Download Fortinet NSE4 - FortiOS 6.0.NSE4_FGT-6.0.CertDumps.2020-02-12.127q.vcex
| Vendor: | Fortinet |
| Exam Code: | NSE4_FGT-6.0 |
| Exam Name: | Fortinet NSE4 - FortiOS 6.0 |
| Date: | Feb 12, 2020 |
| File Size: | 8 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Examine the IPS sensor configuration shown in the exhibit, and then answer the question below.
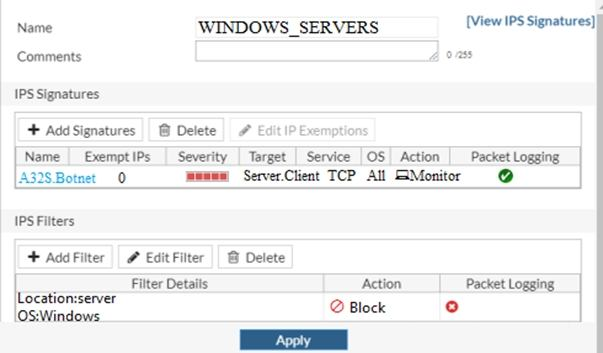
What are the expected actions if traffic matches this IPS sensor? (Choose two.)
- The sensor will gather a packet log for all matched traffic.
- The sensor will not block attackers matching the A32S.Botnet signature.
- The sensor will block all attacks for Windows servers.
- The sensor will reset all connections that match these signatures.
Correct answer: AC
Question 2
Which statement is true regarding the policy ID number of a firewall policy?
- Defines the order in which rules are processed.
- Represents the number of objects used in the firewall policy.
- Required to modify a firewall policy using the CLI.
- Changes when firewall policies are reordered.
Correct answer: C
Question 3
Which statements correctly describe transparent mode operation? (Choose three.)
- All interfaces of the transparent mode FortiGate device must be on different IP subnets.
- Ethernet packets are forwarded based on destination MAC addresses, not IP addresses.
- The transparent FortiGate is visible to network hosts in an IP traceroute.
- It permits inline traffic inspection and firewalling without changing the IP scheme of the network.
- FortiGate acts as transparent bridge and forwards traffic at Layer 2.
Correct answer: BDE
Question 4
Which of the following statements correctly describes FortiGates route lookup behavior when searching for a suitable gateway? (Choose two)
- Lookup is done on the first packet from the session originator
- Lookup is done on the last packet sent from the responder
- Lookup is done on every packet, regardless of direction
- Lookup is done on the first reply packet from the responder
Correct answer: AB
Question 5
Which of the following are valid actions for FortiGuard category based filter in a web filter profile in proxy-based inspection mode? (Choose two.)
- Warning
- Exempt
- Allow
- Learn
Correct answer: AC
Question 6
Which is the correct description of a hash result as it relates to digital certificates?
- A unique value used to verify the input data
- An output value that is used to identify the person or device that authored the input data.
- An obfuscation used to mask the input data.
- An encrypted output value used to safe-guard the input data
Correct answer: A
Question 7
You have tasked to design a new IPsec deployment with the following criteria:
- There are two HQ sues that all satellite offices must connect to
- The satellite offices do not need to communicate directly with other satellite offices
- No dynamic routing will be used
- The design should minimize the number of tunnels being configured.
Which topology should be used to satisfy all of the requirements?
- Partial mesh
- Hub-and-spoke
- Fully meshed
- Redundant
Correct answer: B
Question 8
On a FortiGate with a hard disk, how can you upload logs to FortiAnalyzer or FortiManager? (Choose two.)
- hourly
- real time
- on-demand
- store-and-upload
Correct answer: BD
Question 9
A FortiGate device has multiple VDOMs. Which statement about an administrator account configured with the default prof_admin profile is true?
- It can create administrator accounts with access to the same VDOM.
- It cannot have access to more than one VDOM.
- It can reset the password for the admin account.
- It can upgrade the firmware on the FortiGate device.
Correct answer: C
Question 10
Which of the following statements about the FSSO collector agent timers is true?
- The workstation verify interval is used to periodically check if a workstation is still a domain member.
- The IP address change verify interval monitors the server IP address where the collector agent is installed, and the updates the collector agent configuration if it changes.
- The user group cache expiry is used to age out the monitored groups.
- The dead entry timeout interval is used to age out entries with an unverified status.
Correct answer: D
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



