Download Fortinet NSE4 - FortiOS 6.0.NSE4_FGT-6.0.CertKiller.2019-12-05.75q.vcex
| Vendor: | Fortinet |
| Exam Code: | NSE4_FGT-6.0 |
| Exam Name: | Fortinet NSE4 - FortiOS 6.0 |
| Date: | Dec 05, 2019 |
| File Size: | 4 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
What files are sent to FortiSandbox for inspection in flow-based inspection mode?
- All suspicious files that do not have their hash value in the FortiGuard antivirus signature database.
- All suspicious files that are above the defined oversize limit value in the protocol options.
- All suspicious files that match patterns defined in the antivirus profile.
- All suspicious files that are allowed to be submitted to FortiSandbox in the antivirus profile.
Correct answer: C
Question 2
Which statements about a One-to-One IP pool are true? (Choose two.)
- It is used for destination NAT.
- It allows the fixed mapping of an internal address range to an external address range.
- It does not use port address translation.
- It allows the configuration of ARP replies.
Correct answer: CD
Question 3
An administrator is investigating a report of users having intermittent issues with browsing the web. The administrator ran diagnostics and received the output shown in the exhibit.
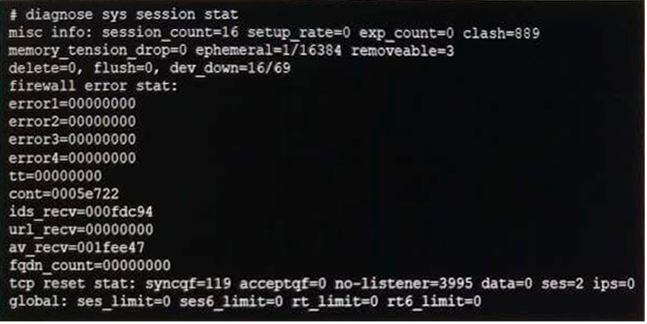
Examine the diagnostic output shown exhibit. Which of the following options is the most likely cause of this issue?
- NAT port exhaustion
- High CPU usage
- High memory usage
- High session timeout value
Correct answer: A
Question 4
Which of the following route attributes must be equal for static routes to be eligible for equal cost multipath (ECMP) routing? (Choose two.)
- Priority
- Metric
- Distance
- Cost
Correct answer: AC
Question 5
View the exhibit.
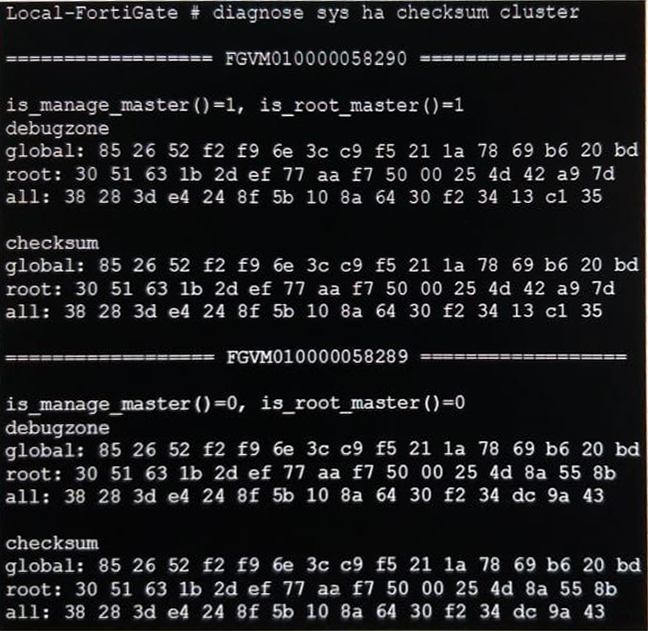
Based on this output, which statements are correct? (Choose two.)
- The all VDOM is not synchronized between the primary and secondary FortiGate devices.
- The root VDOM is not synchronized between the primary and secondary FortiGate devices.
- The global configuration is synchronized between the primary and secondary FortiGate devices.
- The FortiGate devices have three VDOMs.
Correct answer: BC
Question 6
An administrator wants to block HTTP uploads. Examine the exhibit, which contains the proxy address created for that purpose.
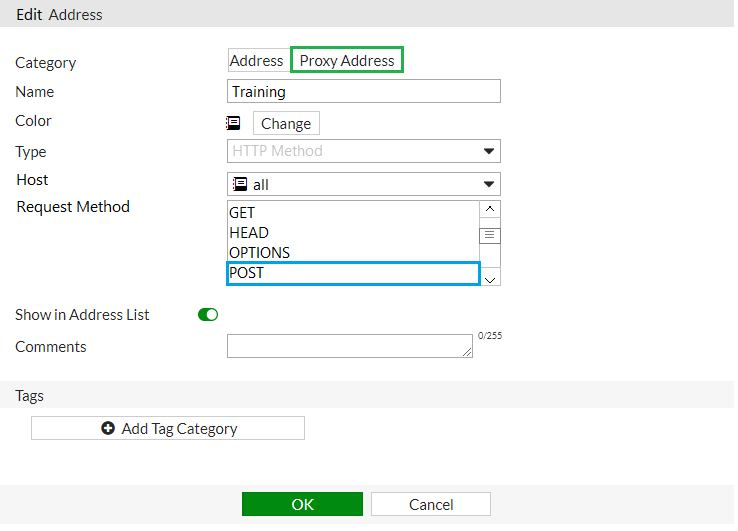
Where must the proxy address be used?
- As the source in a firewall policy.
- As the source in a proxy policy.
- As the destination in a firewall policy.
- As the destination in a proxy policy.
Correct answer: B
Question 7
Which statement is true regarding SSL VPN timers? (Choose two.)
- Allow to mitigate DoS attacks from partial HTTP requests.
- SSL VPN settings do not have customizable timers.
- Disconnect idle SSL VPN users when a firewall policy authentication timeout occurs.
- Prevent SSL VPN users from being logged out because of high network latency.
Correct answer: AD
Question 8
Which of the following conditions must be met in order for a web browser to trust a web server certificate signed by a third-party CA?
- The public key of the web server certificate must be installed on the browser.
- The web-server certificate must be installed on the browser.
- The CA certificate that signed the web-server certificate must be installed on the browser.
- The private key of the CA certificate that signed the browser certificate must be installed on the browser.
Correct answer: C
Question 9
When using SD-WAN, how do you configure the next-hop gateway address for a member interface so that FortiGate can forward Internet traffic?
- It must be configured in a static route using the sdwan virtual interface.
- It must be provided in the SD-WAN member interface configuration.
- It must be configured in a policy-route using the sdwan virtual interface.
- It must be learned automatically through a dynamic routing protocol.
Correct answer: A
Question 10
Which statements about DNS filter profiles are true? (Choose two.)
- They can inspect HTTP traffic.
- They can redirect blocked requests to a specific portal.
- They can block DNS requests to known botnet command and control servers.
- They must be applied in firewall policies with SSL inspection enabled.
Correct answer: BC
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



