Download FCSS-FortiSASE 23 Administrator.FCSS_SASE_AD-23.VCEplus.2024-08-20.18q.vcex
| Vendor: | Fortinet |
| Exam Code: | FCSS_SASE_AD-23 |
| Exam Name: | FCSS-FortiSASE 23 Administrator |
| Date: | Aug 20, 2024 |
| File Size: | 2 MB |
| Downloads: | 4 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Which two deployment methods are used to connect a FortiExtender as a FortiSASE LAN extension? (Choose two.)
- Connect FortiExtender to FortiSASE using FortiZTP
- Enable Control and Provisioning Wireless Access Points (CAPWAP) access on the FortiSASE portal.
- Enter the FortiSASE domain name in the FortiExtender GUI as a static discovery server
- Configure an IPsec tunnel on FortiSASE to connect to FortiExtender.
Correct answer: AC
Explanation:
There are two deployment methods used to connect a FortiExtender as a FortiSASE LAN extension:Connect FortiExtender to FortiSASE using FortiZTP:FortiZero Touch Provisioning (FortiZTP) simplifies the deployment process by allowing FortiExtender to automatically connect and configure itself with FortiSASE.This method requires minimal manual configuration, making it efficient for large-scale deployments.Enter the FortiSASE domain name in the FortiExtender GUI as a static discovery server:Manually configuring the FortiSASE domain name in the FortiExtender GUI allows the extender to discover and connect to the FortiSASE infrastructure.This static discovery method ensures that FortiExtender can establish a connection with FortiSASE using the provided domain name.FortiOS 7.2 Administration Guide: Details on FortiExtender deployment methods and configurations.FortiSASE 23.2 Documentation: Explains how to connect and configure FortiExtender with FortiSASE using FortiZTP and static discovery. There are two deployment methods used to connect a FortiExtender as a FortiSASE LAN extension:
Connect FortiExtender to FortiSASE using FortiZTP:
FortiZero Touch Provisioning (FortiZTP) simplifies the deployment process by allowing FortiExtender to automatically connect and configure itself with FortiSASE.
This method requires minimal manual configuration, making it efficient for large-scale deployments.
Enter the FortiSASE domain name in the FortiExtender GUI as a static discovery server:
Manually configuring the FortiSASE domain name in the FortiExtender GUI allows the extender to discover and connect to the FortiSASE infrastructure.
This static discovery method ensures that FortiExtender can establish a connection with FortiSASE using the provided domain name.
FortiOS 7.2 Administration Guide: Details on FortiExtender deployment methods and configurations.
FortiSASE 23.2 Documentation: Explains how to connect and configure FortiExtender with FortiSASE using FortiZTP and static discovery.
Question 2
Refer to the exhibits.
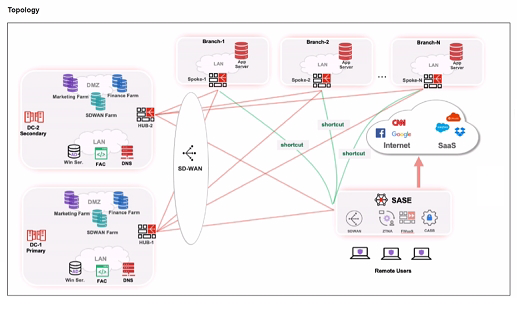
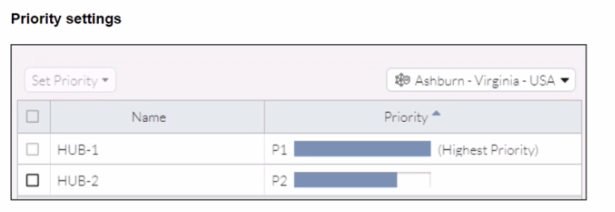
When remote users connected to FortiSASE require access to internal resources on Branch-2. how will traffic be routed?
- FortiSASE will use the SD-WAN capability and determine that traffic will be directed to HUB-2. which will then route traffic to Branch-2.
- FortiSASE will use the AD VPN protocol and determine that traffic will be directed to Branch-2 directly, using a static route
- FortiSASE will use the SD-WAN capability and determine that traffic will be directed to HUB-1, which will then route traffic to Branch-2.
- FortiSASE will use the AD VPN protocol and determine that traffic will be directed to Branch-2 directly, using a dynamic route
Correct answer: C
Explanation:
When remote users connected to FortiSASE require access to internal resources on Branch-2, the following process occurs:SD-WAN Capability:FortiSASE leverages SD-WAN to optimize traffic routing based on performance metrics and priorities.In the priority settings, HUB-1 is configured with the highest priority (P1), whereas HUB-2 has a lower priority (P2).Traffic Routing Decision:FortiSASE evaluates the available hubs (HUB-1 and HUB-2) and selects HUB-1 due to its highest priority setting.Once the traffic reaches HUB-1, it is then routed to the appropriate branch based on internal routing policies.Branch-2 Access:Since HUB-1 has the highest priority, FortiSASE directs the traffic to HUB-1.HUB-1 then routes the traffic to Branch-2, providing the remote users access to the internal resources.FortiOS 7.2 Administration Guide: Details on SD-WAN configurations and priority settings.FortiSASE 23.2 Documentation: Explains how FortiSASE integrates with SD-WAN to route traffic based on defined priorities and performance metrics. When remote users connected to FortiSASE require access to internal resources on Branch-2, the following process occurs:
SD-WAN Capability:
FortiSASE leverages SD-WAN to optimize traffic routing based on performance metrics and priorities.
In the priority settings, HUB-1 is configured with the highest priority (P1), whereas HUB-2 has a lower priority (P2).
Traffic Routing Decision:
FortiSASE evaluates the available hubs (HUB-1 and HUB-2) and selects HUB-1 due to its highest priority setting.
Once the traffic reaches HUB-1, it is then routed to the appropriate branch based on internal routing policies.
Branch-2 Access:
Since HUB-1 has the highest priority, FortiSASE directs the traffic to HUB-1.
HUB-1 then routes the traffic to Branch-2, providing the remote users access to the internal resources.
FortiOS 7.2 Administration Guide: Details on SD-WAN configurations and priority settings.
FortiSASE 23.2 Documentation: Explains how FortiSASE integrates with SD-WAN to route traffic based on defined priorities and performance metrics.
Question 3
When accessing the FortiSASE portal for the first time, an administrator must select data center locations for which three FortiSASE components? (Choose three.)
- Endpoint management
- Points of presence
- SD-WAN hub
- Logging
- Authentication
Correct answer: ABD
Explanation:
When accessing the FortiSASE portal for the first time, an administrator must select data center locations for the following FortiSASE components:Endpoint Management:The data center location for endpoint management ensures that endpoint data and policies are managed and stored within the chosen geographical region.Points of Presence (PoPs):Points of Presence (PoPs) are the locations where FortiSASE services are delivered to users. Selecting PoP locations ensures optimal performance and connectivity for users based on their geographical distribution.Logging:The data center location for logging determines where log data is stored and managed. This is crucial for compliance and regulatory requirements, as well as for efficient log analysis and reporting.FortiOS 7.2 Administration Guide: Details on initial setup and configuration steps for FortiSASE.FortiSASE 23.2 Documentation: Explains the importance of selecting data center locations for various FortiSASE components. When accessing the FortiSASE portal for the first time, an administrator must select data center locations for the following FortiSASE components:
Endpoint Management:
The data center location for endpoint management ensures that endpoint data and policies are managed and stored within the chosen geographical region.
Points of Presence (PoPs):
Points of Presence (PoPs) are the locations where FortiSASE services are delivered to users. Selecting PoP locations ensures optimal performance and connectivity for users based on their geographical distribution.
Logging:
The data center location for logging determines where log data is stored and managed. This is crucial for compliance and regulatory requirements, as well as for efficient log analysis and reporting.
FortiOS 7.2 Administration Guide: Details on initial setup and configuration steps for FortiSASE.
FortiSASE 23.2 Documentation: Explains the importance of selecting data center locations for various FortiSASE components.
Question 4
During FortiSASE provisioning, how many security points of presence (POPs) need to be configured by the FortiSASE administrator?
- 3
- 4
- 2
- 1
Correct answer: D
Explanation:
During FortiSASE provisioning, the FortiSASE administrator needs to configure at least one security point of presence (PoP). A single PoP is sufficient to get started with FortiSASE, providing the necessary security services and connectivity for users.Security Point of Presence (PoP):A PoP is a strategically located data center that provides security services such as secure web gateway, firewall, and VPN termination.Configuring at least one PoP ensures that users can connect to FortiSASE and benefit from its security features.Scalability:While only one PoP is required to start, additional PoPs can be added as needed to enhance redundancy, load balancing, and performance.FortiOS 7.2 Administration Guide: Provides details on the provisioning process for FortiSASE.FortiSASE 23.2 Documentation: Explains the configuration and role of security PoPs in the FortiSASE architecture. During FortiSASE provisioning, the FortiSASE administrator needs to configure at least one security point of presence (PoP). A single PoP is sufficient to get started with FortiSASE, providing the necessary security services and connectivity for users.
Security Point of Presence (PoP):
A PoP is a strategically located data center that provides security services such as secure web gateway, firewall, and VPN termination.
Configuring at least one PoP ensures that users can connect to FortiSASE and benefit from its security features.
Scalability:
While only one PoP is required to start, additional PoPs can be added as needed to enhance redundancy, load balancing, and performance.
FortiOS 7.2 Administration Guide: Provides details on the provisioning process for FortiSASE.
FortiSASE 23.2 Documentation: Explains the configuration and role of security PoPs in the FortiSASE architecture.
Question 5
How does FortiSASE hide user information when viewing and analyzing logs?
- By hashing data using Blowfish
- By hashing data using salt
- By encrypting data using Secure Hash Algorithm 256-bit (SHA-256)
- By encrypting data using advanced encryption standard (AES)
Correct answer: B
Explanation:
FortiSASE hides user information when viewing and analyzing logs by hashing data using salt. This approach ensures that sensitive user information is obfuscated, enhancing privacy and security.Hashing Data with Salt:Hashing data involves converting it into a fixed-size string of characters, which is typically a hash value.Salting adds random data to the input of the hash function, ensuring that even identical inputs produce different hash values.This method provides enhanced security by making it more difficult to reverse-engineer the original data from the hash value.Security and Privacy:Using salted hashes ensures that user information remains secure and private when stored or analyzed in logs.This technique is widely used in security systems to protect sensitive data from unauthorized access.FortiOS 7.2 Administration Guide: Provides information on log management and data protection techniques.FortiSASE 23.2 Documentation: Details on how FortiSASE implements data hashing and salting to secure user information in logs. FortiSASE hides user information when viewing and analyzing logs by hashing data using salt. This approach ensures that sensitive user information is obfuscated, enhancing privacy and security.
Hashing Data with Salt:
Hashing data involves converting it into a fixed-size string of characters, which is typically a hash value.
Salting adds random data to the input of the hash function, ensuring that even identical inputs produce different hash values.
This method provides enhanced security by making it more difficult to reverse-engineer the original data from the hash value.
Security and Privacy:
Using salted hashes ensures that user information remains secure and private when stored or analyzed in logs.
This technique is widely used in security systems to protect sensitive data from unauthorized access.
FortiOS 7.2 Administration Guide: Provides information on log management and data protection techniques.
FortiSASE 23.2 Documentation: Details on how FortiSASE implements data hashing and salting to secure user information in logs.
Question 6
Refer to the exhibit.
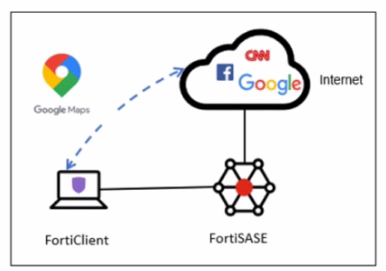
A company has a requirement to inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE VPN tunnel and redirect it to the endpoint physical Interface.
Which configuration must you apply to achieve this requirement?
- Exempt the Google Maps FQDN from the endpoint system proxy settings.
- Configure a static route with the Google Maps FQDN on the endpoint to redirect traffic
- Configure the Google Maps FQDN as a split tunneling destination on the FortiSASE endpoint profile.
- Change the default DNS server configuration on FortiSASE to use the endpoint system DNS.
Correct answer: C
Explanation:
To meet the requirement of inspecting all endpoint internet traffic on FortiSASE while excluding Google Maps traffic from the FortiSASE VPN tunnel and redirecting it to the endpoint's physical interface, you should configure split tunneling. Split tunneling allows specific traffic to bypass the VPN tunnel and be routed directly through the endpoint's local interface.Split Tunneling Configuration:Split tunneling enables selective traffic to be routed outside the VPN tunnel.By configuring the Google Maps Fully Qualified Domain Name (FQDN) as a split tunneling destination, you ensure that traffic to Google Maps bypasses the VPN tunnel and uses the endpoint's local interface instead.Implementation Steps:Access the FortiSASE endpoint profile configuration.Add the Google Maps FQDN to the split tunneling destinations list.This configuration directs traffic intended for Google Maps to bypass the VPN tunnel and be routed directly through the endpoint's physical network interface.FortiOS 7.2 Administration Guide: Provides details on split tunneling configuration.FortiSASE 23.2 Documentation: Explains how to set up and manage split tunneling for specific destinations. To meet the requirement of inspecting all endpoint internet traffic on FortiSASE while excluding Google Maps traffic from the FortiSASE VPN tunnel and redirecting it to the endpoint's physical interface, you should configure split tunneling. Split tunneling allows specific traffic to bypass the VPN tunnel and be routed directly through the endpoint's local interface.
Split Tunneling Configuration:
Split tunneling enables selective traffic to be routed outside the VPN tunnel.
By configuring the Google Maps Fully Qualified Domain Name (FQDN) as a split tunneling destination, you ensure that traffic to Google Maps bypasses the VPN tunnel and uses the endpoint's local interface instead.
Implementation Steps:
Access the FortiSASE endpoint profile configuration.
Add the Google Maps FQDN to the split tunneling destinations list.
This configuration directs traffic intended for Google Maps to bypass the VPN tunnel and be routed directly through the endpoint's physical network interface.
FortiOS 7.2 Administration Guide: Provides details on split tunneling configuration.
FortiSASE 23.2 Documentation: Explains how to set up and manage split tunneling for specific destinations.
Question 7
Which two advantages does FortiSASE bring to businesses with multiple branch offices? (Choose two.)
- It offers centralized management for simplified administration.
- It enables seamless integration with third-party firewalls.
- it offers customizable dashboard views for each branch location
- It eliminates the need to have an on-premises firewall for each branch.
Correct answer: AD
Explanation:
FortiSASE brings the following advantages to businesses with multiple branch offices:Centralized Management for Simplified Administration:FortiSASE provides a centralized management platform that allows administrators to manage security policies, configurations, and monitoring from a single interface.This simplifies the administration and reduces the complexity of managing multiple branch offices.Eliminates the Need for On-Premises Firewalls:FortiSASE enables secure access to the internet and cloud applications without requiring dedicated on-premises firewalls at each branch office.This reduces hardware costs and simplifies network architecture, as security functions are handled by the cloud-based FortiSASE solution.FortiOS 7.2 Administration Guide: Provides information on the benefits of centralized management and cloud-based security solutions.FortiSASE 23.2 Documentation: Explains the advantages of using FortiSASE for businesses with multiple branch offices, including reduced need for on-premises firewalls. FortiSASE brings the following advantages to businesses with multiple branch offices:
Centralized Management for Simplified Administration:
FortiSASE provides a centralized management platform that allows administrators to manage security policies, configurations, and monitoring from a single interface.
This simplifies the administration and reduces the complexity of managing multiple branch offices.
Eliminates the Need for On-Premises Firewalls:
FortiSASE enables secure access to the internet and cloud applications without requiring dedicated on-premises firewalls at each branch office.
This reduces hardware costs and simplifies network architecture, as security functions are handled by the cloud-based FortiSASE solution.
FortiOS 7.2 Administration Guide: Provides information on the benefits of centralized management and cloud-based security solutions.
FortiSASE 23.2 Documentation: Explains the advantages of using FortiSASE for businesses with multiple branch offices, including reduced need for on-premises firewalls.
Question 8
Refer to the exhibit.
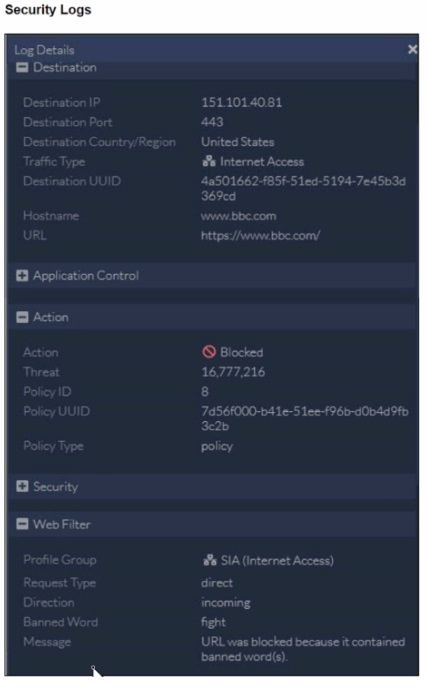
To allow access, which web tiller configuration must you change on FortiSASE?
- FortiGuard category-based filter
- content filter
- URL Filter
- inline cloud access security broker (CASB) headers
Correct answer: C
Explanation:
The exhibit indicates that the URL https://www.bbc.com/ is being blocked due to containing a banned word ('fight'). To allow access to this specific URL, you need to adjust the URL filter settings on FortiSASE.URL Filtering:URL filtering allows administrators to define policies that block or allow access to specific URLs or URL patterns.In this case, the URL filter is set to block any URL containing the word 'fight.'Modifying URL Filter:Navigate to the Web Filter configuration in FortiSASE.Locate the URL filter settings.Add an exception for the URL https://www.bbc.com/ to allow access, even if it contains a banned word.Alternatively, remove or adjust the banned word list to exclude the word 'fight' if it's not critical to the security policy.FortiOS 7.2 Administration Guide: Provides details on configuring and managing URL filters.FortiSASE 23.2 Documentation: Explains how to set up and modify web filtering policies, including URL filters. The exhibit indicates that the URL https://www.bbc.com/ is being blocked due to containing a banned word ('fight'). To allow access to this specific URL, you need to adjust the URL filter settings on FortiSASE.
URL Filtering:
URL filtering allows administrators to define policies that block or allow access to specific URLs or URL patterns.
In this case, the URL filter is set to block any URL containing the word 'fight.'
Modifying URL Filter:
Navigate to the Web Filter configuration in FortiSASE.
Locate the URL filter settings.
Add an exception for the URL https://www.bbc.com/ to allow access, even if it contains a banned word.
Alternatively, remove or adjust the banned word list to exclude the word 'fight' if it's not critical to the security policy.
FortiOS 7.2 Administration Guide: Provides details on configuring and managing URL filters.
FortiSASE 23.2 Documentation: Explains how to set up and modify web filtering policies, including URL filters.
Question 9
When you configure FortiSASE Secure Private Access (SPA) with SD-WAN integration, you must establish a routing adjacency between FortiSASE and the FortiGate SD-WAN hub. Which routing protocol must you use?
- BGP
- IS-IS
- OSPF
- EIGRP
Correct answer: A
Explanation:
When configuring FortiSASE Secure Private Access (SPA) with SD-WAN integration, establishing a routing adjacency between FortiSASE and the FortiGate SD-WAN hub requires the use of the Border Gateway Protocol (BGP).BGP (Border Gateway Protocol):BGP is widely used for establishing routing adjacencies between different networks, particularly in SD-WAN environments.It provides scalability and flexibility in managing dynamic routing between FortiSASE and the FortiGate SD-WAN hub.Routing Adjacency:BGP enables the exchange of routing information between FortiSASE and the FortiGate SD-WAN hub.This ensures optimal routing paths and efficient traffic management across the hybrid network.FortiOS 7.2 Administration Guide: Provides information on configuring BGP for SD-WAN integration.FortiSASE 23.2 Documentation: Details on setting up routing adjacencies using BGP for Secure Private Access with SD-WAN. When configuring FortiSASE Secure Private Access (SPA) with SD-WAN integration, establishing a routing adjacency between FortiSASE and the FortiGate SD-WAN hub requires the use of the Border Gateway Protocol (BGP).
BGP (Border Gateway Protocol):
BGP is widely used for establishing routing adjacencies between different networks, particularly in SD-WAN environments.
It provides scalability and flexibility in managing dynamic routing between FortiSASE and the FortiGate SD-WAN hub.
Routing Adjacency:
BGP enables the exchange of routing information between FortiSASE and the FortiGate SD-WAN hub.
This ensures optimal routing paths and efficient traffic management across the hybrid network.
FortiOS 7.2 Administration Guide: Provides information on configuring BGP for SD-WAN integration.
FortiSASE 23.2 Documentation: Details on setting up routing adjacencies using BGP for Secure Private Access with SD-WAN.
Question 10
A FortiSASE administrator is configuring a Secure Private Access (SPA) solution to share endpoint information with a corporate FortiGate.
Which three configuration actions will achieve this solution? (Choose three.)
- Add the FortiGate IP address in the secure private access configuration on FortiSASE.
- Use the FortiClient EMS cloud connector on the corporate FortiGate to connect to FortiSASE
- Register FortiGate and FortiSASE under the same FortiCloud account.
- Authorize the corporate FortiGate on FortiSASE as a ZTNA access proxy.
- Apply the FortiSASE zero trust network access (ZTNA) license on the corporate FortiGate.
Correct answer: ABC
Explanation:
To configure a Secure Private Access (SPA) solution to share endpoint information between FortiSASE and a corporate FortiGate, you need to take the following steps:Add the FortiGate IP address in the secure private access configuration on FortiSASE:This step allows FortiSASE to recognize and establish a connection with the corporate FortiGate.Use the FortiClient EMS cloud connector on the corporate FortiGate to connect to FortiSASE:The EMS (Endpoint Management Server) cloud connector facilitates the integration between FortiClient endpoints and FortiSASE, enabling seamless sharing of endpoint information.Register FortiGate and FortiSASE under the same FortiCloud account:By registering both FortiGate and FortiSASE under the same FortiCloud account, you ensure centralized management and synchronization of configurations and policies.FortiOS 7.2 Administration Guide: Provides details on configuring Secure Private Access and integrating with FortiGate.FortiSASE 23.2 Documentation: Explains how to set up and manage connections between FortiSASE and corporate FortiGate. To configure a Secure Private Access (SPA) solution to share endpoint information between FortiSASE and a corporate FortiGate, you need to take the following steps:
Add the FortiGate IP address in the secure private access configuration on FortiSASE:
This step allows FortiSASE to recognize and establish a connection with the corporate FortiGate.
Use the FortiClient EMS cloud connector on the corporate FortiGate to connect to FortiSASE:
The EMS (Endpoint Management Server) cloud connector facilitates the integration between FortiClient endpoints and FortiSASE, enabling seamless sharing of endpoint information.
Register FortiGate and FortiSASE under the same FortiCloud account:
By registering both FortiGate and FortiSASE under the same FortiCloud account, you ensure centralized management and synchronization of configurations and policies.
FortiOS 7.2 Administration Guide: Provides details on configuring Secure Private Access and integrating with FortiGate.
FortiSASE 23.2 Documentation: Explains how to set up and manage connections between FortiSASE and corporate FortiGate.
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



