Download CompTIA PenTest-Certification Exam.PT0-003.ExamTopics.2025-10-03.172q.vcex
| Vendor: | CompTIA |
| Exam Code: | PT0-003 |
| Exam Name: | CompTIA PenTest-Certification Exam |
| Date: | Oct 03, 2025 |
| File Size: | 1 MB |
| Downloads: | 14 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
A penetration tester wants to send a specific network packet with custom flags and sequence numbers to a vulnerable target. Which of the following should the tester use?
- tcprelay
- Bluecrack
- Scapy
- tcpdump
Correct answer: C
Explanation:
C: 1 - Mosted C: 1 - Mosted
Question 2
A penetration tester needs to test a very large number of URLs for public access. Given the following code snippet:
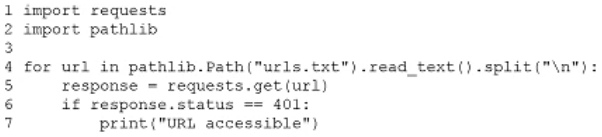
Which of the following changes is required?
- The condition on line 6
- The method on line 5
- The import on line 1
- The delimiter in line 3
Correct answer: A
Explanation:
A: 2 - Mosted A: 2 - Mosted
Question 3
During a penetration test, a tester captures information about an SPN account. Which of the following attacks requires this information as a prerequisite to proceed?
- Golden Ticket
- Kerberoasting
- DCShadow
- LSASS dumping
Correct answer: B
Explanation:
B: 2 - Mosted B: 2 - Mosted
Question 4
A penetration tester is performing reconnaissance for a web application assessment. Upon investigation, the tester reviews the robots.txt file for items of interest.
INSTRUCTIONS -
Select the tool the penetration tester should use for further investigation.
Select the three entries in the robots.txt file that the penetration tester should recommend for removal.
If at any time you would like to bring back the inital state of the simulation, please click the Reset All button.
Correct answer: To work with this question, an Exam Simulator is required.
Question 5
While performing an internal assessment, a tester uses the following command: crackmapexec smb 192.168.1.0/24 -u user.txt -p Summer123@
Which of the following is the main purpose of the command?
- To perform a pass-the-hash attack over multiple endpoints within the internal network
- To perform common protocol scanning within the internal network
- To perform password spraying on internal systems
- To execute a command in multiple endpoints at the same time
Correct answer: C
Explanation:
C: 3 - Mosted C: 3 - Mosted
Question 6
A tester gains initial access to a server and needs to enumerate all corporate domain DNS records. Which of the following commands should the tester use?
- dig +short A AAAA local.domain
- nslookup local.domain
- dig afxr @local.dns.server
- nslookup -server local.dns.server local.domain *
Correct answer: C
Explanation:
C: 1 - Mosted C: 1 - Mosted
Question 7
A penetration tester is performing network reconnaissance. The tester wants to gather information about the network without causing detection mechanisms to flag the reconnaissance activities. Which of the following techniques should the tester use?
- Sniffing
- Banner grabbing
- TCP/UDP scanning
- Ping sweeps
Correct answer: A
Explanation:
A: 1 A: 1
Question 8
During a security assessment, a penetration tester uses a tool to capture plaintext log-in credentials on the communication between a user and an authentication system. The tester wants to use this information for further unauthorized access. Which of the following tools is the tester using?
- Burp Suite
- Wireshark
- Zed Attack Proxy
- Metasploit
Correct answer: B
Explanation:
B: 2 - Mosted B: 2 - Mosted
Question 9
A penetration tester established an initial compromise on a host. The tester wants to pivot to other targets and set up an appropriate relay. The tester needs to enumerate through the compromised host as a relay from the tester's machine. Which of the following commands should the tester use to do this task from the tester's host?
- attacker_host$ nmap -sT <target_cidr> | nc -n <compromised_host> 22
- attacker_host$ mknod backpipe pattacker_host$ nc -l -p 8000 | 0 <backpipe | nc <target_cidr> 80 | tee backpipe
- attacker_host$ nc -nlp 8000 | nc -n <target_cidr>attacker_host$ nmap -sT 127.0.0.1 8000
- attacker_host$ proxychains nmap -sT <target_cidr>
Correct answer: D
Explanation:
D: 2 - Mosted D: 2 - Mosted
Question 10
A penetration tester is unable to identify the Wi-Fi SSID on a client's cell phone. Which of the following techniques would be most effective to troubleshoot this issue?
- Sidecar scanning
- Channel scanning
- Stealth scanning
- Static analysis scanning
Correct answer: B
Explanation:
B: 7 - Mosted B: 7 - Mosted
Question 11
A client recently hired a penetration testing firm to conduct an assessment of their consumer-facing web application. Several days into the assessment, the client's networking team observes a substantial increase in DNS traffic. Which of the following would most likely explain the increase in DNS traffic?
- Covert data exfiltration
- URL spidering
- HTML scrapping
- DoS attack
Correct answer: A
Explanation:
A: 2B: 1 - Mosted A: 2B: 1 - Mosted
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!




