Download Cisco Meraki Solutions Specialist.500-220.ExamTopics.2025-12-28.85q.vcex
| Vendor: | Cisco |
| Exam Code: | 500-220 |
| Exam Name: | Cisco Meraki Solutions Specialist |
| Date: | Dec 28, 2025 |
| File Size: | 2 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Which Radio Frequency (RF) Profile setting is typically used to decrease the Service Set Identifier (SSID) overhead, exclude legacy clients, and promote more efficient client roaming?
- Minimum bitrate
- Channel width
- Band selection
- Transmit power range
Correct answer: A
Question 2
Which two limitations are addressed by the implementation of Adaptive Policy? (Choose two.)
- managing network policies when IP addresses are prone to changes over time
- applying segmentation inside a VLAN
- preventing the micro-segmentation of clients within the network
- ensuring dedicated bandwidth for specific applications
- implementing Quality of Service (QoS) policies within a flat Layer 2 network
Correct answer: AB
Question 3
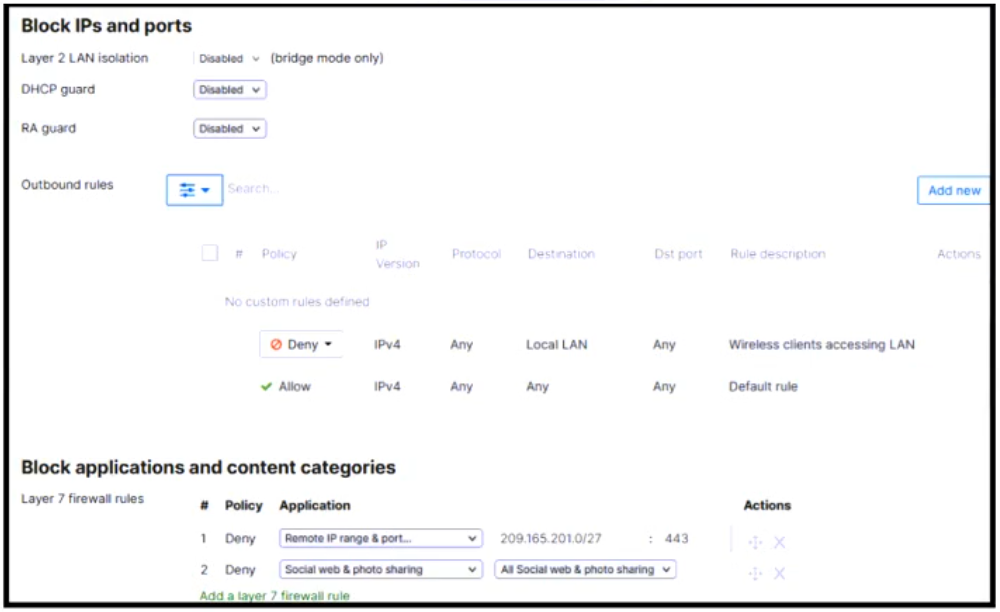
Refer to the exhibit. After associating with the Officers SSID and receiving an IP address on the 10.0.0/8 subnet, a wireless user submitted a support ticket that they cannot access wired network resources. Which configuration will provide successful network communication?
- The ‘DHCP guard’ setting should be adjusted from ‘Disabled’ to ‘Enabled.’
- The Layer 7 firewall rules prevent wired IP traffic from being forwarded and should be disabled.
- An ‘Allow’ rule must be added to the Outbound rules list to connect to the necessary resources.
- The Layer 2 LAN isolation setting should be adjusted from ‘Disabled’ to ‘Enabled.’
Correct answer: C
Question 4
A legacy wireless client, supporting WPA2 security, cannot associate to a guest wireless network. What is the cause?
- The guest wireless network is configured with layer 2 LAN isolation.
- The guest wireless network is configured with Open (no encryption).
- The guest wireless network is configured with WPA3 transition mode with 802.1w set to “Enabled.”
- The guest wireless network is configured with Opportunistic Wireless Encryption (OWE) with 802.1w set to “Required.”
Correct answer: D
Question 5
Which technique is not a PCI requirement but is considered a best practice for limiting the cardholder data environment (CDE) from the remainder of a corporate network?
- Limit inbound connections to the CDE while allowing all outbound connections originating from the CDE.
- Establishing wired network segmentation between the CDE and the rest of the corporate network.
- Implementing identical firewall rules between corporate and CDE egress points.
- Incorporate the CDE within the corporate network's established Demilitarized Zone (DMZ).
Correct answer: B
Question 6
Which two features can be configured on a Cisco Meraki MX security appliance and on a vMX virtual instance? (Choose two.)
- SD-WAN policies
- client VPN
- Active Directory
- Layer 3 and Layer 7 firewall rules
- threat protection
Correct answer: AD
Question 7
Which two wireless threats can be automatically mitigated by the dedicated security radio when using Air Marshal? (Choose two.)
- Malicious broadcasts
- Packet floods
- Network impersonation
- Wired LAN compromise
- SSID spoofing
Correct answer: BC
Question 8
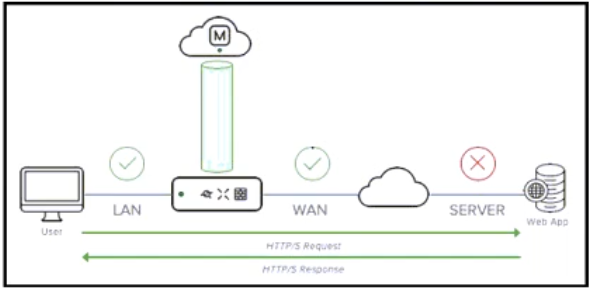
Refer to the exhibit. Meraki Insight aggregates network statistics on the MX and sends those aggregates back to the Meraki Cloud. In which three ways are aggregated statistics sent? (Choose three.)
- 443
- UDP
- TCP
- 7351
- SYSLOG traffic
- TLS-SYSLOG traffic
Correct answer: A
Question 9
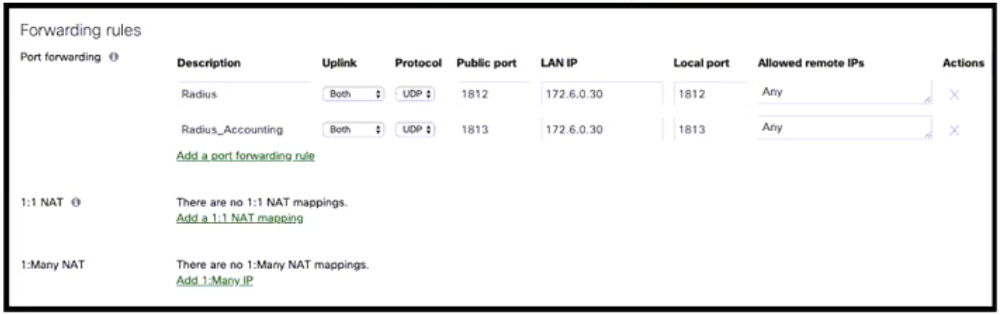
Refer to the exhibit. 172.16.0.0/24 is a configured local VLAN on the Cisco Meraki MX security appliance. What happens to inbound traffic flow to the MX WAN with a destination of TCP port 1813?
- The traffic is forwarded to 172.16.0.30 on the WAN.
- The traffic is dropped on the WAN of the MX security appliance.
- The traffic is forwarded to 172.16.0.30 on the LAN.
- The traffic is dropped on the WAN of the MX security appliance due to the “any” allow remote IP rule.
Correct answer: B
Question 10
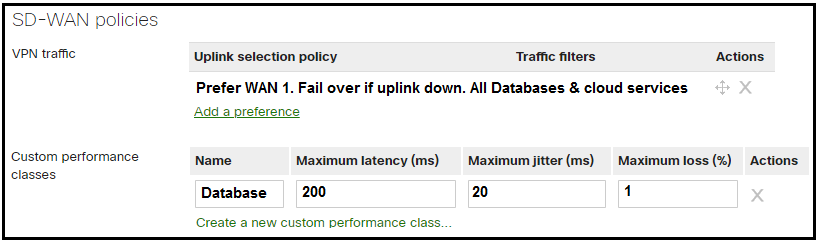
Refer to the exhibit. Which condition or conditions will cause the “All Databases & cloud services” SD-WAN traffic to be routed via a VPN tunnel on WAN2?
- WAN1 tunnel latency is 20 ms or more, irrespective of WAN2 tunnel performance.
- WAN1 tunnel latency is 20 ms or more, and WAN2 tunnel meets the configured performance criteria.
- WAN1 tunnel latency is 20 ms or less, irrespective of WAN2 tunnel performance.
- WAN1 tunnel latency is 20 ms or less, and WAN2 tunnel meets the configured performance criteria.
Correct answer: B
Question 11
What happens to an unsupervised iOS device when the “Meraki management” profile is removed?
- The “Meraki management” profile is removed. All configuration profiles that Systems Manager pushed remain.
- The “Meraki management” profile is removed. All configuration profiles that Systems Manager pushed are also removed.
- The “Meraki management” profile is removed and then pushed automatically by Systems Manager.
- The “Meraki management” profile cannot be removed.
Correct answer: A
Question 12
What are two methods of targeting and applying management profiles to System Manager clients? (Choose two.)
- by defining a range of serial numbers
- by defining the scope
- by using device tags
- by using Wi-Fi tags
- by using dynamic IP tags
Correct answer: BC
Question 13
Drag and drop the descriptions from the left onto the permission types on the right.
Correct answer: To work with this question, an Exam Simulator is required.
Question 14
A Cisco Meraki MX security appliance is trying to route a packet to the destination IP address of 172.18.24.12. Which routes contained in its routing table does it select?
- Auto VPN route 172.18.0.0/16
- non-Meraki VPN route 172.18.24.0/24
- directly connected 172.18.16.0/20
- static route 172.16.0.0/12
Correct answer: B
Question 15
There will be 100 concurrent users streaming video to their laptops. A 30/70 split between 2.4 Ghz and 5 Ghz will be used. Roughly how many APs (rounded to the nearest whole number) are needed based on client count?
- 2
- 3
- 4
- 5
Correct answer: B
Question 16
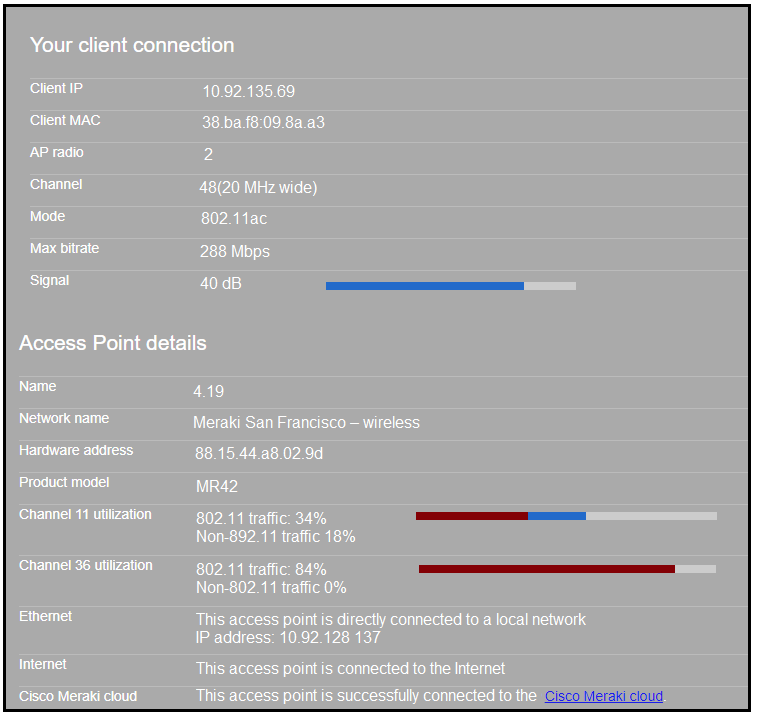
Refer to the exhibit. Why does the end user complain of poor wireless performance?
- Channel 48 utilization is at 84 percent.
- The client is using 20 MHz channel width to connect.
- Non-802.11 traffic of 18 percent indicates poor AP placement.
- The client is connected to the secondary radio of the AP instead of the primary radio.
Correct answer: A
Question 17
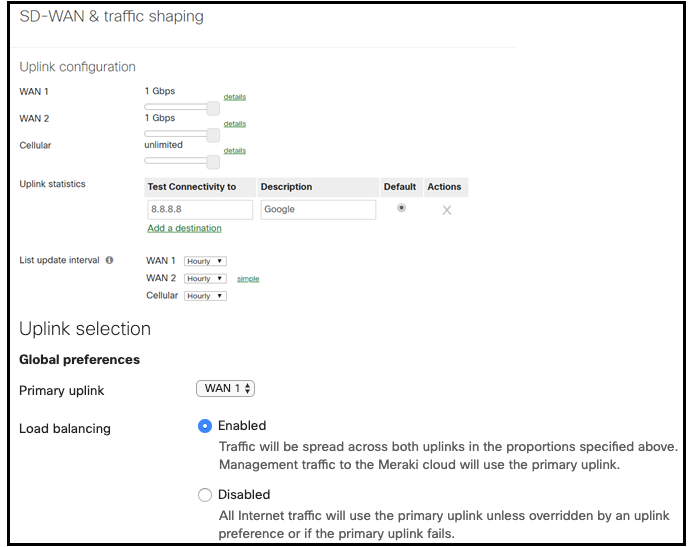
Refer to the exhibit. What is the ratio of internet-bound flows that route via WAN 1 compared with WAN 2?
- All flows egress via WAN 1.
- All flows alternate in a 1:1 ratio.
- All flows alternate in a 5:1 ratio.
- All flows alternate in a 2:1 ratio.
Correct answer: B
Question 18
The WAN connection of a Cisco Meraki MX security appliance is congested, and the MX appliance is buffering the traffic from LAN ports going to the WAN ports. High, normal, and low priority queue buffers are all full. Which proportion of the normal traffic is forwarded compared to the other queues?
- 4/10 packets
- 2/10 packets
- 2/7 packets
- 5/15 packets
Correct answer: C
Question 19
An organization requires that BYOD devices be enrolled in Systems Manager before they gain access to the network. Part of the enrollment includes pushing out the corporate SSID preshared key, corporate email settings, and some business-sensitive PDFs. When a user leaves the organization, which Systems Manager feature allows the removal of only the MDM-delivered content from the user’s device?
- Unenroll Device
- Clear Pushed Data
- Selective Wipe
- Erase Device
Correct answer: C
Question 20
What is the default frequency of SD-WAN probes sent between VPN peers in a Cisco Meraki MX SD-WAN deployment?
- 10 milliseconds
- 100 milliseconds
- 1 second
- 10 seconds
Correct answer: C
Question 21
Drag and drop the settings from the left onto the OS system or systems that support it on the right. Settings can be used more than once.
Correct answer: To work with this question, an Exam Simulator is required.
Question 22
Refer to the exhibit. Which two configurations are needed to successfully monitor custom applications that a user is accessing using Cisco Meraki Insight? (Choose two.)
- The custom application uses TLS on any ports.
- The custom application uses HTTP on port 8080.
- The custom application uses HTTPS on TCP 443.
- The custom application uses SMB/CIFS.
- The custom application uses HTTPS on port 8080.
Correct answer: BC
Question 23
Which enrollment method must be used when containerization is required on BYOD Android devices managed by Systems Manager?
- Systems Manager network ID
- Android Enterprise utilizing a Work Profile
- Android Business utilizing a BYOD Profile
- Systems Manager container ID
Correct answer: B
Question 24
What is out of scope when considering the best practices for high-density wireless designs?
- number of SSIDs
- maximum beamforming
- band selection
- minimum bitrate
Correct answer: B
Question 25
Drag and drop the steps from the left into the sequence on the right to manage device control, according to Cisco Meraki best practice.
Correct answer: To work with this question, an Exam Simulator is required.
Question 26
When an SSID is configured with Sign-On Splash page enabled, which two settings must be configured for unauthenticated clients to have full network access and not be allow listed? (Choose two.)
- Controller disconnection behavior
- Captive Portal strength
- Simultaneous logins
- Firewall & traffic shaping
- RADIUS for splash page settings
Correct answer: AB
Question 27
Drag and drop the settings from the left onto the available or non-available methods of applying a group policy to a Cisco Meraki MR access point on the right.
Correct answer: To work with this question, an Exam Simulator is required.
Question 28
When deploying network-wide alerts, which three active alerting techniques can be sent from the Cisco Meraki dashboard? (Choose three.)
- Email
- Event logs
- Change logs
- Webhooks
- Teams
- SMS
Correct answer: ADF
Question 29
There will be 700 concurrent users streaming video to their laptops. A 30/70 split between 2.4 GHz and 5 GHz RF bands is expected. Using a ratio of 50 clients per AP, roughly how many (rounded to the nearest whole number) APs are needed?
- 6
- 7
- 9
- 10
Correct answer: D
Question 30
A customer needs inline traffic tagging to assign a Security Group Tag (SGT) that identifies the group from which the source traffic originates. Which feature provides this capability?
- Software Defined Access
- Rapid Threat Containment
- Secure Connect
- Adaptive Policy
Correct answer: D
Question 31
A Cisco Meraki MV camera monitors an office, and its field of vision currently captures work desks and employee computer screens. However, recording employee computer screens is prohibited by local regulation. Which feature in Dashboard should be used to preserve the current position of the camera while also meeting regulation requirements?
- area or interest
- zone exclusion
- privacy window
- sensor crop
Correct answer: C
Question 32
Company iPads are enrolled in Systems Manager without supervision, and profiles are pushed through Systems Manager.
Which outcome occurs when a user attempts to remove the “Meraki Management” profile on an iPad?
- The “Meraki Management” profile cannot be removed.
- The “Meraki Management” profile is removed and then pushed automatically by Systems Manager.
- The “Meraki Management” profile is removed. All the profiles that Systems Manager pushed are also removed.
- The “Meraki Management” profile is removed. All the profiles Systems Manager pushed remain.
Correct answer: C
Question 33
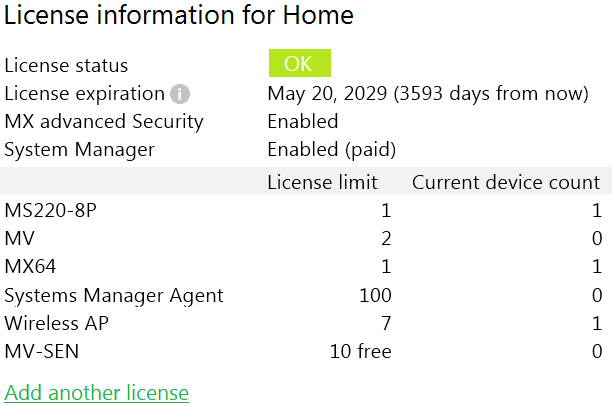
Refer to the exhibit. This Dashboard organization uses Co-Termination licensing model.
What happens when an additional seven APs are claimed on this network without adding licenses?
- All APs immediately stop functioning.
- All network devices stop functioning in 30 days.
- One AP Immediately stops functioning.
- All APs stop functioning in 30 days.
Correct answer: B
Question 34
Which Cisco Meraki product must be deployed in addition to Systems Manager so that Systems Manager Sentry enrollment can be used?
- MS Switch
- Meraki Insight
- MR Access Point
- MV Smart Camera
Correct answer: C
Question 35
Which VLAN is used to source pings across the site-to-site VPN when using the MX Live tools?
- highest VLAN ID that is configured and set to NO to use VPN
- lowest VLAN ID that is configured and set to YES to use VPN
- highest VLAN ID that is configured and set to YES to use VPN
- lowest VLAN ID configured and set to NO to use VPN
Correct answer: C
Question 36
What are two roles of the network and device tags in a Dashboard? (Choose two.)
- Tags enable administrators to configure a combination of network and device specific tags to create summary reports filtered for specific devices across multiple networks.
- Network tags can be used to assign networks to separate Auto VPN domains in an Organization with many networks.
- Network tags can be used to simplify the assignment of network-level permissions in an Organization with many networks.
- Device tags can be used to simplify the assignment of device-level permissions in an Organization with many administrators.
- Device tags can be assigned to MR APs to influence the gateway selection for repeaters in a mesh wireless network.
Correct answer: AC
Question 37
Which three verbs of request are available in the Cisco Meraki API? (Choose three.)
- SET
- PUT
- PATCH
- ADD
- POST
- GET
Correct answer: BEF
Question 38
Where should a network admin navigate to investigate wireless mesh information between Meraki APs?
- Wireless > Monitor > Access Points > AP > RF
- Wireless > Configure > Radio Settings
- Wireless > Monitor > Wireless Health
- Wireless > Monitor > RF Spectrum
Correct answer: A
Question 39
Which design requirement is met by implementing syslog versus SNMP?
- when automation capabilities are needed
- when proactive alerts for critical events must be generated
- when organization-wide information must be collected
- when information such as flows and client connectivity must be gathered
Correct answer: D
Question 40
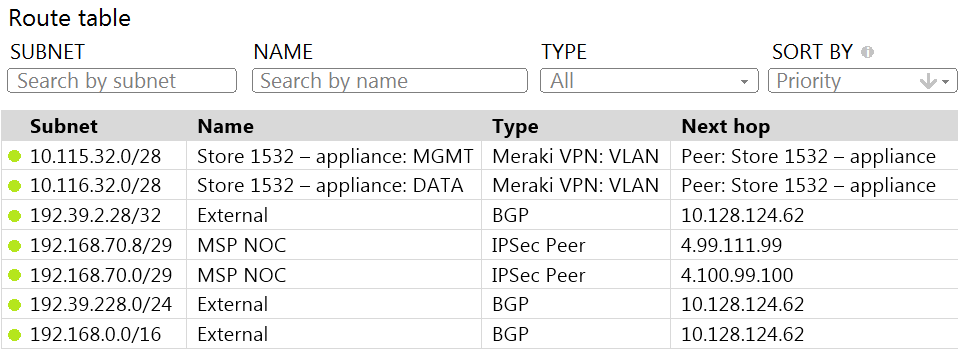
Refer to the exhibit. A packet arrives on the VPN concentrator with source IP 10.168.70.3 and destined for IP 10.116.32.4.
What is the next hop for the packet, based on this concentrator routing table?
- The concentrator gateway (10.128.124.62) is the next hop.
- Not enough detail is available to determine the next hop.
- The packet is stopped.
- The Auto VPN peer “Store 1532 – appliance” is the next hop.
Correct answer: D
Question 41
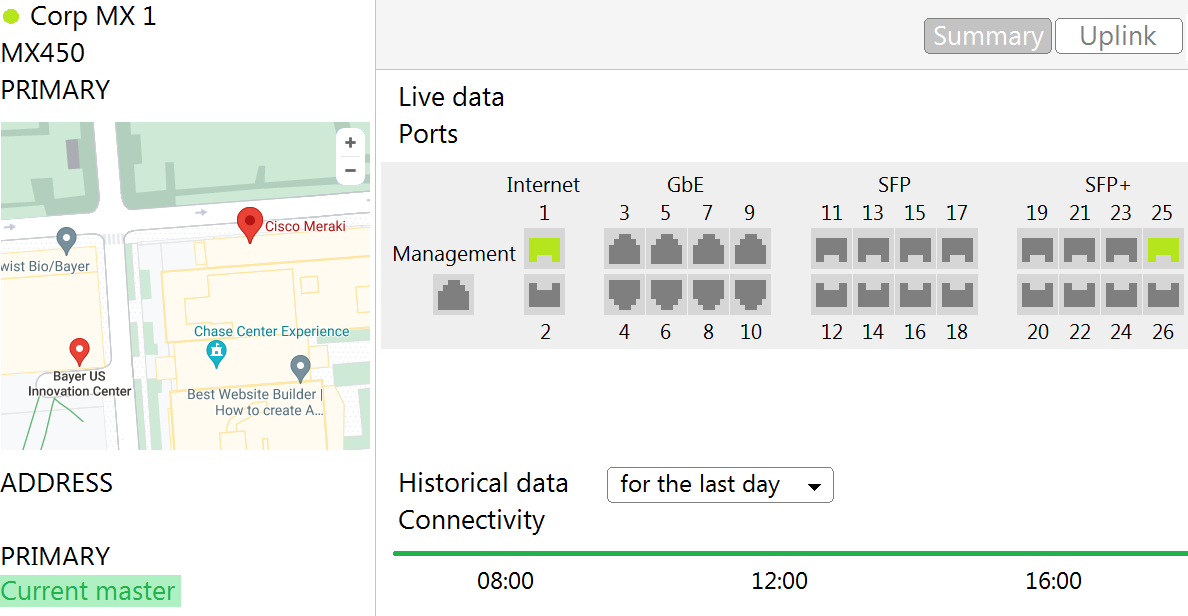
Refer to the exhibit. The VPN concentrator is experiencing issues.
Which action should be taken to ensure a stable environment?
- Add a deny any/any firewall rule to the end of the firewall rules.
- Remove the connection from Internet 1.
- Physically disconnect all LAN ports.
- Configure the MX appliance to Routed mode on the Addressing & VLANS page.
Correct answer: C
Question 42
Which two actions can extend the video retention of a Cisco Meraki MV Smart Camera? (Choose two.)
- enabling audio compression
- installing an SSD memory extension
- enabling motion-based retention
- enabling maximum retention limit
- configuring a recording schedule
Correct answer: CE
Question 43
A new application needs to be pushed to all iOS devices. Some devices report “NotNow” in the event log and do not install the application.
What does the “NotNow” event indicate?
- The application requires the most recent iOS version.
- The device is locked with a passcode.
- The device cannot connect to Apple servers.
- The device cannot connect to Cisco Meraki servers.
Correct answer: B
Question 44
Which Meraki Dashboard menu section is accessed to enable Sentry enrollment on an SSID?
- Wireless > Configure > Access Control
- Wireless > Configure > Splash page
- Wireless > Configure > Firewall & Traffic Shaping
- Wireless > Configure > SSIDs
Correct answer: A
Question 45
Which order is accurate for a firmware upgrade on MX appliances in a high-availability configuration?
- starts on the secondary MX appliance and then occurs on the primary MX appliance
- starts on both MX appliances at the same time and then reboots both appliances after traffic on the primary MX appliance ceases
- starts on both MX appliances at the same time and then immediately reboots both appliances
- starts on the primary MX appliance and then occurs on the secondary MX appliance
Correct answer: D
Question 46
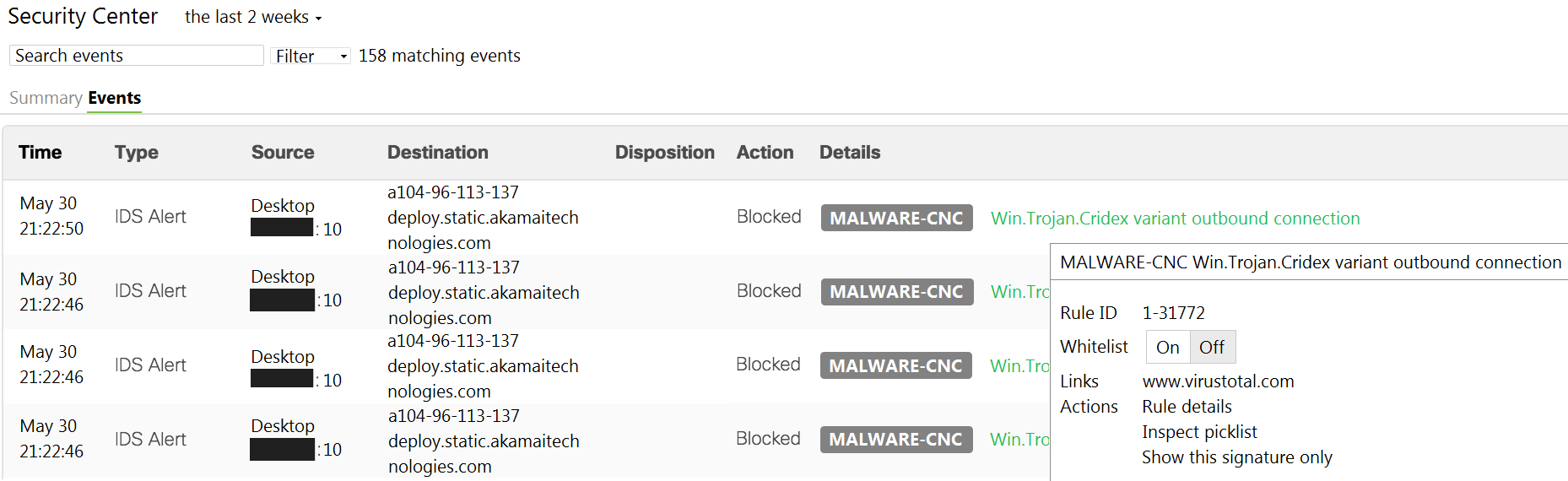
Refer to the exhibit. Which IDS/IPS mode is the MX Security Appliance configured for?
- quarantine
- prevention
- detection
- blocking
Correct answer: B
Question 47
When wireless SSIDs are configured in Dashboard, which setting on the Access Control page affects the ability of a 2.4 GHz only client device from associating to the WLAN for the first time?
- Content filtering
- Bridge mode
- 802.11r
- Dual band operating with Band Steering
Correct answer: D
Question 48
Which type of authentication protocol is used when using OSPF on an MX appliance?
- MD5
- certificate
- plaintext
- SHA-1
Correct answer: A
Question 49
Which requirement is needed to implement Fast Lane on Cisco Meraki APs?
- wireless profile installed on an Apple iOS device
- wireless profile installed on a Cisco iOS access point
- adaptive 802.11r disabled
- traffic shaping rule tagging traffic with a DSCP value of 46 to Apple.com
Correct answer: A
Question 50
Air Marshal has contained a malicious SSID.
What are two effects on connectivity? (Choose two.)
- Currently associated clients stay connected.
- New clients can connect.
- Currently associated clients are affected by restrictive traffic shaping rules.
- New clients cannot connect.
- Currently associated clients are disconnected.
Correct answer: DE
Question 51
What is the role of the Meraki Dashboard as the service provider when using SAML for single sign-on to the Dashboard?
- The Dashboard generates the SAML request.
- The Dashboard provides user access credentials.
- The Dashboard parses the SAML request and authenticates users.
- The Dashboard generates the SAML response.
Correct answer: A
Question 52
What are two organization permission types? (Choose two.)
- Full
- Read-only
- Monitor-only
- Write
- Write-only
Correct answer: AB
Question 53
In an organization that uses the Co-Termination licensing model, which two operations enable licenses to be applied? (Choose two.)
- Renew the Dashboard license.
- License a network.
- License more devices.
- Call Meraki support.
- Wait for the devices to auto-renew.
Correct answer: AC
Question 54
For which two reasons can an organization become “Out of License”? (Choose two.)
- licenses that are in the wrong network
- more hardware devices than device licenses
- expired device license
- licenses that do not match the serial numbers in the organization
- MR licenses that do not match the MR models in the organization
Correct answer: BC
Question 55
What is a feature of distributed Layer 3 roaming?
- An MX Security Appliance is not required as a concentrator.
- An MX Security Appliance is required as a concentrator.
- All wireless client traffic can be split-tunneled.
- All wireless client traffic is tunneled.
Correct answer: A
Question 56
How is high-availability supported for Cisco Meraki devices?
- Only the MX Security Appliances that use VRRP support high availability.
- An active/active high-availability pair is recommended for MX Security Appliances.
- The MX Security Appliances and MS Series Switches that use VRRP support an active/passive high-availability pair.
- The MX Security Appliances and MS Series Switches that use HSRP support an active/passive high-availability pair.
Correct answer: C
Question 57
Which two Systems Manager Live tools are available only for Apple Macs and Windows PCs and cannot be used on iOS or Android mobile devices? (Choose two.)
- OS updates
- Send notification
- Selective wipe
- Screenshot
- Remote Desktop
Correct answer: DE
Question 58
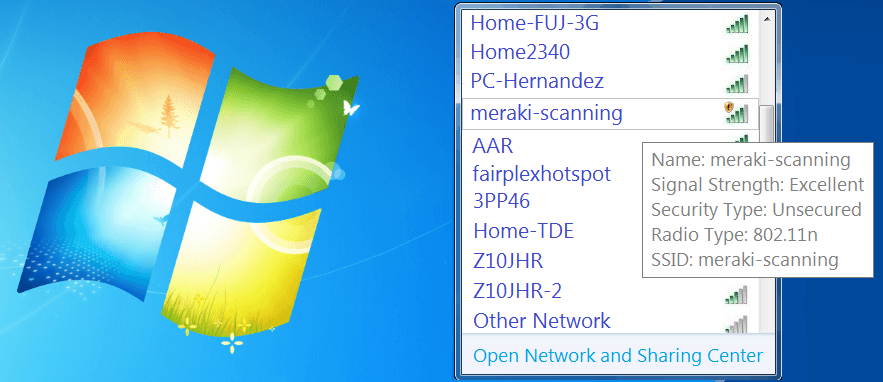
Refer to the exhibit. During a Meraki AP deployment, the default SSID that the exhibit shows is broadcast.
What causes this behavior?
- An AP does not have a wired connection to the network.
- An AP cannot connect to the default gateway.
- An AP has never connected to the Meraki Cloud Controller.
- An AP has Site Survey mode enabled.
Correct answer: B
Question 59
Which Cisco Meraki best practice method preserves complete historical network event logs?
- Configuring the preserved event number to maximize logging.
- Configuring the preserved event period to unlimited.
- Configuring a syslog server for the network.
- Configuring Dashboard logging to preserve only certain event types.
Correct answer: C
Question 60
Which two features and functions are supported when using an MX appliance in Passthrough mode? (Choose two.)
- intrusion prevention
- site-to-site VPN
- secondary uplinks
- DHCP
- high availability
Correct answer: AB
Question 61
A customer wants to use Microsoft Azure to host corporate application servers.
Which feature does the customer get by using a vMX appliance rather than connecting directly to Azure by VPN?
- malware protection
- SD-WAN
- next-generation firewall
- intrusion prevention
Correct answer: B
Question 62
Which API endpoint clones a new Organization?
- POST /organizations/clone/{organizationId}
- PUT /organizations/{organizationId}/clone
- POST /organizations/{organizationId}/new
- POST /organizations/{organizationId}/clone
Correct answer: D
Question 63
Drag and drop the settings from the left into the boxes on the right to indicate if the setting will be cloned or not cloned using the Cisco Meraki MS switch cloning feature.
Correct answer: To work with this question, an Exam Simulator is required.
Question 64
What occurs when a configuration change is made to an MX network that is bound to a configuration template?
- The configuration change in the bound network is combined with the template configuration inside the template.
- The more restrictive configuration is preferred.
- The configuration change in the bound network overrides the template configuration.
- The template configuration overrides the configuration change in the bound network.
Correct answer: C
Question 65
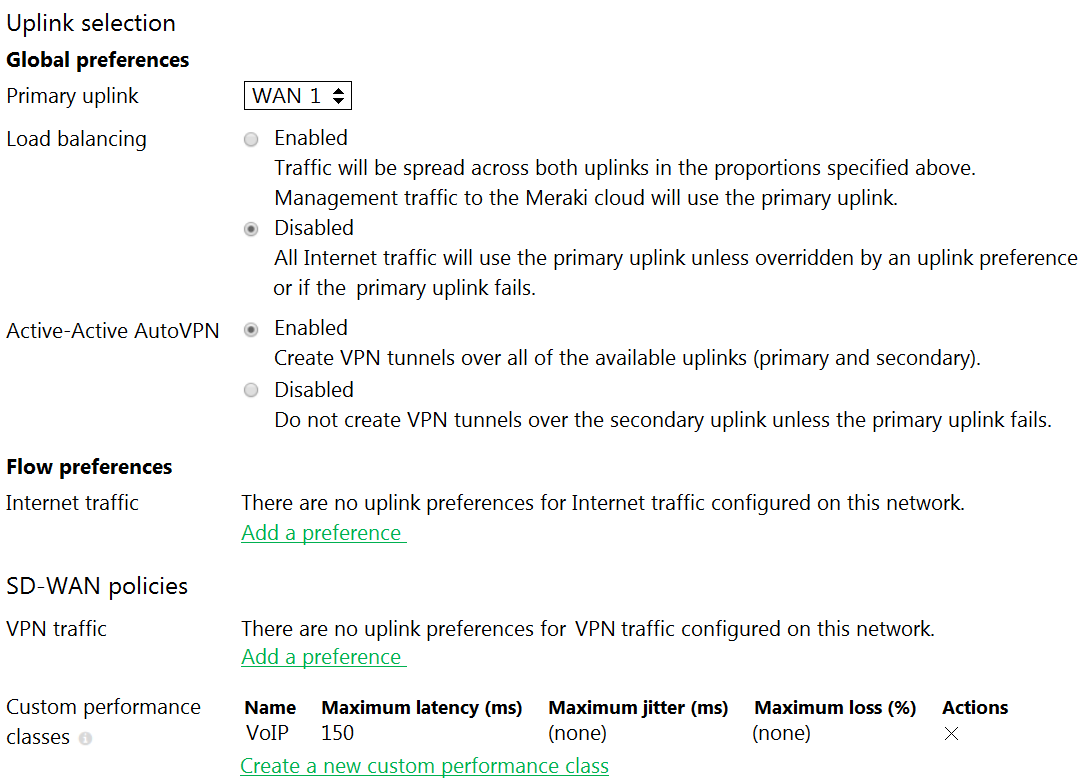
Refer to the exhibit. What does the MX Security Appliance send to determine whether VPN traffic exceeds the configured latency threshold in the VoIP custom performance class?
- 1000-byte TCP probes every second, through VPN tunnels that are established over the primary WAN link.
- 100-byte UDP probes every second, through VPN tunnels that are established over every WAN link.
- 100-byte UDP probes every second, through VPN tunnels that are established over the primary WAN link.
- 1000-byte TCP probes every second, through VPN tunnels that are established over every WAN link.
Correct answer: B
Question 66
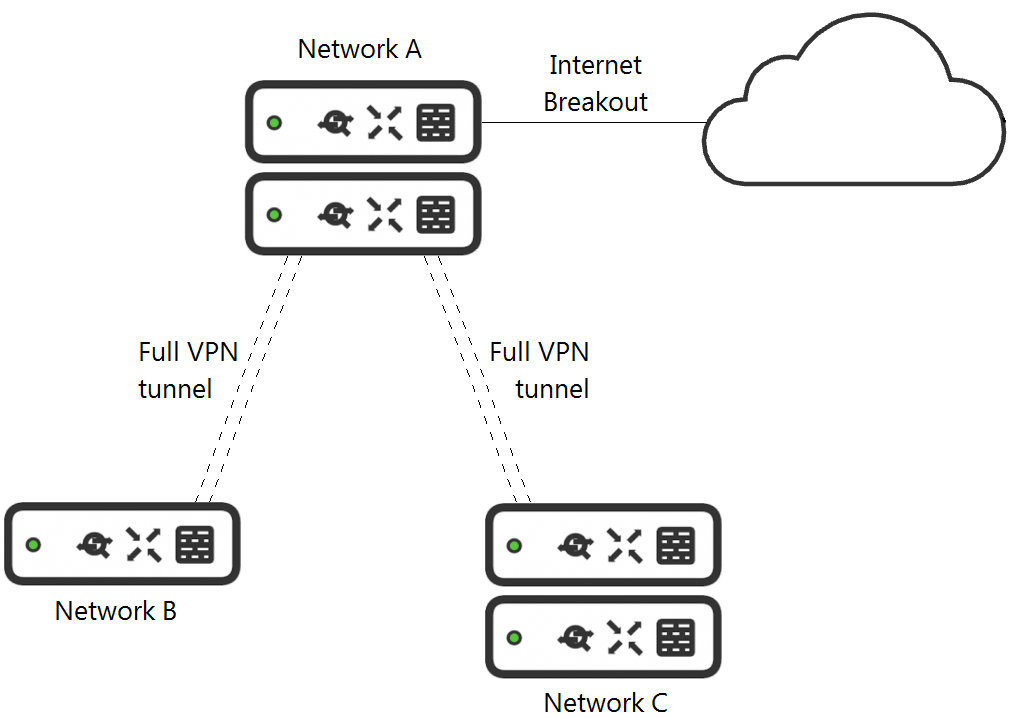
Refer to the exhibit. What is the minimal Cisco Meraki Insight licensing requirement?
- A single Meraki Insight license must be configured on network A to gain Web App Health visibility on network B.
- A single Meraki Insight license must be configured on network B to gain Web App Health visibility on network B.
- A single Meraki Insight license must be configured on network A, and a single license must be configured on network B, to gain Web App Health visibility on network B.
- Two Meraki Insight licenses must be configured on network A to gain Web App Health visibility on network B.
- Two Meraki Insight licenses must be configured on network A and a single license must be configured on network B, to gain Web App Health visibility on network B.
Correct answer: B
Question 67
Which configuration step is necessary when automatic updating is required of iOS apps provisioned through Systems Manager that are found in the App Store?
- No configuration step is necessary; automatic updating is the default behavior.
- Configure automatic updating of iOS devices in the Meraki installed profile.
- Create a security policy that enables automatic updates.
- Create a profile with automatic update enabled and apply it to iOS devices.
Correct answer: A
Question 68

Refer to the exhibit. Which outcome occurs when logging is set to Enabled?
- Outbound flows are sent to a configured syslog server if a syslog sender is configured for flows.
- The hits counter within this section is now enabled.
- This firewall rule is now enabled.
- Inbound flows are sent to a configured syslog server if a syslog server configured for flows.
Correct answer: A
Question 69
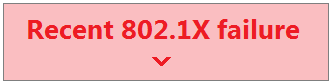
Refer to the exhibit. For an AP that displays this alert, which network access control method must be in use?
- preshared key
- WPA2-enterprise with my RADIUS server
- splash page with my RADIUS server
- MAC-based access control with RADIUS server
Correct answer: B
Question 70
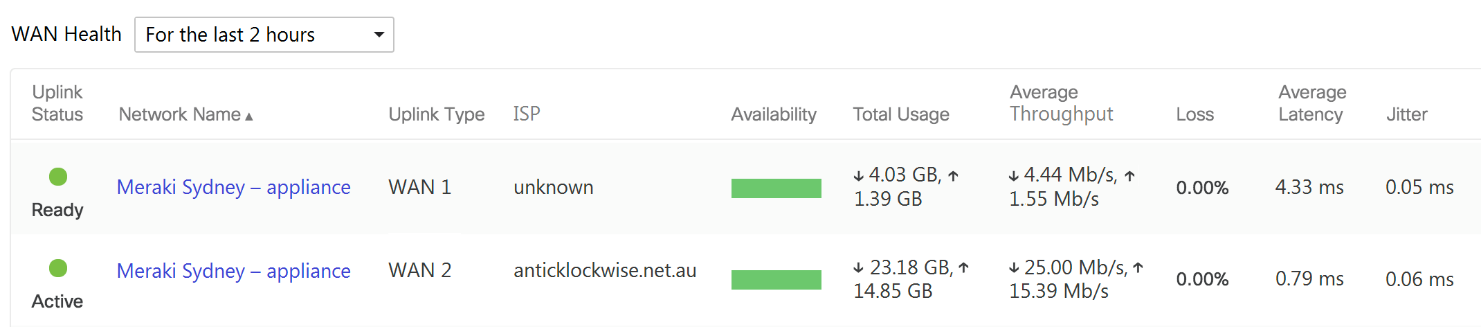
Refer to the exhibit. What are the Loss and Average Latency statistics based on?
- responses that the MX appliance receives on the connectivity-testing hostnames on the Insight > Web App Health page
- responses that the MX appliance receives on the connectivity-testing IP addresses on the Security & SD-WAN > Firewall page
- responses that the MX appliance receives on the connectivity-testing IP address that is configured on the Security & SD-WAN > SD-WAN & Traffic Shaping page
- responses that the MX appliance receives on the connectivity-testing IP addresses on the Help > Firewall info page
Correct answer: C
Question 71
A customer requires a hub-and-spoke Auto VPN deployment with two NAT-mode hubs with dual uplink connections and 50 remote sites with a single uplink connection.
How many tunnels does each hub need to support?
- 52
- 54
- 100
- 104
Correct answer: D
Question 72
Which information is used to calculate whether a WAN link has high usage?
- data under Security & SD WAN > Appliance Status > Uplink > Live Data
- total historical throughput of an uplink
- total number of devices that are actively passing traffic
- value under Security & SD WAN > SD WAN & Traffic Shaping > Uplink Configuration
Correct answer: D
Question 73
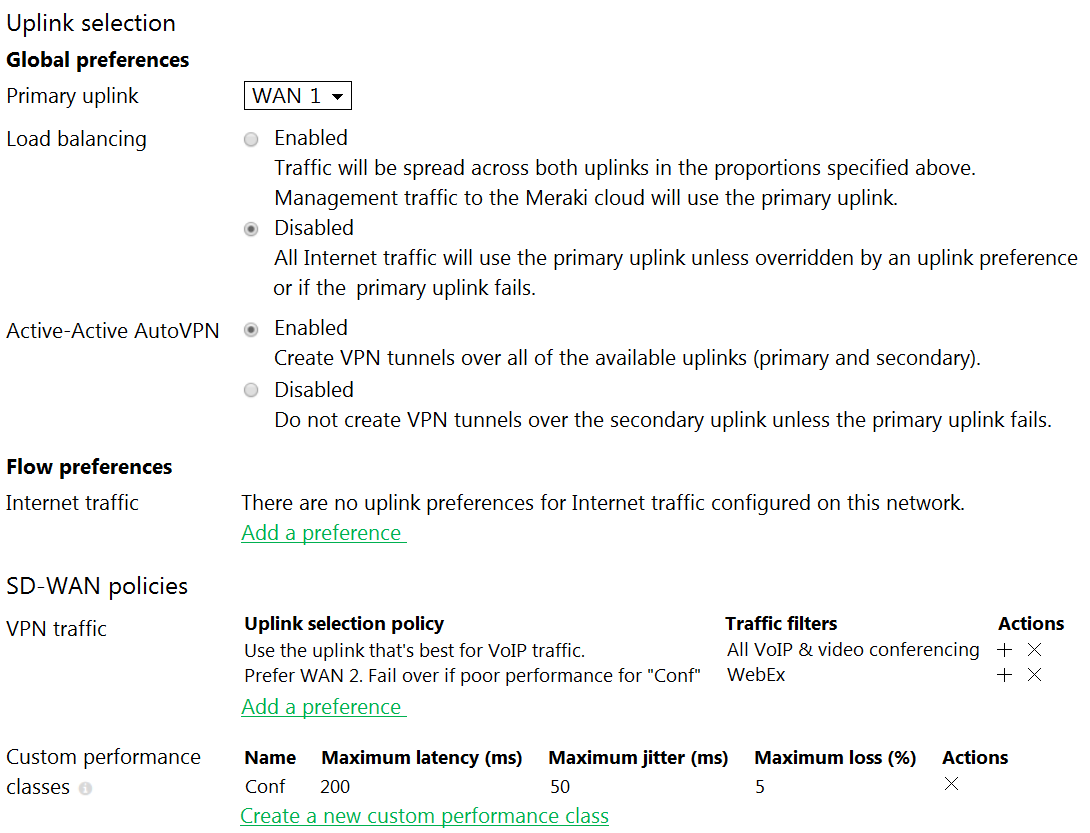
Refer to the exhibit. Assuming this MX has established a full tunnel with its VPN peer, how will the MX route the WebEx traffic?
- WebEx traffic will prefer WAN 2 as long as it meets the thresholds in the “Conf” performance class.
- WebEx traffic will prefer WAN 1 as it is the primary uplink.
- WebEx traffic will prefer WAN 2 as long as it is up.
- WebEx traffic will be load-balanced between both active WAN links.
Correct answer: B
Question 74
A Cisco Meraki MV camera is monitoring an office and its field of vision currently captures work desks and employee computer screens. However, recording employee computer screens is prohibited by local regulation.
Which feature in Dashboard can be used to preserve the current position of the camera while also meeting regulation requirements?
- zone exclusion
- privacy window
- area or interest
- sensor crop
- restricted mode
Correct answer: B
Question 75
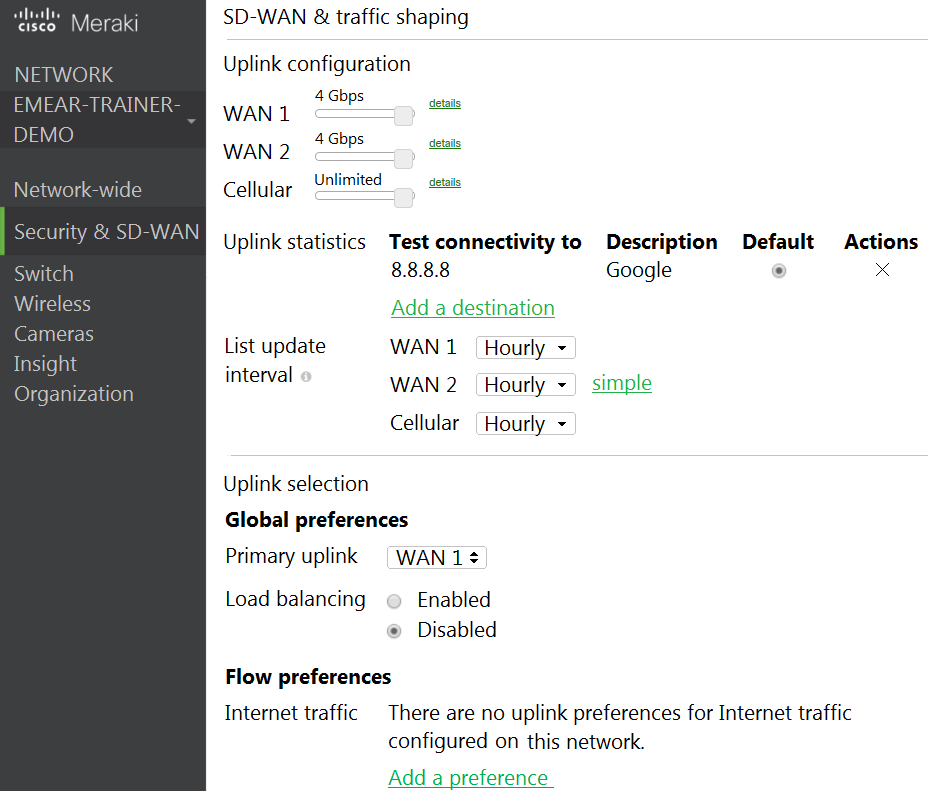
Refer to the exhibit. Which two actions are required to optimize load balancing asymmetrically with a 4:1 ratio between links? (Choose two.)
- Change the primary uplink to "none".
- Add an internet traffic preference that defines the load-balancing ratio as 4:1.
- Enable load balancing.
- Set the speed of the cellular uplink to zero.
- Change the assigned speeds of WAN 1 and WAN 2 so that the ratio is 4:1.
Correct answer: CE
Question 76
How does a Meraki device behave if cloud connectivity is temporarily lost?
- The offline device continues to run with its last known configuration until cloud connectivity is restored.
- The offline device reboots every 5 minutes until connection is restored.
- The offline device stops passing traffic.
- The offline device tries to form a connection with a local backup sever.
Correct answer: A
Question 77
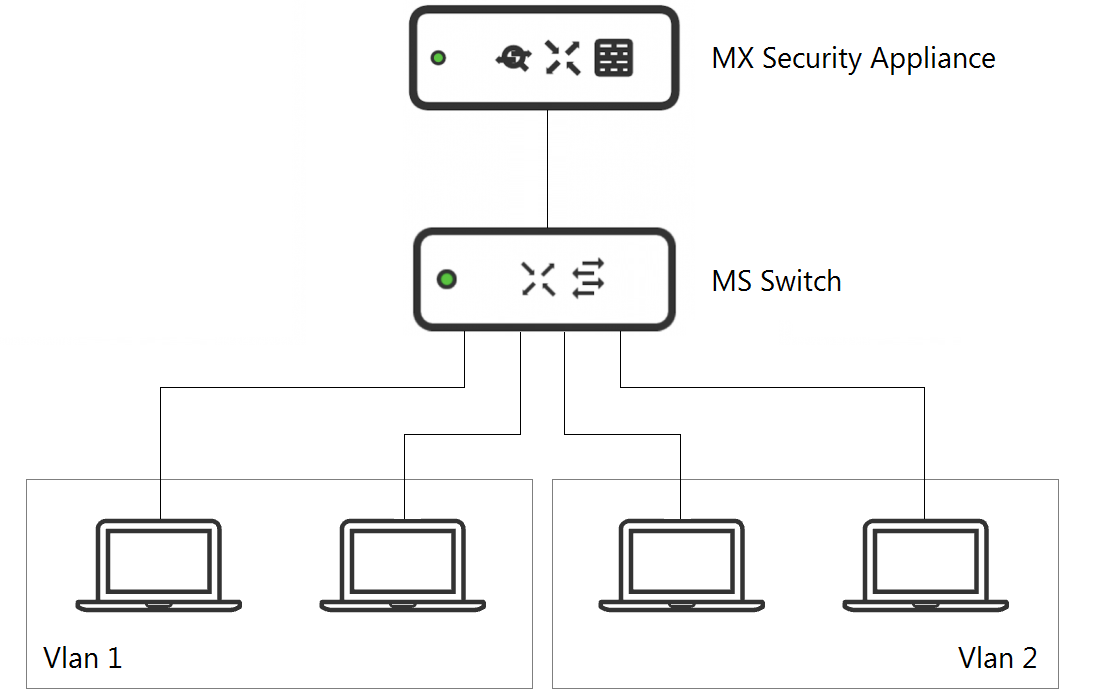
Refer to the exhibit. What is an advantage of implementing inter-VLAN routing on an MX Security Appliance rather than performing inter-VLAN routing on an MS Series Switch?
- The MX appliance performs IDS/IPS for inter-VLAN traffic.
- The MX appliance performs AMP for inter-VLAN traffic.
- The MX appliance performs data encryption for inter-VLAN traffic.
- The MX appliance performs content filtering for inter-VLAN traffic.
Correct answer: A
Question 78
Drag and drop the descriptions from the left onto the corresponding MX operation mode on the right.
Correct answer: To work with this question, an Exam Simulator is required.
Question 79
Which information do the MXs in a High Availability pair share?
- spanning-tree state
- time synchronization state
- DHCP association database
- stateful firewall database
Correct answer: C
Question 80
One thousand concurrent users stream video to their laptops. A 30/70 split between 2.4 GHz and 5 GHz is used.
Based on client count, how many APs (rounded to the nearest whole number) are needed?
- 26
- 28
- 30
- 32
Correct answer: B
Question 81
What are two ways peers interact with ports that Auto VPN uses? (Choose two.)
- For IPsec tunneling, peers use high UDP ports within the 32768 to 61000 range.
- Peers contact the VPN registry at UDP port 9350.
- For IPsec tunneling, peers use high TCP ports within the 32768 to 61000 range.
- Peers contact the VPN registry at TCP port 9350.
- For IPsec tunneling, peers use UDP ports 500 and 4500.
Correct answer: AB
Question 82
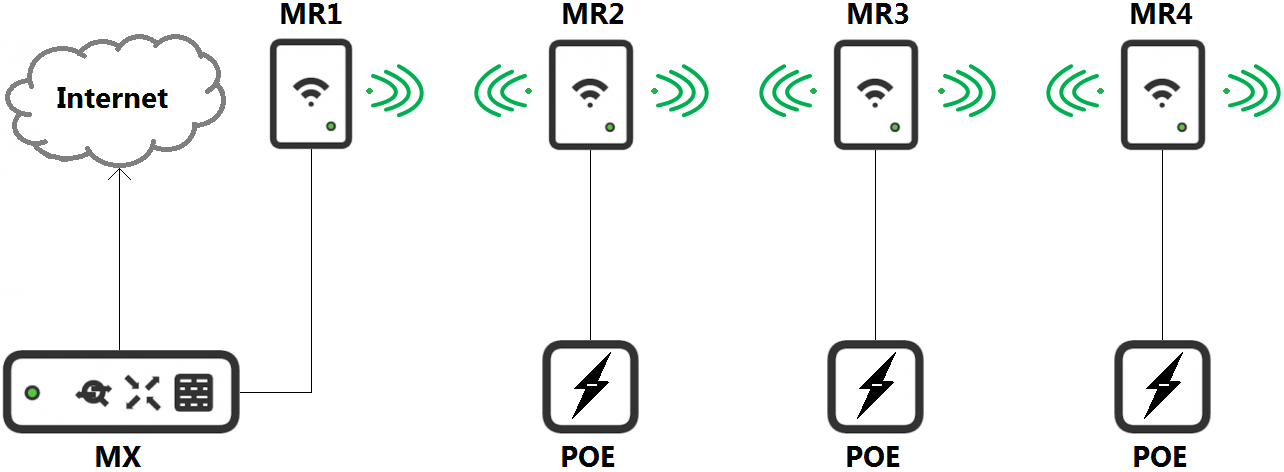
Refer to the exhibit. Which design recommendation should be considered?
- A 25-percent throughput loss occurs for every hop. Cisco Meraki best practice recommends a 1-hop maximum.
- A 25-percent throughput loss occurs for every hop. Cisco Meraki best practice recommends a 2-hop maximum.
- A 50-percent throughput loss occurs for every hop. Cisco Meraki best practice recommends a 1-hop maximum.
- A 50-percent throughput loss occurs for every hop. Cisco Meraki best practice recommends a 2-hop maximum.
Correct answer: C
Question 83
What is the best practice Systems Manager enrollment method when deploying corporate-owned iOS devices?
- manual
- Apple Configurator
- Sentry enrollment
- DEP
Correct answer: D
Question 84
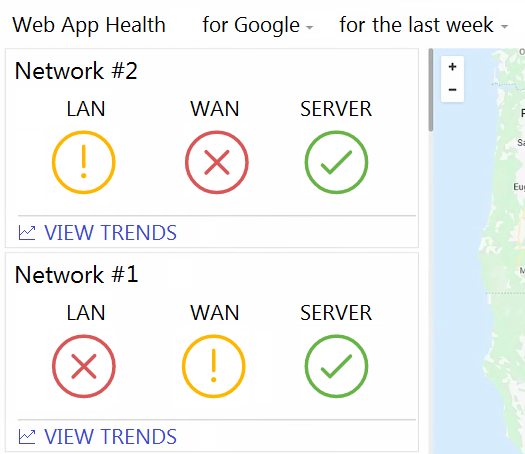
Refer to the exhibit. What are two outcomes reflected in the Web App Health application? (Choose two.)
- Users on both networks may be experiencing issues when attempting to reach Google.
- Network #1 could not load Google because of a remote server issue.
- Network #2 had better application performance than Network #1.
- Network #2 could not load Google because of a local client misconfiguration.
- Neither network recorded any server-side performance issues.
Correct answer: AE
Question 85
Which two primary metrics does Meraki Insight use to calculate the Application Performance Score? (Choose two.)
- Maximum Jitter
- Total Bandwidth Usage
- Maximum Latency
- Per-flow Goodput
- Application Response Time
Correct answer: DE
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!




