Download Security, Specialist (JNCIS-SEC).JN0-230.ActualTests.2021-07-08.65q.vcex
| Vendor: | Juniper |
| Exam Code: | JN0-230 |
| Exam Name: | Security, Specialist (JNCIS-SEC) |
| Date: | Jul 08, 2021 |
| File Size: | 257 KB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Which statement is correct about Junos security zones?
- User-defined security zones must contain at least one interface.
- Logical interfaces are added to user-defined security zones.
- Security policies are referenced within a user-defined security zone.
- User-defined security zones must contain the key word “zone”.
Correct answer: A
Question 2
Which type of traffic is analyzed by an SRX Series device configured to use an antispam UTM policy?
- IMAP
- POP3
- SMTP
- HTTP
Correct answer: C
Question 3
What is the definition of a zone on an SRX Series device?
- a collection of one or more network segments sharing similar security requirements
- an individual logical interface with a public IP address
- a collection of one or more network segments with different security requirements
- an individual logical interface with a private IP address
Correct answer: A
Question 4
Click the Exhibit button.
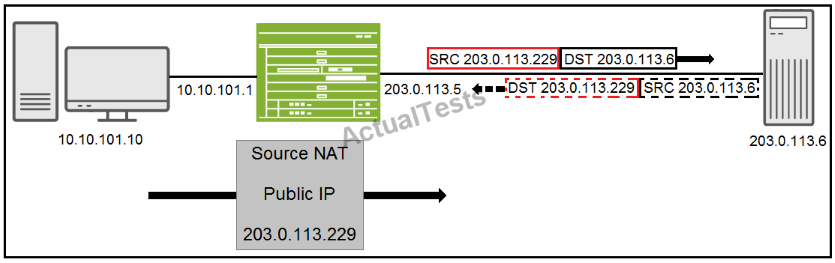
You have configured source NAT using an address pool as shown in the exhibit.
Traffic is reaching the 203.0.113.6 server but return traffic is not being received by the SRX Series device.
Which feature must be configured to allow return traffic to be accepted by the SRX Series device?
- proxy ARP
- destination NAT
- port forwarding
- reverse static NAT
Correct answer: B
Question 5
Your company uses SRX Series devices to secure the edge of the network. You are asked to protect the company from ransomware attacks.
Which solution will satisfy this requirement?
- screens
- unified security policies
- AppSecure
- Sky ATP
Correct answer: D
Question 6
Which method do VPNs use to prevent outside parties from viewing packets in clear text?
- integrity
- authentication
- encryption
- NAT-T
Correct answer: C
Question 7
What is the correct order of processing when configuring NAT rules and security policies?
- destination NAT > policy lookup > source NAT > static NAT
- policy lookup > source NAT > static NAT > destination NAT
- source NAT > static NAT > destination NAT > policy lookup
- static NAT > destination NAT > policy lookup > source NAT
Correct answer: D
Question 8
Which two statements describe IPsec VPNs? (Choose two.)
- IPsec VPN traffic is always authenticated.
- IPsec VPNs are dedicated physical connections between two private networks.
- IPsec VPN traffic is always encrypted.
- IPsec VPNs use security measures to secure traffic over a public network between two remote sites.
Correct answer: AD
Question 9
Which zone is considered a functional zone?
- junos host
- null
- trust
- management
Correct answer: B
Question 10
What does IPsec use to negotiate encryption algorithms?
- AH
- TLS
- IKE
- ESP
Correct answer: C
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



