Download Implementing and Operating Cisco Security Core Technologies.350-701.DumpsBase.2021-05-10.102q.vcex
| Vendor: | Cisco |
| Exam Code: | 350-701 |
| Exam Name: | Implementing and Operating Cisco Security Core Technologies |
| Date: | May 10, 2021 |
| File Size: | 906 KB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Which feature requires a network discovery policy on the Cisco Firepower Next Generation Intrusion Prevention System?
- security intelligence
- impact flags
- health monitoring
- URL filtering
Correct answer: A
Question 2
Refer to the exhibit.
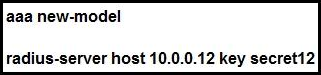
Which statement about the authentication protocol used in the configuration is true?
- The authentication request contains only a password
- The authentication request contains only a username
- The authentication and authorization requests are grouped in a single packet.
- There are separate authentication and authorization request packets.
Correct answer: C
Question 3
Which two preventive measures are used to control cross-site scripting? (Choose two.)
- Enable client-side scripts on a per-domain basis.
- Incorporate contextual output encoding/escaping.
- Disable cookie inspection in the HTML inspection engine.
- Run untrusted HTML input through an HTML sanitization engine.
- SameSite cookie attribute should not be used.
Correct answer: AB
Question 4
Which policy is used to capture host information on the Cisco Firepower Next Generation Intrusion Prevention System?
- correlation
- intrusion
- access control
- network discovery
Correct answer: D
Question 5
Refer to the exhibit.
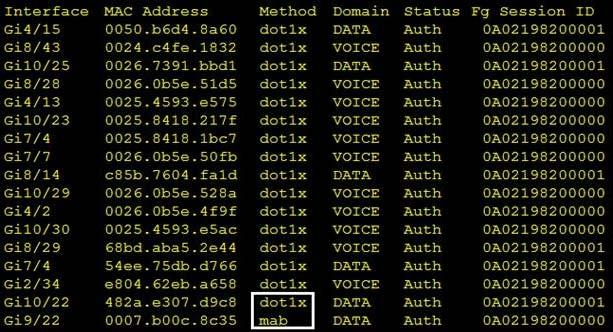
Which command was used to generate this output and to show which ports are authenticating with dot1x or mab?
- show authentication registrations
- show authentication method
- show dot1x all
- show authentication sessions
Correct answer: B
Question 6
An engineer is configuring a Cisco ESA and wants to control whether to accept or reject email messages to a recipient address.
Which list contains the allowed recipient addresses?
- SAT
- BAT
- HAT
- RAT
Correct answer: D
Question 7
Which two capabilities does TAXII support? (Choose two.)
- exchange
- pull messaging
- binding
- correlation
- mitigating
Correct answer: BC
Question 8
Which policy represents a shared set of features or parameters that define the aspects of a managed device that are likely to be similar to other managed devices in a deployment?
- group policy
- access control policy
- device management policy
- platform service policy
Correct answer: D
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/firepower/622/configuration/guide/fpmc-config-guide-v622/platform_settings_policies_for_managed_devices.pdf Reference:
https://www.cisco.com/c/en/us/td/docs/security/firepower/622/configuration/guide/fpmc-config-guide-v622/platform_settings_policies_for_managed_devices.pdf
Question 9
An administrator wants to ensure that all endpoints are compliant before users are allowed access on the corporate network. The endpoints must have the corporate antivirus application installed and be running the latest build of Windows 10.
What must the administrator implement to ensure that all devices are compliant before they are allowed on the network?
- Cisco Identity Services Engine and AnyConnect Posture module
- Cisco Stealthwatch and Cisco Identity Services Engine integration
- Cisco ASA firewall with Dynamic Access Policies configured
- Cisco Identity Services Engine with PxGrid services enabled
Correct answer: A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect46/administration/guide/b_AnyConnect_Administrator_Guide_4-6/configure-posture.html Reference:
https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect46/administration/guide/b_AnyConnect_Administrator_Guide_4-6/configure-posture.html
Question 10
What are two Detection and Analytics Engines of Cognitive Threat Analytics? (Choose two.)
- data exfiltration
- command and control communication
- intelligent proxy
- snort
- URL categorization
Correct answer: AB
Explanation:
Reference: https://www.cisco.com/c/dam/en/us/products/collateral/security/cognitive-threat-analytics/at-a-glance-c45-736555.pdf Reference:
https://www.cisco.com/c/dam/en/us/products/collateral/security/cognitive-threat-analytics/at-a-glance-c45-736555.pdf
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



