Download CompTIA Cybersecurity Analyst.CS0-002.CertDumps.2023-11-24.298q.vcex
| Vendor: | CompTIA |
| Exam Code: | CS0-002 |
| Exam Name: | CompTIA Cybersecurity Analyst |
| Date: | Nov 24, 2023 |
| File Size: | 7 MB |
| Downloads: | 10 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
A malicious hacker wants to gather guest credentials on a hotel 802.11 network. Which of the following tools is the malicious hacker going to use to gain access to information found on the hotel network?
- Nikto
- Aircrak-ng
- Nessus
- tcpdump
Correct answer: B
Question 2
A security analyst needs to identify possible threats to a complex system a client is developing. Which of the following methodologies would BEST address this task?
- Open Source Security Information Management (OSSIM)
- Software Assurance Maturity Model (SAMM)
- Open Web Application Security Project (OWASP)
- Spoofing, Tampering. Repudiation, Information disclosure. Denial of service, Elevation of privileges (STRIDE)
Correct answer: C
Question 3
An analyst identifies multiple instances of node-to-node communication between several endpoints within the 10.200.2.0/24 network and a user machine at the IP address 10.200.2.5. This user machine at the IP address 10.200.2.5 is also identified as initiating outbound communication during atypical business hours with several IP addresses that have recently appeared on threat feeds.
Which of the following can be inferred from this activity?
- 10.200.2.0/24 is infected with ransomware.
- 10.200.2.0/24 is not routable address space.
- 10.200.2.5 is a rogue endpoint.
- 10.200.2.5 is exfiltrating datA.
Correct answer: D
Question 4
A security analyst receives an alert that highly sensitive information has left the company's network Upon investigation, the analyst discovers an outside IP range has had connections from three servers more than 100 times m the past month The affected servers are virtual machines Which of the following is the BEST course of action?
- Shut down the servers as soon as possible, move them to a clean environment, restart, run a vulnerability scanner to find weaknesses determine the root cause, remediate, and report
- Report the data exfiltration to management take the affected servers offline, conduct an antivirus scan, remediate all threats found, and return the servers to service.
- Disconnect the affected servers from the network, use the virtual machine console to access the systems, determine which information has left the network, find the security weakness,and remediate
- Determine if any other servers have been affected, snapshot any servers found, determine the vector that was used to allow the data exfiltration. fix any vulnerabilities, remediate, and report.
Correct answer: A
Question 5
A security analyst is reviewing the following log entries to identify anomalous activity:
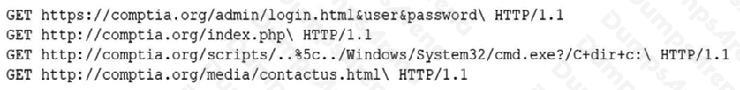
Which of the following attack types is occurring?
- Directory traversal
- SQL injection
- Buffer overflow
- Cross-site scripting
Correct answer: A
Question 6
An organization recently discovered some inconsistencies in the motherboards it received from a vendor. The organization's security team then provided guidance on how to ensure the authenticity of the motherboards it received from vendors.
Which of the following would be the BEST recommendation for the security analyst to provide'?
- The organization should evaluate current NDAs to ensure enforceability of legal actions.
- The organization should maintain the relationship with the vendor and enforce vulnerability scans.
- The organization should ensure all motherboards are equipped with a TPM.
- The organization should use a certified, trusted vendor as part of the supply chain.
Correct answer: D
Question 7
A newly appointed Chief Information Security Officer (CISO) has completed a risk assessment review of the organization and wants to reduce the numerous risks that were identified. Which of the following will provide a trend of risk mitigation?
- Risk response
- Risk analysis
- Planning
- Oversight
- Continuous monitoring
Correct answer: A
Question 8
A security manager has asked an analyst to provide feedback on the results of a penetration lest. After reviewing the results the manager requests information regarding the possible exploitation of vulnerabilities Much of the following information data points would be MOST useful for the analyst to provide to the security manager who would then communicate the risk factors to senior management? (Select TWO)
- Probability
- Adversary capability
- Attack vector
- Impact
- Classification
- Indicators of compromise
Correct answer: AD
Question 9
While investigating an incident in a company's SIEM console, a security analyst found hundreds of failed SSH login attempts, which all occurred in rapid succession. The failed attempts were followed by a successful login on the root user Company policy allows systems administrators to manage their systems only from the company's internal network using their assigned corporate logins. Which of the following are the BEST actions the analyst can take to stop any further compromise?
(Select TWO).
A Configure /etc/sshd_config to deny root logins and restart the SSHD service.
- Add a rule on the network IPS to block SSH user sessions
- Configure /etc/passwd to deny root logins and restart the SSHD service.
- Reset the passwords for all accounts on the affected system.
- Add a rule on the perimeter firewall to block the source IP address.
- Add a rule on the affected system to block access to port TCP/22.
- Add a rule on the network IPS to block SSH user sessions
- Configure /etc/passwd to deny root logins and restart the SSHD service.
- Reset the passwords for all accounts on the affected system.
- Add a rule on the perimeter firewall to block the source IP address.
- Add a rule on the affected system to block access to port TCP/22.
Correct answer: D
Question 10
An organization's Chief Information Security Officer (CISO) has asked department leaders to coordinate on communication plans that can be enacted in response to different cybersecurity incident triggers
Which of the following is a benefit of having these communication plans?
- They can help to prevent the inadvertent release of damaging information outside the organization.
- They can quickly inform the public relations team to begin coordinating with the media as soon as a breach is detected.
- They can help to keep the organization's senior leadership informed about the status of patching during the recovery phase.
- They can help to limit the spread of worms by coordinating with help desk personnel earlier in the recovery phase.
Correct answer: C
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



