Download Fortinet NSE4 - FortiOS 6.0.NSE4_FGT-6.0.NewDumps.2020-01-28.127q.vcex
| Vendor: | Fortinet |
| Exam Code: | NSE4_FGT-6.0 |
| Exam Name: | Fortinet NSE4 - FortiOS 6.0 |
| Date: | Jan 28, 2020 |
| File Size: | 10 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
You are configuring the root FortiGate to implement the security fabric. You are configuring port10 to communicate with a downstream FortiGate. View the default Edit Interface in the exhibit below:
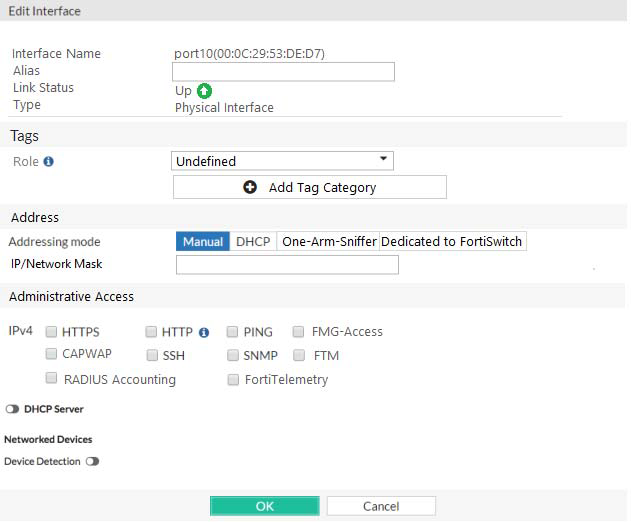
When configuring the root FortiGate to communicate with a downstream FortiGate, which settings are required to be configured? (Choose two.)
- Device detection enabled.
- Administrative Access: FortiTelemetry.
- IP/Network Mask.
- Role: Security Fabric.
Correct answer: BC
Question 2
When browsing to an internal web server using a web-mode SSL VPN bookmark, which IP address is used as the source of the HTTP request?
- remote user’s public IP address
- The public IP address of the FortiGate device.
- The remote user’s virtual IP address.
- The internal IP address of the FotiGate device.
Correct answer: D
Question 3
Examine this output from a debug flow:
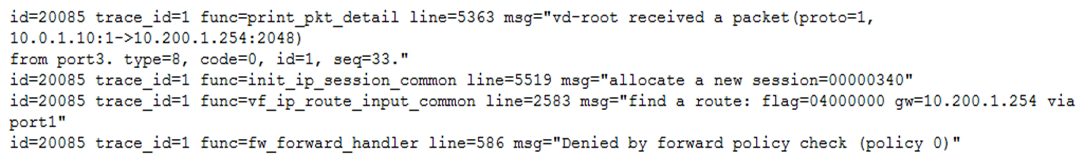
Why did the FortiGate drop the packet?
- The next-hop IP address is unreachable.
- It failed the RPF check.
- It matched an explicitly configured firewall policy with the action DENY.
- It matched the default implicit firewall policy.
Correct answer: D
Question 4
Examine the exhibit, which shows the output of a web filtering real time debug.
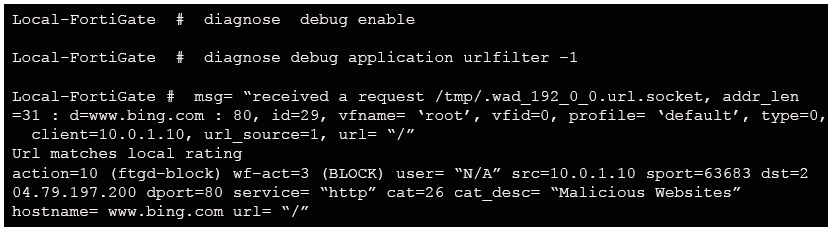
Why is the site www.bing.com being blocked?
- The web site www.bing.com is categorized by FortiGuard as Malicious Websites.
- The user has not authenticated with the FortiGate yet.
- The web server IP address 204.79.197.200 is categorized by FortiGuard as Malicious Websites.
- The rating for the web site www.bing.com has been locally overridden to a category that is being blocked.
Correct answer: D
Question 5
View the exhibit:
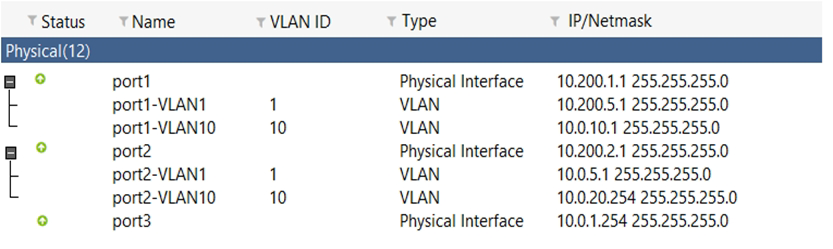
Which statement about the exhibit is true? (Choose two.)
- Broadcast traffic received in port1-VLAN10 will not be forwarded to port2-VLAN10.
- port-VLAN1 is the native VLAN for the port1 physical interface.
- port1-VLAN10 and port2-VLAN10 can be assigned to different VDOMs.
- Traffic between port1-VLAN1 and port2-VLAN1 is allowed by default.
Correct answer: AC
Question 6
Which of the following statements about backing up logs from the CLI and downloading logs from the GUI are true? (Choose two.)
- Log downloads from the GUI are limited to the current log filter view
- Log backups from the CLI cannot be restored to another FortiGate.
- Log backups from the CLI can be configured to upload to FTP at a scheduled time
- Log downloads from the GUI are stored as LZ4 compressed files.
Correct answer: AB
Question 7
Examine the network diagram shown in the exhibit, then answer the following question:
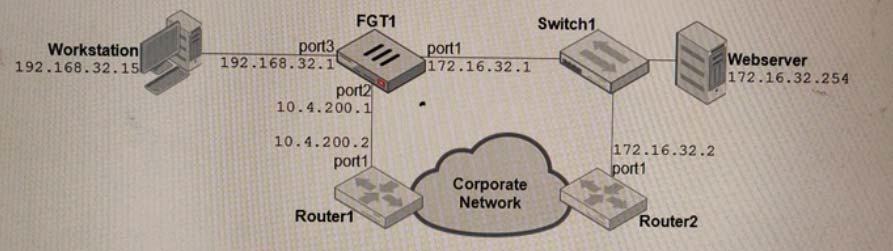
Which one of the following routes is the best candidate route for FGT1 to route traffic from the Workstation to the Web server?
Correct answer: D
Question 8
A team manager has decided that while some members of the team need access to particular website, the majority of the team does not.
Which configuration option is the most effective option to support this request?
- Implement a web filter category override for the specified website.
- Implement web filter authentication for the specified website
- Implement web filter quotas for the specified website.
- Implement DNS filter for the specified website.
Correct answer: B
Question 9
Examine this output from a debug flow:
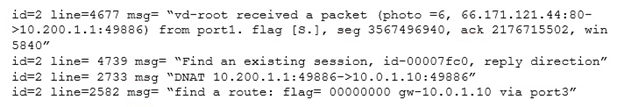
Which statements about the output are correct? (Choose two.)
- FortiGate received a TCP SYN/ACK packet.
- The source IP address of the packet was translated to 10.0.1.10.
- FortiGate routed the packet through port 3.
- The packet was allowed by the firewall policy with the ID 00007fc0.
Correct answer: AC
Question 10
Examine this FortiGate configuration:
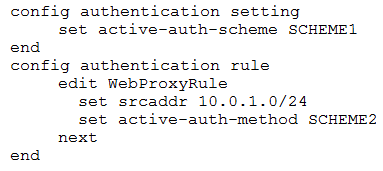
How does the FortiGate handle web proxy traffic coming from the IP address 10.2.1.200 that requires authorization?
- It always authorizes the traffic without requiring authentication.
- It drops the traffic.
- It authenticates the traffic using the authentication scheme SCHEME2.
- It authenticates the traffic using the authentication scheme SCHEME1.
Correct answer: D
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!







