Download Fortinet NSE4 - FortiOS 6.0.NSE4_FGT-6.0.Pass4Sure.2019-05-02.63q.vcex
| Vendor: | Fortinet |
| Exam Code: | NSE4_FGT-6.0 |
| Exam Name: | Fortinet NSE4 - FortiOS 6.0 |
| Date: | May 02, 2019 |
| File Size: | 3 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Which statement about FortiGuard services for FortiGate is true?
- The web filtering database is downloaded locally on FortiGate.
- Antivirus signatures are downloaded locally on FortiGate.
- FortiGate downloads IPS updates using UDP port 53 or 8888.
- FortiAnalyzer can be configured as a local FDN to provide antivirus and IPS updates.
Correct answer: B
Question 2
Which of the following route attributes must be equal for static routes to be eligible for equal cost multipath (ECMP) routing? (Choose two.)
- Priority
- Metric
- Distance
- Cost
Correct answer: AC
Question 3
View the exhibit.
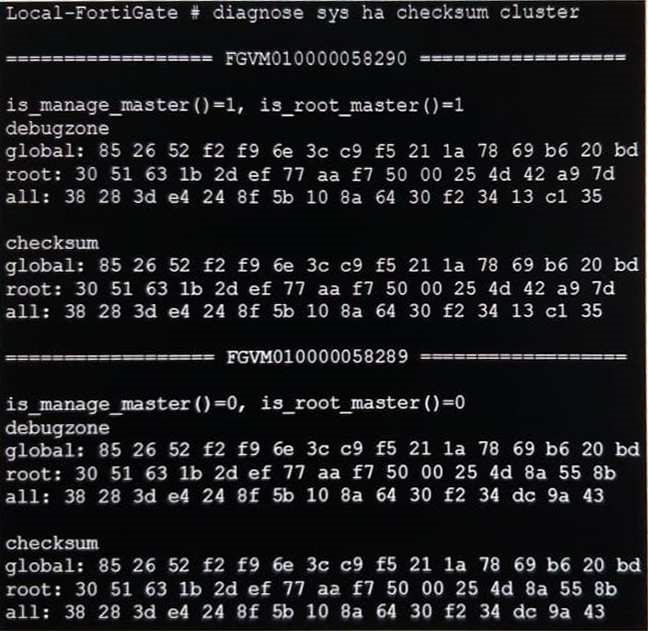
Based on this output, which statements are correct? (Choose two.)
- The all VDOM is not synchronized between the primary and secondary FortiGate devices.
- The root VDOM is not synchronized between the primary and secondary FortiGate devices.
- The global configuration is synchronized between the primary and secondary FortiGate devices.
- The FortiGate devices have three VDOMs.
Correct answer: BC
Question 4
Which statement is true regarding the policy ID number of a firewall policy?
- Defines the order in which rules are processed.
- Represents the number of objects used in the firewall policy.
- Required to modify a firewall policy using the CLI.
- Changes when firewall policies are reordered.
Correct answer: C
Question 5
An administrator wants to block HTTP uploads. Examine the exhibit, which contains the proxy address created for that purpose.
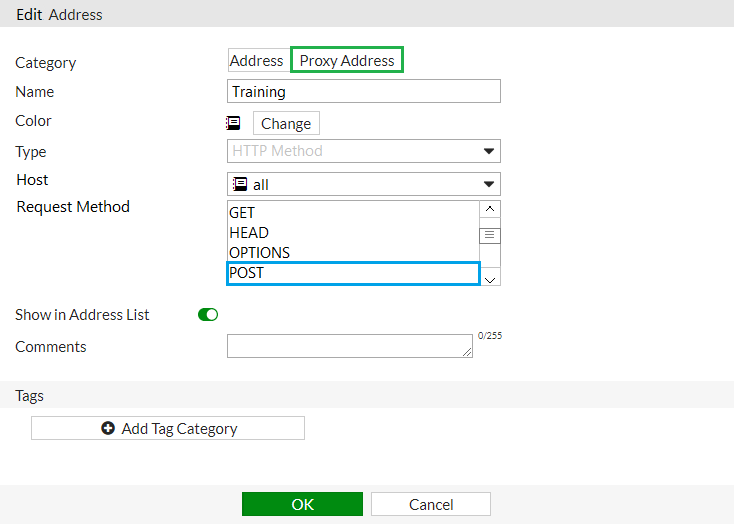
Where must the proxy address be used?
- As the source in a firewall policy.
- As the source in a proxy policy.
- As the destination in a firewall policy.
- As the destination in a proxy policy.
Correct answer: B
Question 6
Which statement is true regarding SSL VPN timers? (Choose two.)
- Allow to mitigate DoS attacks from partial HTTP requests.
- SSL VPN settings do not have customizable timers.
- Disconnect idle SSL VPN users when a firewall policy authentication timeout occurs.
- Prevent SSL VPN users from being logged out because of high network latency.
Correct answer: AD
Question 7
Which of the following conditions must be met in order for a web browser to trust a web server certificate signed by a third-party CA?
- The public key of the web server certificate must be installed on the browser.
- The web-server certificate must be installed on the browser.
- The CA certificate that signed the web-server certificate must be installed on the browser.
- The private key of the CA certificate that signed the browser certificate must be installed on the browser.
Correct answer: C
Question 8
When using SD-WAN, how do you configure the next-hop gateway address for a member interface so that FortiGate can forward Internet traffic?
- It must be configured in a static route using the sdwan virtual interface.
- It must be provided in the SD-WAN member interface configuration.
- It must be configured in a policy-route using the sdwan virtual interface.
- It must be learned automatically through a dynamic routing protocol.
Correct answer: A
Question 9
Which of the following services can be inspected by the DLP profile? (Choose three.)
- NFS
- FTP
- IMAP
- CIFS
- HTTP-POST
Correct answer: BCE
Question 10
Which of the following statements describe WMI polling mode for the FSSO collector agent? (Choose two.)
- The NetSessionEnum function is used to track user logoffs.
- WMI polling can increase bandwidth usage in large networks.
- The collector agent uses a Windows API to query DCs for user logins.
- The collector agent do not need to search any security event logs.
Correct answer: BC
Explanation:
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



