Download NetScaler.1Y0-340.Prep4Sure.2019-01-23.65q.vcex
| Vendor: | Citrix |
| Exam Code: | 1Y0-340 |
| Exam Name: | NetScaler |
| Date: | Jan 23, 2019 |
| File Size: | 232 KB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
A Citrix Engineer has deployed Front-end Optimization on NetScaler. The following are the snippets of the content before and after optimization.
Before Optimization:
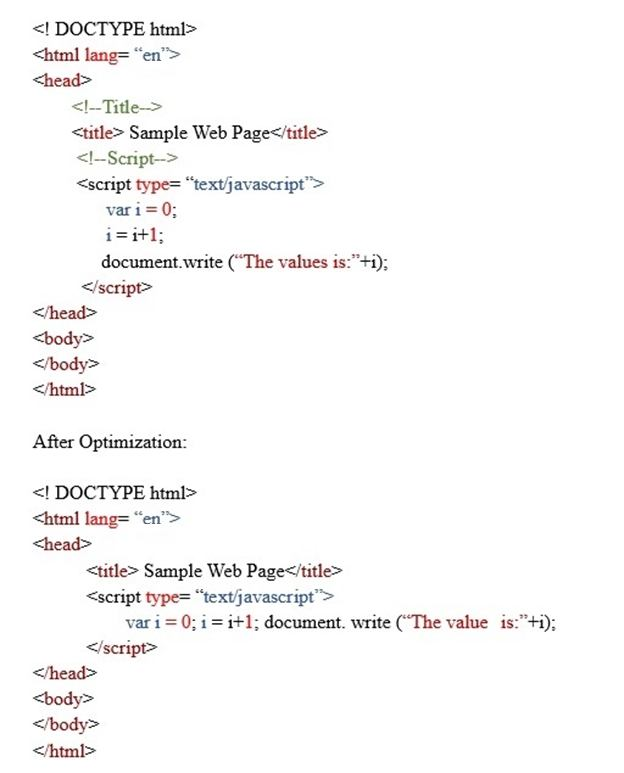
Which optimization technique has been applied to the content?
- Convert linked JavaScript to inline JavaScript
- Minify JavaScript
- Move JavaScript to End of Body Tag
- Inline JavaScript
Correct answer: B
Explanation:
Reference: https://docs.citrix.com/en-us/netscaler/10-5/ns-optimization-wrapper-10-con/ns-feo-con.html Reference: https://docs.citrix.com/en-us/netscaler/10-5/ns-optimization-wrapper-10-con/ns-feo-con.html
Question 2
Scenario: A Citrix Engineer has deployed four NetScaler MPXs with the following network configuration:
- Management traffic is on VLAN 5 (NSIP).
- Application and server traffic is on VLAN 10 (SNIP).
The engineer added the NetScaler Management and Analytics System (NMAS) interface to VLAN 10 to deploy a NMAS High Availability (HA) pair to manage and monitor the applications and virtual servers. After doing so, the engineer is NOT able to see the NetScaler or applications that need to be managed.
How can the engineer resolve the issue?
- Configure VLAN 5 as NSVLAN 5
- Move the NMAS interface to VLAN 5
- Configure VLAN 5 as NSSYNC VLAN
- Bind SNIP to VLAN 5
Correct answer: A
Question 3
A Citrix Engineer needs to configure NetScaler Management and Analytics System (NMAS) in their network to retain network reporting data, events, audit logs, and task logs for 20 days.
Which settings can the engineer configure to meet the requirement?
- System Prune Settings
- System Backup Settings
- Instance Backup Settings
- Syslog Prune Settings
Correct answer: A
Explanation:
Reference: https://docs.citrix.com/en-us/netscaler-mas/12/getting-started-with-mas.html Reference: https://docs.citrix.com/en-us/netscaler-mas/12/getting-started-with-mas.html
Question 4
A Citrix Engineer needs to ensure that all traffic to the virtual server is blocked if NONE of the bound Application Firewall policies are matched.
Which setting can the engineer configure to meet this requirement?
- set appfw settings –undefAction APPFW_BLOCK
- set ns httpProfile nshttp_default_profile-dropInvalReqs DISABLED
- set ns httpProfie nshttp_default_profile –dropInvalReqs ENABLED
- set appfw settings –defaultProfile APPFW_BLOCK
Correct answer: D
Question 5
Scenario: A Citrix Engineer needs to configure the Application Firewall to do a credit card check using the command-line interface (CLI) and configure the profile to obscure the credit card number.
Which parameter will the engineer add in the CLI to encrypt the credit card numbers in the logs?
- –creditCardAction BLOCK
- -creditCardMaxAllowed
- –creditCardXOut ON
- –doSecureCreditCardLogging ON
Correct answer: D
Explanation:
Reference: https://docs.citrix.com/en-us/netscaler/11-1/application-firewall/logs.html Reference: https://docs.citrix.com/en-us/netscaler/11-1/application-firewall/logs.html
Question 6
Scenario: A Citrix Engineer must enable a cookie consistency security check and ensure that all the session cookies get encrypted during the transaction. The engineer needs to ensure that none of the persistent coolies are encrypted and decrypted and decrypt any encrypted cookies during the transaction.
Which cookie consistency security feature will the engineer configure in the following configuration to achieve the desired results?
add appfw profile Test123 –startURLAction none- denyURLAction none- cookieConsistencyAction log –cookieTransforms ON –cookieEncryption ecryptSessionOnly –addCookieFlags httpOnly –crossSiteScriptingAction none- SQLInjectionAction log stats –SQLInjectionTransfrormSpecialChars ON- SQLInjectionCheckSQLWildChars ON –fieldFormatAction none –bufferOverflowAction none –responseContentType “application/octet-stream”- XMLSQLInjectionAction none –XMLXSSAction none-XMLWSIAction none- XMLValidationAction none
- Configure Encrypt Server cookies to “Encrypt All”
- Configure Encrypt Server cookies to “None”
- Configure Encrypt Server cookies to “Encrypt Session Only”
- Configure Encrypt Server cookies to “Encrypt only”
Correct answer: B
Explanation:
Reference: https://docs.citrix.com/en-us/netscaler/12/application-firewall/top-level-protections/cookie-consistency-check.html Reference: https://docs.citrix.com/en-us/netscaler/12/application-firewall/top-level-protections/cookie-consistency-check.html
Question 7
A Citrix Engineer needs to write a regular expression to treat the URL www.citrix.com as a literal string.
Which regular expression can the engineer use?
- www$.citrix$.com
- [www\]. [citrix\]. [com\]
- www+.citrix+.com
- www\.citrix\.com
Correct answer: B
Question 8
What can a Citrix Engineer do to decrease browser load times by increasing the number of parallel connections to the resource?
- Configure Domain Sharding.
- Add more web servers.
- Block JavaScript on client browsers.
- Do NOT allow HTML websites.
Correct answer: A
Explanation:
Reference: https://docs.citrix.com/en-us/netscaler/10-5/ns-optimization-wrapper-10-con/ns-feo-con.html Reference: https://docs.citrix.com/en-us/netscaler/10-5/ns-optimization-wrapper-10-con/ns-feo-con.html
Question 9
Scenario: A Citrix Engineer observes that when going through NetScaler, user connections fail and users are unable to access Exchange server. However, users can connect directly to the Exchange server. After checking the logs, the engineer finds that the POST request is blocked through the NetScaler.
The log in/ var/log/ns.log is as follows:
Jul 20 11:00: 38 <local0.info>x.x.x. 1 07/20/2017:11:00:38 GMT ns 0-PPE-0:APPFW AF_400_RESP 29362 0: x.x.x.1 439800-PPEO- urlwdummy
https://test.abc.com/rpc/rpcproxy.dll?mail.sfmta.com:6004 Bad request headers. Content-length exceeds post body limit <blocked>
Which parameter can the engineer modify to resolve the issue while maintaining security?
- Increase the Maximum Header Length under nshttp_default_profile.
- Increase the POST body limit using the HTTP profile.
- Add an Application Firewall policy with the expression “HTTP.REQ.METHOD.EQ(\ “POST”\)” with APPFW_BYPASS profile bound.
- Increase the POST body limit under common settings in Application Firewall profile settings.
Correct answer: D
Question 10
Which two threats can be prevented by using IP Reputation? (Choose two.)
- Trojan horses
- Phishing Proxies
- Worm
- Compromised IPv6 web-server
- Compromised IPv4 web-server
Correct answer: BE
Explanation:
Reference: https://docs.citrix.com/en-us/netscaler/11/security/reputation/ip-reputation.html Reference: https://docs.citrix.com/en-us/netscaler/11/security/reputation/ip-reputation.html
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



