Download Implementing Aruba WLAN (IAW) 8.HPE6-A42.Pass4Sure.2019-05-21.63q.vcex
| Vendor: | HP |
| Exam Code: | HPE6-A42 |
| Exam Name: | Implementing Aruba WLAN (IAW) 8 |
| Date: | May 21, 2019 |
| File Size: | 2 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
A company has an Aruba solution. The company wants to host a guest login portal with this solution, and the login portal must gie guests the option to create their own login accounts.
How can a network administrator help meet these criteria?
- Choose the Internal captive portal with email registration option for the guest WLAN.
- Make sure to create a guest provisioning account for the guest WLAN.
- Disable authentication in the captive portal profile for the guest WLAN.
- Choose ClearPass or the other external captive portal option for the guest WLAN.
Correct answer: D
Question 2
A network administrator needs to configure firewall rules for three roles:
- Finance
- Sales
- Employee
Several rules apply to both the Employee and Sales roles, but not to the Finance role. What is the simplest way to configure these rules?
- Define the Employee and Sales roles as internal roles, and then configure the rules as global rules for internal users.
- Apply these rules as a subnet-based policy, and then ensure that only Employee and Sales users are assigned IP addresses in that subnet.
- Select either the Employee or Sales role, and then configure these rules within the global policy.
- Create a policy with these rules, and then apply that policy to the Employee and Sales roles.
Correct answer: D
Question 3
An Aruba Mobility Master (MM)-based solution has a WLAN that uses WPA2-Enterprise security. A test login on a wireless client fails.
How can a network administrator determine whether the RADIUS server rejected the credentials or another issue occurred?
- View Technical Support information for the MM.
- Ping the IP address configured as the RADIUS server.
- Use the MM AAA Server Test Diagnostic tool.
- Use the tools in the MM Dashboard > Security window.
Correct answer: C
Question 4
What does an Aruba Mobility Master (MM) do before it deploys a configuration to a Mobility Controller (MC)?
- It encrypts the configuration to be deployed and backs it up to a secure archive.
- It obtains the current configuration, encrypts it, and backs it up to a secure archive.
- It synchronizes the configuration with templates on Aruba AirWave.
- It removes any commands that are not supported on that MC or have dependency errors.
Correct answer: C
Question 5
Refer to the exhibit.

The exhibit shows output from a Mobility Master (MM) dashboard. What does the health status indicate?
- It takes the AP about twice as long to send data to the client as expected if all transmissions succeeded.
- About half of the heartbeats the client sends reaches the Mobility Manager (MM).
- The maximum data rate that 802.11ac supports is about twice as high as the data rate the client uses.
- The client device only complies with about half of the rules in the endpoint health policy.
Correct answer: A
Question 6
A network administrator creates the role employees and adds the rule to it:
user any any permit
The first several wireless clients assigned to the employees role are assigned IP addresses in the 10.10.10.0/24 subnet. Several other wireless clients with the employees role are then assigned IP addresses in the 10.10.20.0/24.
When the Aruba firewall mathces traffic from these clients to the user any any permit rule, what does it do?
- It drops traffic from wireless clients in both the 10.10.0/24 subnet and 10.10.20.0/24 subnet.
- It permits traffic from wireless clients in both the 10.10.10.0/24 and 10.10.20.0/24 subnet as long as the packet has a source IP.
- It permits the traffic from wireless clients in the 10.10.20.0/24 subnet, but drops the traffic from wireless clients in the 10.10.10.0/24 subnet.
- It permits the traffic from wireless clients in the 10.10.0/24 subnet, but drops the traffic from wireless clients in the 10.10.20.0/24 subnet.
Correct answer: B
Question 7
A company has an Aruba solution. A network administrator wants to prevent wireless users from accessing shopping web sites with a bad reputation.
What should thee administrator set up to deny such traffic?
- an AppRF engine
- application filters in the Traffic Analysis dashboard
- firewall access control rules that specify HTTP and HTTPS services
- firewall application rules
Correct answer: C
Question 8
Refer to the exhibits.
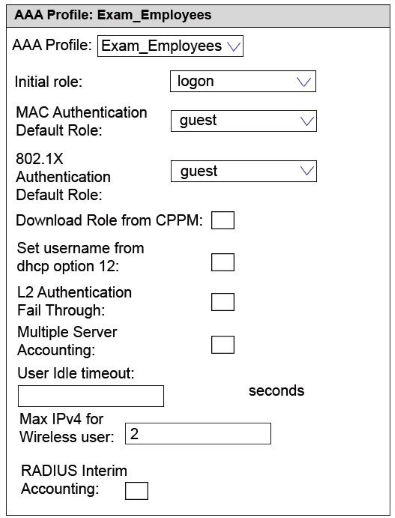

An Aruba solution supports a WLAN that uses WPA2-Enterprise security. Exhibit 1 shows the AAA policy for the WLAN. Users are supposed to be assigned to different roles after authentication. Network administrators test a connection with the employee user account. Exhibit 2 shows the status for the client after this test.
What is a possible reason for the issue shown in Exhibit 2?
- The shared key configured for the ClearPass server is incorrect.
- The RADIUS server is not correctly set up to send a user role for the employee account.
- MAC authentication is enabled on the WLAN, and the test device does not have an authorized address.
- The administrators entered the wrong password for the employee account.
Correct answer: B
Question 9
A company has a single Aruba Mobility Master (MM)-based solution with two Mobility Controllers (MCs). Network administrators want APs in building 1 to support a WLAN but do not want APs in building 2 to support the WLAN.
How can administrator ensure that they can enforce this rule as they set up the WLAN in the Mobility Master (MM) Interface?
- Place APs in different buildings in different AP Groups.
- Assign APs in different buildings to different MM nodes.
- Configure APs in differnet buildings to use different frequency bands.
- Assign different radio profiles to APs in different buidings.
Correct answer: A
Question 10
What is one difference between captive portal authentication and 802.1X authentication?
- 802.1X authentication always authenticates the wireless client, while captive portal authentication always authenticates the wireless user.
- 802.1X authentication occurs at Layer 2, while captive portal authentication occurs at Layer 3.
- 802.1X authentication must use an LDAP server, while captive portal authentication can use a RADIUS server or an LDAP server.
- 802.1X authentication is typically implemented without encryption, while captive authentication is often combined with WPA or WPA2.
Correct answer: A
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



