Download Designing Cisco Enterprise Networks (300-420 ENSLD).300-420.BrainDumps.2020-10-05.86q.vcex
| Vendor: | Cisco |
| Exam Code: | 300-420 |
| Exam Name: | Designing Cisco Enterprise Networks (300-420 ENSLD) |
| Date: | Oct 05, 2020 |
| File Size: | 4 MB |
| Downloads: | 2 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
What command would display a single line of information for each virtual gateway or virtual forwarder on a switch?
- switch# show glbp
- switch# show glbp brief
- switch# show standby
- switch# show standby brief
Correct answer: B
Explanation:
A brief single line view of virtual forwarder and virtual gateway information is provided with the command show glbp brief. Virtual forwarders and virtual gateways are terms used for GLBP groups. A brief output of GLBP information is provided with the brief key word. This output includes the interface, priority, state, and address of GLBP interfaces on the switch.The command show glbp displays detailed information about GLBP groups on the switch. This information includes the GLBP groups the switch is a member of, whether this is the active switch, the virtual IP address, and whether preemption is enabled.The command show standby brief is used to display a summary of the HSRP groups to which the switch belongs. The summary information it provides includes the group number, priority, state, active device address, standby address, and group address. This command is for HSRP only.The command show standby can be used to display detailed information about HSRP groups to which a switch belongs. This command is for HSRP only.Objective: Infrastructure Services Sub-Objective:Configure and verify first-hop redundancy protocolsReferences:Cisco > Cisco IOS IP Application Services Configuration Guide, Release 12.4 > Part 1: First Hop Redundancy Protocols > Configuring GLBP Cisco > Cisco IOS IP Application Services Command Reference > show glbp A brief single line view of virtual forwarder and virtual gateway information is provided with the command show glbp brief. Virtual forwarders and virtual gateways are terms used for GLBP groups. A brief output of GLBP information is provided with the brief key word. This output includes the interface, priority, state, and address of GLBP interfaces on the switch.
The command show glbp displays detailed information about GLBP groups on the switch. This information includes the GLBP groups the switch is a member of, whether this is the active switch, the virtual IP address, and whether preemption is enabled.
The command show standby brief is used to display a summary of the HSRP groups to which the switch belongs. The summary information it provides includes the group number, priority, state, active device address, standby address, and group address. This command is for HSRP only.
The command show standby can be used to display detailed information about HSRP groups to which a switch belongs. This command is for HSRP only.
Objective:
Infrastructure Services Sub-Objective:
Configure and verify first-hop redundancy protocols
References:
Cisco > Cisco IOS IP Application Services Configuration Guide, Release 12.4 > Part 1: First Hop Redundancy Protocols > Configuring GLBP Cisco > Cisco IOS IP Application Services Command Reference > show glbp
Question 2
Which command enables GLBP on an interface?
- glbp
- glbp 10 ip 192.168.1.1
- standby mode glbp
- switchport mode glbp
Correct answer: B
Explanation:
The glbp ip interface configuration command enables Group Load Balancing Protocol (GLBP). The syntax for this command is as follows:switch(config-if)# glbp group-number ip ip-addressThe following example activates GLBP for group 5 on Fast Ethernet interface 1/0. The virtual IP address to be used by the GLBP group is set to 10.5.5.5. The default gateway of each host should be set to the virtual IP address.switch(config)# interface FastEthernet 1/0 switch(config-if)# ip address 10.5.5.1 255.255.255.0 switch(config-if)# glbp 5 ip 10.5.5.5GLBP is a Cisco-designed protocol that provides for the dynamic use of redundant routers in a broadcast network. It differs from HSRP and VRRP in that it is not necessary to configure multiple groups to fully use redundant paths or routers. GLBP has a configurable load-balancing mechanism that will distribute the use of redundant gateways servicing a broadcast network such as an Ethernet LAN. When a host issues an ARP to resolve its gateway's MAC address, the active virtual gateway (AVG) will respond with the virtual MAC address of a selected active virtual forwarder (AVF). The AVG will perform load balancing by varying which virtual MAC it selects to use in the response. The AVF will own that assigned virtual MAC as long as the gateway is active. If an AVF becomes unable to provide service as gateway, then another AVF can assume ownership of the virtual MAC. Objective:Infrastructure Services Sub-Objective:Configure and verify first-hop redundancy protocolsReferences:Cisco > Cisco IOS IP Application Services Configuration Guide, Release 12.4 > Part 1: First Hop Redundancy Protocols > Configuring GLBP The glbp ip interface configuration command enables Group Load Balancing Protocol (GLBP). The syntax for this command is as follows:
switch(config-if)# glbp group-number ip ip-address
The following example activates GLBP for group 5 on Fast Ethernet interface 1/0. The virtual IP address to be used by the GLBP group is set to 10.5.5.5. The default gateway of each host should be set to the virtual IP address.
switch(config)# interface FastEthernet 1/0 switch(config-if)# ip address 10.5.5.1 255.255.255.0 switch(config-if)# glbp 5 ip 10.5.5.5
GLBP is a Cisco-designed protocol that provides for the dynamic use of redundant routers in a broadcast network. It differs from HSRP and VRRP in that it is not necessary to configure multiple groups to fully use redundant paths or routers. GLBP has a configurable load-balancing mechanism that will distribute the use of redundant gateways servicing a broadcast network such as an Ethernet LAN. When a host issues an ARP to resolve its gateway's MAC address, the active virtual gateway (AVG) will respond with the virtual MAC address of a selected active virtual forwarder (AVF). The AVG will perform load balancing by varying which virtual MAC it selects to use in the response. The AVF will own that assigned virtual MAC as long as the gateway is active. If an AVF becomes unable to provide service as gateway, then another AVF can assume ownership of the virtual MAC.
Objective:
Infrastructure Services Sub-Objective:
Configure and verify first-hop redundancy protocols
References:
Cisco > Cisco IOS IP Application Services Configuration Guide, Release 12.4 > Part 1: First Hop Redundancy Protocols > Configuring GLBP
Question 3
What command disables 802.1x authentication on a port and permits traffic without authentication?
- dot1x port-control disable
- dot1x port-control force-unauthorized
- dot1x port-control auto
- dot1x port-control force-authorized
Correct answer: D
Explanation:
The command dot1x port-control force-authorized is used to disable 802.1x on a port and permit traffic without authentication. Dot1x ports are in one of two states, authorized or unauthorized. Authorized ports permit user traffic to flow through the port. This state usually follows successful authentication. Unauthorized ports only permit authorization traffic to flow through the port. Usually a port begins in the unauthorized state. A user is then allowed to exchange AAA authentication traffic with the port. Once the user has been authenticated successfully, the port is changed to the authorized state and the user is permitted to use the port normally.Normal use of 802.1x has the port configured with the dot1x port-control auto statement. This places the port in the unauthorized state until successful authentication. After successful authentication, the port is changed to the authorized state.When 802.1x is initially configured, the default port control of the ports is force-authorized. This forces the port to be in the authorized state without successful authentication. This setting disables the need for authentication and permits all traffic.The force-unauthorized keyword configures the port as an unauthorized port regardless of authentication traffic. A port configured with this key word would not permit user traffic, not even authentication traffic.The command dot1x port-control disable is not a valid command due to incorrect syntax. Objective:Infrastructure Security Sub-Objective:Describe device security using Cisco IOS AAA with TACACS+ and RADIUSReferences:Cisco > Catalyst 6500 Series Release 15.0SY Software Configuration Guide > Security > IEEE 802.1X Port-Based AuthenticationCisco > Catalyst 4500 Series Switch Cisco IOS Command Reference, 12.2(52)SG > aaa accounting dot1x default start-stop group radius through instance > dot1x port-controlCisco > Catalyst 4500 Series Switch Cisco IOS Command Reference, 12.2(52)SG > aaa accounting dot1x default start-stop group radius through instance > dot1x port-control The command dot1x port-control force-authorized is used to disable 802.1x on a port and permit traffic without authentication. Dot1x ports are in one of two states, authorized or unauthorized. Authorized ports permit user traffic to flow through the port. This state usually follows successful authentication. Unauthorized ports only permit authorization traffic to flow through the port. Usually a port begins in the unauthorized state. A user is then allowed to exchange AAA authentication traffic with the port. Once the user has been authenticated successfully, the port is changed to the authorized state and the user is permitted to use the port normally.
Normal use of 802.1x has the port configured with the dot1x port-control auto statement. This places the port in the unauthorized state until successful authentication. After successful authentication, the port is changed to the authorized state.
When 802.1x is initially configured, the default port control of the ports is force-authorized. This forces the port to be in the authorized state without successful authentication. This setting disables the need for authentication and permits all traffic.
The force-unauthorized keyword configures the port as an unauthorized port regardless of authentication traffic. A port configured with this key word would not permit user traffic, not even authentication traffic.
The command dot1x port-control disable is not a valid command due to incorrect syntax.
Objective:
Infrastructure Security Sub-Objective:
Describe device security using Cisco IOS AAA with TACACS+ and RADIUS
References:
Cisco > Catalyst 6500 Series Release 15.0SY Software Configuration Guide > Security > IEEE 802.1X Port-Based Authentication
Cisco > Catalyst 4500 Series Switch Cisco IOS Command Reference, 12.2(52)SG > aaa accounting dot1x default start-stop group radius through instance > dot1x port-control
Cisco > Catalyst 4500 Series Switch Cisco IOS Command Reference, 12.2(52)SG > aaa accounting dot1x default start-stop group radius through instance > dot1x port-control
Question 4
What command would be used to display detailed information regarding VRRP groups on the switch?
- switch# show vrrp
- switch# show standby
- switch# show vrrp detail
- switch# show standby detail
Correct answer: A
Explanation:
The command that would display detailed information regarding VRRP groups on the switch is show vrrp. The information provided for each VRRP group by this command includes the status, virtual IP and MAC addresses, whether preemption is enabled, priority of the switch, and the address of the group master.The command show vrrp detail does not exist on a Cisco device. The detail view is provided by the command show vrrp.The command show standby can be used to display detailed information about HSRP groups to which a switch belongs. This command is for HSRP only.The command show standby detail provides the same output as show standby. It can be used to display detailed information about HSRP groups a switch is a member of. This command is for HSRP only.Objective:Infrastructure Services Sub-Objective:Configure and verify first-hop redundancy protocols References:Cisco > Cisco IOS IP Application Services Command Reference > show vrrp The command that would display detailed information regarding VRRP groups on the switch is show vrrp. The information provided for each VRRP group by this command includes the status, virtual IP and MAC addresses, whether preemption is enabled, priority of the switch, and the address of the group master.
The command show vrrp detail does not exist on a Cisco device. The detail view is provided by the command show vrrp.
The command show standby can be used to display detailed information about HSRP groups to which a switch belongs. This command is for HSRP only.
The command show standby detail provides the same output as show standby. It can be used to display detailed information about HSRP groups a switch is a member of. This command is for HSRP only.
Objective:
Infrastructure Services Sub-Objective:
Configure and verify first-hop redundancy protocols
References:
Cisco > Cisco IOS IP Application Services Command Reference > show vrrp
Question 5
Assuming that preempt is not configured, when does a router in an HSRP group assume the role of the active router for the group?
- A router in standby status will become the active router if it has a higher priority than the active router.
- A router in standby status will become the active router when it does not detect three consecutive hello messages from the active router.
- A router in standby status will become the active router when it does not detect any hello messages from the active router within the configured holdtime.
- A router in listening status will become the active router when it does not detect any hello messages from the active router within the configured holdtime.
Correct answer: C
Explanation:
A router in standby status will become the active router when it does not detect any hello messages from the active router within the configured holdtime.There are two ways for a router to become the HSRP active router. On startup, the router with the highest priority or IP address will become the active router. If the active router fails, the HSRP standby router is a candidate to become the next active HSRP router. Failure of the active router is detected by the loss of hello messages for a configurable amount of time referred to as holdtime. By default, hellos are sent every three seconds (hello time) and the holdtime is 10 seconds.A router with the highest priority will be selected as the active router during the startup election process. If the active router fails and the standby router is promoted to be the active router, the first router will not immediately resume being the active router even if it has higher priority. This characteristic can be overridden with the configuration option of preempt. The router with the highest priority can initiate a coup to become the active router in the group if it has preempt enabled in the configuration. By default, all routers have an HSRP priority of 100. The range of values that can be assigned is 1 - 255.Other default values are: Standby holdtime is 10 secondsStandby track interface priority is 10To illustrate these concepts, consider the following example. Router A is configured with a priority of 150 and Router B is configured with a priority of 100. Neither router is configured to preempt. If both routers were shut down and Router 5 was rebooted first, then Router B would become the active router. If Router A was then rebooted, it would not become the active router even though it has a higher priority than Router B, because it was NOT configured with the preempt command to allow it to assume the active role with a higher priority.The six HSRP states are defined as follows:Initial state: All routers start in this state.Learn state: The router is in the learn state when it has not communicated with the active router. It does not know which router is the active router and does not know the IP address of the virtual router (if no HSRP IP address configured in the router). Listen state: Once the router hears from the active router and knows the virtual IP address, it enters the listen state. It is not the active or standby router. Speak state: After a router learns the IP address of the virtual router, it enters the speak state. It participates in the active and standby router election. It sends hello messages to the active router.Standby state: When the active router has been elected, the second router enters the standby state. This is the standby router and it will become the active router if the active router fails.Active state: The router is in active state when it is forwarding packets. It receives packets via the virtual IP address.Objective:Infrastructure Services Sub-Objective:Configure and verify first-hop redundancy protocolsReferences:Internetworking Case Studies > Using HSRP for Fault-Tolerant IP RoutingCisco > Cisco IOS IP Application Services Configuration Guide, Release 12.4 > Part 1: First Hop Redundancy Protocols > Configuring HSRP A router in standby status will become the active router when it does not detect any hello messages from the active router within the configured holdtime.
There are two ways for a router to become the HSRP active router. On startup, the router with the highest priority or IP address will become the active router. If the active router fails, the HSRP standby router is a candidate to become the next active HSRP router. Failure of the active router is detected by the loss of hello messages for a configurable amount of time referred to as holdtime. By default, hellos are sent every three seconds (hello time) and the holdtime is 10 seconds.
A router with the highest priority will be selected as the active router during the startup election process. If the active router fails and the standby router is promoted to be the active router, the first router will not immediately resume being the active router even if it has higher priority. This characteristic can be overridden with the configuration option of preempt. The router with the highest priority can initiate a coup to become the active router in the group if it has preempt enabled in the configuration. By default, all routers have an HSRP priority of 100. The range of values that can be assigned is 1 - 255.Other default values are:
- Standby holdtime is 10 seconds
- Standby track interface priority is 10
To illustrate these concepts, consider the following example. Router A is configured with a priority of 150 and Router B is configured with a priority of 100. Neither router is configured to preempt. If both routers were shut down and Router 5 was rebooted first, then Router B would become the active router. If Router A was then rebooted, it would not become the active router even though it has a higher priority than Router B, because it was NOT configured with the preempt command to allow it to assume the active role with a higher priority.
The six HSRP states are defined as follows:
- Initial state: All routers start in this state.
- Learn state: The router is in the learn state when it has not communicated with the active router. It does not know which router is the active router and does not know the IP address of the virtual router (if no HSRP IP address configured in the router).
- Listen state: Once the router hears from the active router and knows the virtual IP address, it enters the listen state. It is not the active or standby router. Speak state: After a router learns the IP address of the virtual router, it enters the speak state. It participates in the active and standby router election. It sends hello messages to the active router.
- Standby state: When the active router has been elected, the second router enters the standby state. This is the standby router and it will become the active router if the active router fails.
- Active state: The router is in active state when it is forwarding packets. It receives packets via the virtual IP address.
Objective:
Infrastructure Services Sub-Objective:
Configure and verify first-hop redundancy protocols
References:
Internetworking Case Studies > Using HSRP for Fault-Tolerant IP Routing
Cisco > Cisco IOS IP Application Services Configuration Guide, Release 12.4 > Part 1: First Hop Redundancy Protocols > Configuring HSRP
Question 6
You have configured three routers in HSRP group 10 to provide gateway redundancy for VLAN 56. Your intention was for Router 1 to be the active router in the group and for Router 3 to be the standby router. Furthermore, in the event that Router 1 became unavailable, resulting in Router 3 becoming active, you intended for Router 1 to resume its role as active when it came back online. However, you discover that in practice, Router 1 does NOT resume the active role when it comes back online.
What command should be executed on Router 1?
- router1(config)# interface VLAN 56router1(config-if)# standby 10 preempt
- router1(config)# interface VLAN 10router1(config-if)# standby 56 preempt
- router1(config)# standby 10 preempt
- router1(config)# standby 56 preempt
Correct answer: A
Explanation:
For Router 1 to resume its role as active when it comes back online, it must be configured to preempt the router with a lower priority. In this scenario, Router 3 must have been configured with a lower priority than Router 1, or else it would have been the active router to begin with. To allow Router 1 to take back over as active, it must be configured with the following commands that will allow it to preempt the router with the lower priority: router1(config)# interface VLAN 56 router1(config-if)# standby 1 preemptThis condition can be illustrated by executing the debug standby command on Router 1 as shown in the partial output below. The IP address of Router 1 is 192.168.11.112. The IP address of Router 3 is 192.168.11.150. The virtual IP address of the HSRP group is 192.168.11.156. Router 1 sends a hello in line 1 of the output and receives its hello in line 2. Line 1 shows that Router 1 has a priority of 100. Line 2 shows that Router 3(192.168.11.150) has a priority of 50. Although Router 1 has a higher priority, it is not configured to preempt, so it will not be able to take the active role back from Router 3. If Router 1 were configured to preempt, there would be a series of output as shown below:SB:56:Vl56 Hello in 192.168.11.112 Active pri 100 ip 192.168.11.156 SB:56:Vl56 Active router is 192.168.11.112, was localIf the HSRP router is the only HSRP router on the segment, then the output will show the router sending out hello packets with no hellos coming back.The commands below are incorrect because the VLAN is 56, not 10, and the group number is 10, not 56:router1(config)# interface VLAN 10 router1(config-if)# standby 56 preemptThe command below is incorrect because it is not executed under the VLAN 56 interface:router1(config)# standby 10 preemptThe command below is incorrect because it is not executed under the VLAN 56 interface and the HSRP number is incorrect: router1(config)# standby 56 preemptObjective: Infrastructure Services Sub-Objective:Configure and verify first-hop redundancy protocolsReferences:Internetworking Case Studies > Using HSRP for Fault-Tolerant IP RoutingCisco > Cisco IOS IP Application Services Command Reference > standby preempt through weight > standby preempt For Router 1 to resume its role as active when it comes back online, it must be configured to preempt the router with a lower priority. In this scenario, Router 3 must have been configured with a lower priority than Router 1, or else it would have been the active router to begin with. To allow Router 1 to take back over as active, it must be configured with the following commands that will allow it to preempt the router with the lower priority:
router1(config)# interface VLAN 56 router1(config-if)# standby 1 preempt
This condition can be illustrated by executing the debug standby command on Router 1 as shown in the partial output below. The IP address of Router 1 is 192.168.11.112. The IP address of Router 3 is 192.168.11.150. The virtual IP address of the HSRP group is 192.168.11.156.
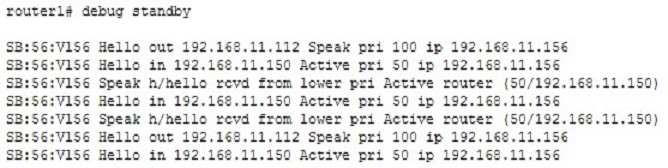
Router 1 sends a hello in line 1 of the output and receives its hello in line 2. Line 1 shows that Router 1 has a priority of 100. Line 2 shows that Router 3
(192.168.11.150) has a priority of 50. Although Router 1 has a higher priority, it is not configured to preempt, so it will not be able to take the active role back from Router 3. If Router 1 were configured to preempt, there would be a series of output as shown below:
SB:56:Vl56 Hello in 192.168.11.112 Active pri 100 ip 192.168.11.156 SB:56:Vl56 Active router is 192.168.11.112, was local
If the HSRP router is the only HSRP router on the segment, then the output will show the router sending out hello packets with no hellos coming back.
The commands below are incorrect because the VLAN is 56, not 10, and the group number is 10, not 56:
router1(config)# interface VLAN 10 router1(config-if)# standby 56 preempt
The command below is incorrect because it is not executed under the VLAN 56 interface:
router1(config)# standby 10 preempt
The command below is incorrect because it is not executed under the VLAN 56 interface and the HSRP number is incorrect: router1(config)# standby 56 preempt
Objective:
Infrastructure Services Sub-Objective:
Configure and verify first-hop redundancy protocols
References:
Internetworking Case Studies > Using HSRP for Fault-Tolerant IP Routing
Cisco > Cisco IOS IP Application Services Command Reference > standby preempt through weight > standby preempt
Question 7
The partial output displayed in the exhibit is a result of what IOS command? (Click on the Exhibit(s) button.)
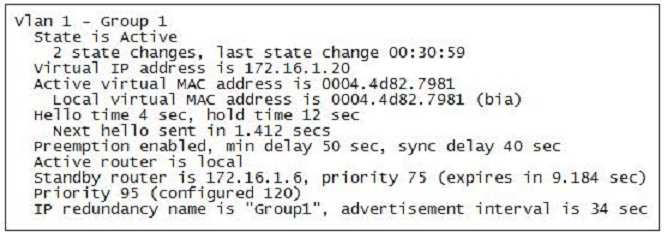
- switch# show running-config
- switch# show standby vlan1 active brief
- switch# show hsrp 1
- switch# show standby
Correct answer: D
Question 8
You have been assigned to create a plan to implement HSRP on the router connecting your company's network to the Internet. The router should be the active router in the HSRP group. On the active router, the following conditions should be met:
- Enable preemption with no delay
- Set Hello timer to 10 seconds and hold time to 25 seconds
- Set the priority to 150
Which of the following commands should be included in the plan to meet the given requirements? (Choose all that apply.)
- standby 1 preempt delay minimum 10
- standby 1 preempt
- standby 1 priority 150
- standby 1 timers 10 25
- standby 1 timers 25 10
- standby track interface S0/1
Correct answer: BCD
Explanation:
The following commands should be included in the implementation plan to meet the given requirements:standby 1 preempt standby 1 priority 150 standby 1 timers 10 25The standby 1 preempt command configures the preempt settings on the router. This command allows preemption without any delay. The standby 1 priority 150 command sets the priority of the router to 150. The default priority of HSRP routers is 100. This implies that this router becomes the active router if there are no other routers in the group with a higher priority. The standby 1 timers 10 25 command sets the Hello timer and the hold time on the local router. The first value, 10, specifies the Hello timer, and the second value, 25, indicates the hold time.The most essential steps to configure HSRP on routers are as follows:Assign IP addresses to the interfaces using the ip address commandEnable HSRP on the interfaces and assign the virtual IP address using the standby ip commandSet the HSRP priority of the interfaces using the standby priority commandConfigure HSRP preempt settings on the interfaces using the standby preempt commandSet the Hello timers using the standby timers commandEnable interface tracking for other HSRP-enabled interfaces using the standby track commandThe standby 1 preempt delay minimum 10 command should not be included in the implementation plan. This command causes the router to preempt the active router after a minimum of 10 seconds. However, the requirement states that there should be no delay in preemption (a delay of 0 seconds), which is the default behavior.The standby 1 timers 25 10 command should not be included in the implementation plan. This command sets the Hello timer to 25 seconds and the hold time to 10 seconds. However, the requirement is to set the Hello timer to 10 seconds and the hold time to 25 seconds.The standby track interface S0/1 command should not be included in the implementation plan. This command enables tracking of the S0/1 interface on the local router. However, there is no requirement in the scenario to track an interface. Tracking can be used to decrement the priority of an HSRP router when the interface goes down. Using the default decrement value, if S0/1 were to go down, the priority of the router would be reduced by 10.Objective:Infrastructure Services Sub-Objective:Configure and verify first-hop redundancy protocolsReferences: Home > Support > Configuring HSRP > How to Configure HSRPInternetworking Case Studies > Using HSRP for Fault-Tolerant IP Routing > Configuring HSRP The following commands should be included in the implementation plan to meet the given requirements:
standby 1 preempt standby 1 priority 150 standby 1 timers 10 25
The standby 1 preempt command configures the preempt settings on the router. This command allows preemption without any delay. The standby 1 priority 150 command sets the priority of the router to 150. The default priority of HSRP routers is 100. This implies that this router becomes the active router if there are no other routers in the group with a higher priority. The standby 1 timers 10 25 command sets the Hello timer and the hold time on the local router. The first value, 10, specifies the Hello timer, and the second value, 25, indicates the hold time.
The most essential steps to configure HSRP on routers are as follows:
- Assign IP addresses to the interfaces using the ip address command
- Enable HSRP on the interfaces and assign the virtual IP address using the standby ip command
- Set the HSRP priority of the interfaces using the standby priority command
- Configure HSRP preempt settings on the interfaces using the standby preempt command
- Set the Hello timers using the standby timers command
- Enable interface tracking for other HSRP-enabled interfaces using the standby track command
The standby 1 preempt delay minimum 10 command should not be included in the implementation plan. This command causes the router to preempt the active router after a minimum of 10 seconds. However, the requirement states that there should be no delay in preemption (a delay of 0 seconds), which is the default behavior.
The standby 1 timers 25 10 command should not be included in the implementation plan. This command sets the Hello timer to 25 seconds and the hold time to 10 seconds. However, the requirement is to set the Hello timer to 10 seconds and the hold time to 25 seconds.
The standby track interface S0/1 command should not be included in the implementation plan. This command enables tracking of the S0/1 interface on the local router. However, there is no requirement in the scenario to track an interface. Tracking can be used to decrement the priority of an HSRP router when the interface goes down. Using the default decrement value, if S0/1 were to go down, the priority of the router would be reduced by 10.
Objective:
Infrastructure Services Sub-Objective:
Configure and verify first-hop redundancy protocols
References:
Home > Support > Configuring HSRP > How to Configure HSRP
Internetworking Case Studies > Using HSRP for Fault-Tolerant IP Routing > Configuring HSRP
Question 9
Which statement best describes the function of Hot Standby Router Protocol (HSRP)?
- HSRP specifies a single IP address that all routers in the group must use.
- HSRP defines a set of routers that represent one virtual, fault-tolerant router.
- HSRP provides a round-robin gateway selection process to increase fault tolerance.
- HSRP defines a frame-tagging scheme that allows end stations to use any router as a gateway.
Correct answer: B
Explanation:
Hot Standby Router Protocol (HSRP) is specified by RFC 2281. The primary function of HSRP is to define a set of routers that work together to represent one virtual, fault-tolerant router. Thus, redundancy is provided in the event that any one of the routers fails. HSRP can be configured on the following interface types: Routed ports Switched virtual interfaces (SVI) Etherchannel port channels HSRP does use a single IP address to represent a group of routers, but this does not fully describe the function of HSRP. HSRP does not provide round-robin gateway selection. HSRP uses router priority to select a primary and standby router. HSRP does not define a frame-tagging scheme that allows end stations to use any router as a gateway. End stations use the virtual IP address of a group of HSRP routers as the default gateway. Objective: Infrastructure Services Sub-Objective: Configure and verify first-hop redundancy protocols References: Internetworking Case Studies > Using HSRP for Fault-Tolerant IP Routing Cisco > Cisco IOS IP Application Services Configuration Guide, Release 12.4 > Part 1: First Hop Redundancy Protocols > Configuring HSRP Hot Standby Router Protocol (HSRP) is specified by RFC 2281. The primary function of HSRP is to define a set of routers that work together to represent one virtual, fault-tolerant router. Thus, redundancy is provided in the event that any one of the routers fails. HSRP can be configured on the following interface types:
- Routed ports
- Switched virtual interfaces (SVI)
- Etherchannel port channels
HSRP does use a single IP address to represent a group of routers, but this does not fully describe the function of HSRP.
HSRP does not provide round-robin gateway selection. HSRP uses router priority to select a primary and standby router.
HSRP does not define a frame-tagging scheme that allows end stations to use any router as a gateway. End stations use the virtual IP address of a group of HSRP routers as the default gateway.
Objective:
Infrastructure Services Sub-Objective:
Configure and verify first-hop redundancy protocols
References:
Internetworking Case Studies > Using HSRP for Fault-Tolerant IP Routing
Cisco > Cisco IOS IP Application Services Configuration Guide, Release 12.4 > Part 1: First Hop Redundancy Protocols > Configuring HSRP
Question 10
Which of the following statements best describes the result of issuing the command standby 44 timers 3 1 on an HSRP router?
- The holdtime will be set to a value of 3, and the hellotime will be set to a value of 1.
- The status of the standby router will be displayed as unknown expired.
- The role of active router will be passed repeatedly from one router to another.
- The router will be configured to reassume the role of active router in the event that the router fails and is subsequently restarted.
Correct answer: C
Explanation:
When the command standby 44 timers 3 1 is issued on a Hot Standby Routing Protocol (HSRP) router, the role of active router will be passed repeatedly from one router to another. This behavior occurs when the timers are set incorrectly. The syntax for the standby timers command is standby [group-number] timers [hellotime holdtime].The hellotime variable is the number of seconds between hello messages and is set to a value of 3 by default.The holdtime variable is the number of seconds that the HSRP standby router will wait before assuming that the active router is down; if the standby router believes the active router to be down, it will assume the role of active router.The holdtime is set to a value of 10 by default. The holdtime should be set to a value at least three times the value of the hellotime. Otherwise, the active router might not be able to respond before the standby router assumes that the active router is down and becomes the new active router.Because the command standby 44 timers 3 1 sets the hellotime to a value of 3 and the holdtime to a value of 1, the role of active router will be passed from one standby router to the next. To set the holdtime to a value of 3 and the hellotime to a value of 1, the command standby 44 timers 1 3 should be issued. To reset the timer values to their default values, the command no standby group-number timers should be issued.The status of the standby router will be displayed as unknown expired if a Physical layer problem exists. The unknown expired status can also be displayed if only one HSRP router is configured for the subnet.To configure an HSRP router to reassume the role of active router in the event that the router fails and is subsequently restarted, the command standby groupnumber preempt should be issued. When the HSRP active router fails or is shut down, the standby router assumes the role of active router. By default, when the original HSRP active router is restarted, it does not take the role of active router away from the original standby router, even if the original active router has a higher priority value. The command standby group-number preempt changes this default behavior.The holdtime will not be set to a value of 3, and the hellotime will not be set to a value of 1. On the contrary, the hellotime will be set to a value of 3 and the holdtime will be set to a value of 1. Objective:Infrastructure Services Sub-Objective:Configure and verify first-hop redundancy protocolsReferences:Cisco IOS IP Application Services Command Reference > show vrrp through synguard (virtual server) > standby timersCisco > Cisco IOS IP Application Services Configuration Guide, Release 12.4 > Part 1: First Hop Redundancy Protocols > Configuring HSRP When the command standby 44 timers 3 1 is issued on a Hot Standby Routing Protocol (HSRP) router, the role of active router will be passed repeatedly from one router to another. This behavior occurs when the timers are set incorrectly. The syntax for the standby timers command is standby [group-number] timers [hellotime holdtime].
The hellotime variable is the number of seconds between hello messages and is set to a value of 3 by default.
The holdtime variable is the number of seconds that the HSRP standby router will wait before assuming that the active router is down; if the standby router believes the active router to be down, it will assume the role of active router.
The holdtime is set to a value of 10 by default. The holdtime should be set to a value at least three times the value of the hellotime. Otherwise, the active router might not be able to respond before the standby router assumes that the active router is down and becomes the new active router.
Because the command standby 44 timers 3 1 sets the hellotime to a value of 3 and the holdtime to a value of 1, the role of active router will be passed from one standby router to the next. To set the holdtime to a value of 3 and the hellotime to a value of 1, the command standby 44 timers 1 3 should be issued. To reset the timer values to their default values, the command no standby group-number timers should be issued.
The status of the standby router will be displayed as unknown expired if a Physical layer problem exists. The unknown expired status can also be displayed if only one HSRP router is configured for the subnet.
To configure an HSRP router to reassume the role of active router in the event that the router fails and is subsequently restarted, the command standby groupnumber preempt should be issued. When the HSRP active router fails or is shut down, the standby router assumes the role of active router. By default, when the original HSRP active router is restarted, it does not take the role of active router away from the original standby router, even if the original active router has a higher priority value. The command standby group-number preempt changes this default behavior.
The holdtime will not be set to a value of 3, and the hellotime will not be set to a value of 1. On the contrary, the hellotime will be set to a value of 3 and the holdtime will be set to a value of 1.
Objective:
Infrastructure Services Sub-Objective:
Configure and verify first-hop redundancy protocols
References:
Cisco IOS IP Application Services Command Reference > show vrrp through synguard (virtual server) > standby timers
Cisco > Cisco IOS IP Application Services Configuration Guide, Release 12.4 > Part 1: First Hop Redundancy Protocols > Configuring HSRP
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



