interfaces have identical settings before adding them to the LAG. These settings can be checked using the show interfaces command, and the LAG can be configured using:
set interfaces ae0 aggregated-ether-options link-speed 10g
set interfaces ge-0/0/1 ether-options 802.3ad ae0
Juniper
Reference:
LAG Configuration: Duplex and link speed must be consistent across member interfaces to ensure proper LAG operation in Juniper devices.
Question 2
Which three actions are required to implement filter-based forwarding? (Choose three.)
- You must create an instance-type forwarding routing instance.
- You must create an instance-type vrf routing instance.
- You must create a match filter.
- You must create a security policy.
- You must create a RIB group.
Correct answer: ACE
Explanation:
Filter-Based Forwarding (FBF) in Junos OS allows traffic to be routed based on specific criteria such as source address, rather than just the destination address. This is useful in scenarios like policy routing or providing multiple paths for different types of traffic.Step-by-Step Breakdown:Instance-Type Forwarding:You must create an instance-type forwarding routing instance. This routing instance allows for different routing tables based on the incoming packet filter.Command:set routing-instances FBF-instance instance-type forwardingMatch Filter:You need to create a filter to match the traffic that will be forwarded according to your custom routing policy. This filter is applied to an interface to determine which traffic will use the custom forwarding instance.Command Example:set firewall family inet filter FBF-filter term 1 from source-addressset firewall family inet filter FBF-filter term 1 then routing-instance FBF-instanceRIB Group:A RIB (Routing Information Base) group is necessary to share routes between the primary routing table and the custom routing instance. This allows FBF traffic to use the routing information from other routing tables.Command Example:set routing-options rib-groups FBF-group import-rib inet.0set routing-instances FBF-instance routing-options rib-group FBF-groupJuniperReference:FBF Configuration: Filter-based forwarding requires these specific steps to redirect traffic to a custom routing table based on filter criteria. Filter-Based Forwarding (FBF) in Junos OS allows traffic to be routed based on specific criteria such as source address, rather than just the destination address. This is useful in scenarios like policy routing or providing multiple paths for different types of traffic.
Step-by-Step Breakdown:
Instance-Type Forwarding:
You must create an instance-type forwarding routing instance. This routing instance allows for different routing tables based on the incoming packet filter.
Command:
set routing-instances FBF-instance instance-type forwarding
Match Filter:
You need to create a filter to match the traffic that will be forwarded according to your custom routing policy. This filter is applied to an interface to determine which traffic will use the custom forwarding instance.
Command Example:
set firewall family inet filter FBF-filter term 1 from source-address
set firewall family inet filter FBF-filter term 1 then routing-instance FBF-instance
RIB Group:
A RIB (Routing Information Base) group is necessary to share routes between the primary routing table and the custom routing instance. This allows FBF traffic to use the routing information from other routing tables.
Command Example:
set routing-options rib-groups FBF-group import-rib inet.0
set routing-instances FBF-instance routing-options rib-group FBF-group
Juniper
Reference:
FBF Configuration: Filter-based forwarding requires these specific steps to redirect traffic to a custom routing table based on filter criteria.
Question 3
Which signaling protocol is used for EVPN?
- OSPF
- PIM
- IS-IS
- BGP
Correct answer: D
Explanation:
EVPN (Ethernet Virtual Private Network) is a standard protocol used for building Layer 2 and Layer 3 VPNs over an IP or MPLS network. The signaling protocol used for EVPN is BGP (Border Gateway Protocol).Step-by-Step Breakdown:BGP as the EVPN Signaling Protocol:EVPN uses BGP to exchange MAC address reachability information between routers (PE devices). This enables devices to learn which MAC addresses are reachable through which PE devices, facilitating Layer 2 forwarding across an IP or MPLS core.BGP Extensions for EVPN:BGP is extended with new address families (e.g., EVPN NLRI) to carry both MAC and IP address information, allowing for scalable and efficient multi-tenant network solutions.JuniperReference:Junos EVPN Configuration: Juniper uses BGP as the control plane for EVPN to exchange MAC and IP route information between different data center devices. EVPN (Ethernet Virtual Private Network) is a standard protocol used for building Layer 2 and Layer 3 VPNs over an IP or MPLS network. The signaling protocol used for EVPN is BGP (Border Gateway Protocol).
Step-by-Step Breakdown:
BGP as the EVPN Signaling Protocol:
EVPN uses BGP to exchange MAC address reachability information between routers (PE devices). This enables devices to learn which MAC addresses are reachable through which PE devices, facilitating Layer 2 forwarding across an IP or MPLS core.
BGP Extensions for EVPN:
BGP is extended with new address families (e.g., EVPN NLRI) to carry both MAC and IP address information, allowing for scalable and efficient multi-tenant network solutions.
Juniper
Reference:
Junos EVPN Configuration: Juniper uses BGP as the control plane for EVPN to exchange MAC and IP route information between different data center devices.
Question 4
Which operation mode command will display the mapping between the VLAN ID and ports on a switch?
- show route
- show ethernet-switching table
- show interfaces terse
- show vlans
Correct answer: D
Explanation:
To display the mapping between VLAN IDs and ports on a Juniper switch, the show vlans command is used.Step-by-Step Breakdown:VLAN Information:The show vlans command displays detailed information about VLAN configurations, including the VLAN ID, associated interfaces (ports), and VLAN membership.Command Example:show vlansThis command will provide an output listing each VLAN, its ID, and the interfaces associated with the VLAN, enabling network engineers to quickly verify VLAN to port mappings.JuniperReference:VLAN Verification: Use the show vlans command to verify which VLANs are configured on the switch and the ports that are members of those VLANs. To display the mapping between VLAN IDs and ports on a Juniper switch, the show vlans command is used.
Step-by-Step Breakdown:
VLAN Information:
The show vlans command displays detailed information about VLAN configurations, including the VLAN ID, associated interfaces (ports), and VLAN membership.
Command Example:
show vlans
This command will provide an output listing each VLAN, its ID, and the interfaces associated with the VLAN, enabling network engineers to quickly verify VLAN to port mappings.
Juniper
Reference:
VLAN Verification: Use the show vlans command to verify which VLANs are configured on the switch and the ports that are members of those VLANs.
Question 5
Exhibit:
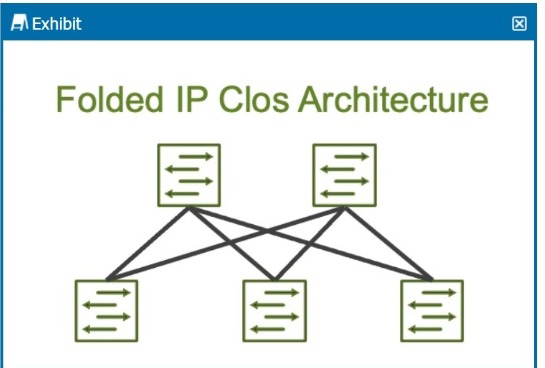
How many stages are shown in the exhibit?
- 2
- 5
- 6
- 3
Correct answer: D
Explanation:
The exhibit shows a Folded IP Clos Architecture, which is also referred to as a 3-stage Clos network design. This architecture typically consists of two layers of switches:Spine Layer: The top row of switches.Leaf Layer: The bottom row of switches.Step-by-Step Breakdown:Clos Architecture:A 3-stage Clos network has two types of devices: spine and leaf. In this design, each leaf switch connects to every spine switch, providing a high level of redundancy and load balancing.Stage Explanation:Stage 1: The first set of leaf switches.Stage 2: The spine switches.Stage 3: The second set of leaf switches.The Folded Clos architecture shown here effectively 'folds' the 3-stage design by combining the ingress and egress leaf layers into one, reducing it to two visible layers, but still maintaining the overall 3-stage architecture.JuniperReference:IP Clos Architecture: The 3-stage Clos design is commonly used in modern data centers for high availability, redundancy, and scalability. The exhibit shows a Folded IP Clos Architecture, which is also referred to as a 3-stage Clos network design. This architecture typically consists of two layers of switches:
Spine Layer: The top row of switches.
Leaf Layer: The bottom row of switches.
Step-by-Step Breakdown:
Clos Architecture:
A 3-stage Clos network has two types of devices: spine and leaf. In this design, each leaf switch connects to every spine switch, providing a high level of redundancy and load balancing.
Stage Explanation:
Stage 1: The first set of leaf switches.
Stage 2: The spine switches.
Stage 3: The second set of leaf switches.
The Folded Clos architecture shown here effectively 'folds' the 3-stage design by combining the ingress and egress leaf layers into one, reducing it to two visible layers, but still maintaining the overall 3-stage architecture.
Juniper
Reference:
IP Clos Architecture: The 3-stage Clos design is commonly used in modern data centers for high availability, redundancy, and scalability.
Question 6
Exhibit:
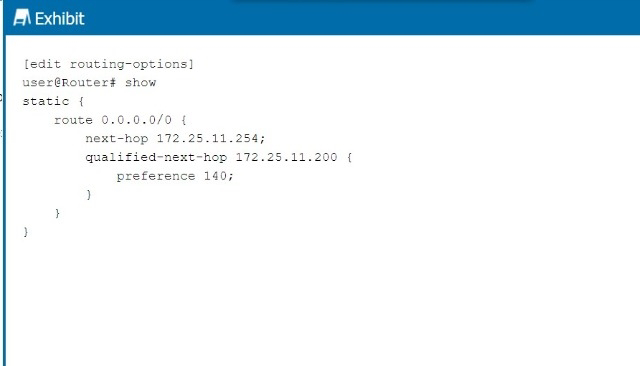
Referring to the exhibit, what is the route preference of the 172.25.11.254 next hop?
- 5
- 10
- 130
- 140
Correct answer: A
Explanation:
In the exhibit, we see two next-hop addresses for the default static route (0.0.0.0/0):The first next hop is 172.25.11.254, with no specified preference.The second next hop is 172.25.11.200, with a specified preference of 140.Step-by-Step Breakdown:Default Static Route Preference:If no preference is explicitly set for a next hop in Junos, it defaults to 5 for static routes.Determining Preference:In this case, the next hop 172.25.11.254 does not have an explicit preference defined, so it will use the default value of 5. The second next hop has a preference of 140, which is higher, meaning it will only be used if the primary next hop is unavailable.JuniperReference:Static Route Preference: In Junos, the default preference for static routes is 5, and this value is applied unless overridden by the preference parameter. In the exhibit, we see two next-hop addresses for the default static route (0.0.0.0/0):
The first next hop is 172.25.11.254, with no specified preference.
The second next hop is 172.25.11.200, with a specified preference of 140.
Step-by-Step Breakdown:
Default Static Route Preference:
If no preference is explicitly set for a next hop in Junos, it defaults to 5 for static routes.
Determining Preference:
In this case, the next hop 172.25.11.254 does not have an explicit preference defined, so it will use the default value of 5. The second next hop has a preference of 140, which is higher, meaning it will only be used if the primary next hop is unavailable.
Juniper
Reference:
Static Route Preference: In Junos, the default preference for static routes is 5, and this value is applied unless overridden by the preference parameter.
Question 7
When considering bidirectional forwarding detection, which two statements are correct? (Choose two.)
- The BFD default minimum interval is 3.
- You can configure BFD per interface within the protocol stanza.
- The BFD operation always consists of minimum intervals and multipliers.
- The BFD default multiplier is 5.
Correct answer: BC
Explanation:
Bidirectional Forwarding Detection (BFD) is a protocol used to detect faults in the forwarding path between two routers. It provides rapid failure detection, enhancing the performance of routing protocols like OSPF, BGP, and IS-IS.Step-by-Step Breakdown:Per Interface Configuration:BFD can be configured on a per-interface basis within the protocol stanza (e.g., OSPF, BGP). This allows granular control over where BFD is enabled and the failure detection intervals for specific interfaces.Minimum Interval and Multiplier:BFD uses a minimum interval (the time between BFD control packets) and a multiplier (the number of missed packets before the path is declared down). The combination of these two defines the detection time for failures.JuniperReference:BFD Configuration: In Juniper, BFD is configurable within routing protocol stanzas, with the failure detection mechanism always based on minimum intervals and multipliers. Bidirectional Forwarding Detection (BFD) is a protocol used to detect faults in the forwarding path between two routers. It provides rapid failure detection, enhancing the performance of routing protocols like OSPF, BGP, and IS-IS.
Step-by-Step Breakdown:
Per Interface Configuration:
BFD can be configured on a per-interface basis within the protocol stanza (e.g., OSPF, BGP). This allows granular control over where BFD is enabled and the failure detection intervals for specific interfaces.
Minimum Interval and Multiplier:
BFD uses a minimum interval (the time between BFD control packets) and a multiplier (the number of missed packets before the path is declared down). The combination of these two defines the detection time for failures.
Juniper
Reference:
BFD Configuration: In Juniper, BFD is configurable within routing protocol stanzas, with the failure detection mechanism always based on minimum intervals and multipliers.
Question 8
How does OSPF calculate the best path to a particular prefix?
- It finds the path with the numerically lowest cost.
- It finds the path with the shortest autonomous system path.
- It finds the path with the least number of hops.
- It finds the path with the numerically lowest route preference.
Correct answer: A
Explanation:
OSPF (Open Shortest Path First) calculates the best path based on the cost of the route, which is derived from the bandwidth of the interfaces along the path.Step-by-Step Breakdown:OSPF Path Selection:OSPF assigns a cost to each link, typically based on the link's bandwidth (higher bandwidth equals lower cost).The OSPF algorithm computes the shortest path to a destination by adding the costs of all links in the path. The path with the numerically lowest total cost is chosen as the best path.Cost Calculation:The OSPF cost can be manually adjusted or automatically calculated using the default formula:Cost=ReferenceBandwidthLinkBandwidth\text{Cost} = \frac{\text{Reference Bandwidth}}{\text{Link Bandwidth}}Cost=LinkBandwidthReferenceBandwidthJuniperReference:OSPF Best Path Selection: OSPF selects the path with the lowest cumulative cost, ensuring efficient use of higher-bandwidth links in Junos networks. OSPF (Open Shortest Path First) calculates the best path based on the cost of the route, which is derived from the bandwidth of the interfaces along the path.
Step-by-Step Breakdown:
OSPF Path Selection:
OSPF assigns a cost to each link, typically based on the link's bandwidth (higher bandwidth equals lower cost).
The OSPF algorithm computes the shortest path to a destination by adding the costs of all links in the path. The path with the numerically lowest total cost is chosen as the best path.
Cost Calculation:
The OSPF cost can be manually adjusted or automatically calculated using the default formula:
Cost=ReferenceBandwidthLinkBandwidth\text{Cost} = \frac{\text{Reference Bandwidth}}{\text{Link Bandwidth}}Cost=LinkBandwidthReferenceBandwidth
Juniper
Reference:
OSPF Best Path Selection: OSPF selects the path with the lowest cumulative cost, ensuring efficient use of higher-bandwidth links in Junos networks.
Question 9
Which state in the adjacency process do OSPF routers check the MTU size?
- Init
- Exchange
- Done
- ExStart
Correct answer: B
Explanation:
In OSPF, routers exchange link-state information in different stages to establish full adjacency. The MTU size is checked during the Exchange state.Step-by-Step Breakdown:OSPF Adjacency Process:OSPF routers go through multiple stages when forming an adjacency: Down, Init, 2-Way, ExStart, Exchange, Loading, and Full.Exchange State:During the Exchange state, OSPF routers exchange Database Description (DBD) packets to describe their link-state databases. The MTU size is checked at this stage to ensure both routers can successfully exchange these packets without fragmentation.If there is an MTU mismatch, the routers may fail to proceed past the Exchange state.JuniperReference:MTU Checking in OSPF: Junos uses the Exchange state to check for MTU mismatches, ensuring that routers can properly exchange database information without packet fragmentation issues. In OSPF, routers exchange link-state information in different stages to establish full adjacency. The MTU size is checked during the Exchange state.
Step-by-Step Breakdown:
OSPF Adjacency Process:
OSPF routers go through multiple stages when forming an adjacency: Down, Init, 2-Way, ExStart, Exchange, Loading, and Full.
Exchange State:
During the Exchange state, OSPF routers exchange Database Description (DBD) packets to describe their link-state databases. The MTU size is checked at this stage to ensure both routers can successfully exchange these packets without fragmentation.
If there is an MTU mismatch, the routers may fail to proceed past the Exchange state.
Juniper
Reference:
MTU Checking in OSPF: Junos uses the Exchange state to check for MTU mismatches, ensuring that routers can properly exchange database information without packet fragmentation issues.
Question 10
Leaf and spine data centers are used to better accommodate which type of traffic?
- north-east
- east-west
- north-west
- south-east
Correct answer: B
Explanation:
In modern data centers, the shift toward leaf-spine architectures is driven by the need to handle increased east-west traffic, which is traffic between servers within the same data center. Unlike traditional hierarchical data center designs, where most traffic was 'north-south' (between users and servers), modern applications often involve server-to-server communication (east-west) to enable services like distributed databases, microservices, and virtualized workloads. Leaf-Spine Architecture:Leaf Layer: This layer consists of switches that connect directly to servers or end-host devices. These switches serve as the access layer.Spine Layer: The spine layer comprises high-performance switches that provide interconnectivity between leaf switches. Each leaf switch connects to every spine switch, creating a non-blocking fabric that optimizes traffic flow within the data center.East-West Traffic Accommodation:In traditional three-tier architectures (core, aggregation, access), traffic had to traverse multiple layers, leading to bottlenecks when servers communicated with each other. Leaf-spine architectures address this by creating multiple equal-cost paths between leaf switches and the spine. Since each leaf switch connects directly to every spine switch, the architecture facilitates quick, low-latency communication between servers, which is essential for east-west traffic flows.Juniper's Role:Juniper Networks provides a range of solutions that optimize for east-west traffic in a leaf-spine architecture, notably through:QFX Series Switches: Juniper's QFX series switches are designed for the leaf and spine architecture, delivering high throughput, low latency, and scalability to accommodate the traffic demands of modern data centers.EVPN-VXLAN: Juniper uses EVPN-VXLAN to create a scalable Layer 2 and Layer 3 overlay network across the data center. This overlay helps enhance east-west traffic performance by enabling network segmentation and workload mobility across the entire fabric.Key Features That Support East-West Traffic:Equal-Cost Multipath (ECMP): ECMP enables the use of multiple paths between leaf and spine switches, balancing the traffic and preventing any one path from becoming a bottleneck. This is crucial in handling the high volume of east-west traffic.Low Latency: Spine switches are typically high-performance devices that minimize the delay between leaf switches, which improves the efficiency of server-to-server communications.Scalability: As the demand for east-west traffic grows, adding more leaf and spine switches is straightforward, maintaining consistent performance without redesigning the entire network.In summary, the leaf-spine architecture is primarily designed to handle the increase in east-west traffic within data centers, and Juniper provides robust solutions to enable this architecture through its switch platforms and software solutions like EVPN-VXLAN. In modern data centers, the shift toward leaf-spine architectures is driven by the need to handle increased east-west traffic, which is traffic between servers within the same data center. Unlike traditional hierarchical data center designs, where most traffic was 'north-south' (between users and servers), modern applications often involve server-to-server communication (east-west) to enable services like distributed databases, microservices, and virtualized workloads. Leaf-Spine Architecture:
Leaf Layer: This layer consists of switches that connect directly to servers or end-host devices. These switches serve as the access layer.
Spine Layer: The spine layer comprises high-performance switches that provide interconnectivity between leaf switches. Each leaf switch connects to every spine switch, creating a non-blocking fabric that optimizes traffic flow within the data center.
East-West Traffic Accommodation:
In traditional three-tier architectures (core, aggregation, access), traffic had to traverse multiple layers, leading to bottlenecks when servers communicated with each other. Leaf-spine architectures address this by creating multiple equal-cost paths between leaf switches and the spine. Since each leaf switch connects directly to every spine switch, the architecture facilitates quick, low-latency communication between servers, which is essential for east-west traffic flows.
Juniper's Role:
Juniper Networks provides a range of solutions that optimize for east-west traffic in a leaf-spine architecture, notably through:
QFX Series Switches: Juniper's QFX series switches are designed for the leaf and spine architecture, delivering high throughput, low latency, and scalability to accommodate the traffic demands of modern data centers.
EVPN-VXLAN: Juniper uses EVPN-VXLAN to create a scalable Layer 2 and Layer 3 overlay network across the data center. This overlay helps enhance east-west traffic performance by enabling network segmentation and workload mobility across the entire fabric.
Key Features That Support East-West Traffic:
Equal-Cost Multipath (ECMP): ECMP enables the use of multiple paths between leaf and spine switches, balancing the traffic and preventing any one path from becoming a bottleneck. This is crucial in handling the high volume of east-west traffic.
Low Latency: Spine switches are typically high-performance devices that minimize the delay between leaf switches, which improves the efficiency of server-to-server communications.
Scalability: As the demand for east-west traffic grows, adding more leaf and spine switches is straightforward, maintaining consistent performance without redesigning the entire network.
In summary, the leaf-spine architecture is primarily designed to handle the increase in east-west traffic within data centers, and Juniper provides robust solutions to enable this architecture through its switch platforms and software solutions like EVPN-VXLAN.
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



