Download Implementing Cisco Network Security.210-260.ExamCollection.2024-10-15.137q.vcex
| Vendor: | Cisco |
| Exam Code: | 210-260 |
| Exam Name: | Implementing Cisco Network Security |
| Date: | Oct 15, 2024 |
| File Size: | 7 MB |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
You are using ASDM to verify a clientless SSL VPN configuration made by a junior administrator on an ASA.
Please click exhibit to answer the following questions.
Which of the following tunneling protocols will the jane user account be able to use when establishing a clientless SSL VPN connection by using the boson tunnel group? (Select the best answer.)
Exhibit:
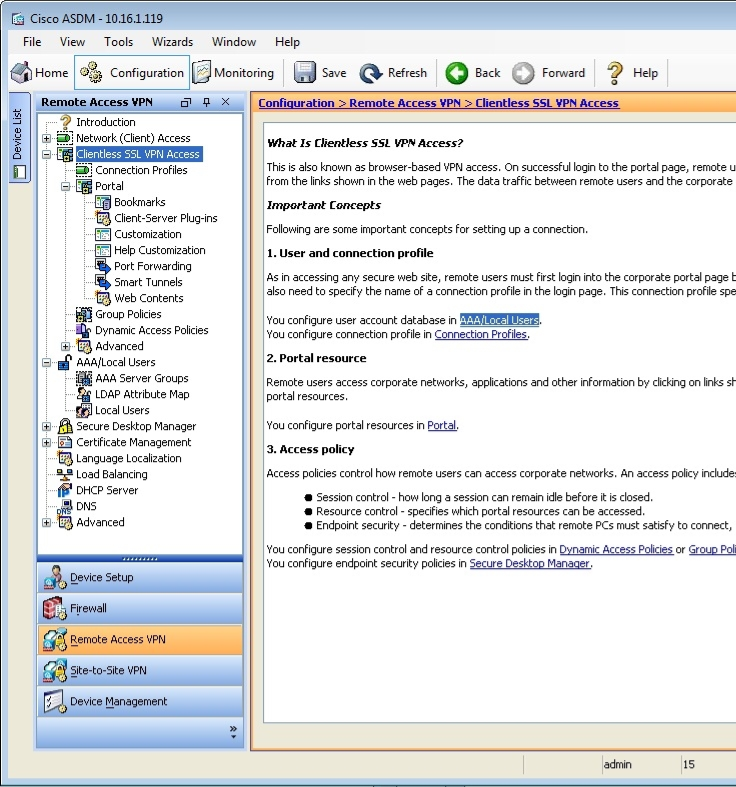
- only clientless SSL VPN
- only SSL VPN client
- only IPSec
- only L2TP/IPSec
- both client and clientless SSL VPN
- both clientless SSL VPN and IPSec
Correct answer: A
Explanation:
The jane user account will be able to use only the clientless Secure Sockets Layer (SSL) virtual private network (VPN) tunneling protocol when establishing a clientless SSL VPN connection by using the boson tunnel group. You can specify the tunneling protocols that can be used to establish a connection to a tunnel group, which is also known as a connection profile, either in a group policy or within a user account, depending on whether the tunneling protocol configuration should be applied to a group or to a single user.When you configure a tunneling protocol, you can specify one or more of the following four options: Clientless SSL VPN, SSL VPN Client, IPSec, or L2TP/IPSec.In this scenario, you can view the tunneling protocols that are configured for the jane user account by accessing her user account information in Cisco Adaptive Security Device Manager (ASDM) by clicking Configuration, clicking the Remote Access VPN button, expanding AAA/Local Users, clicking Local Users, and doubleclicking the jane user account, which will open the Edit User Account dialog box. You should then click VPN Policy, which will display a pane that includes a Tunneling Protocols entry. This entry for the jane user account is configured with the Inherit option, which means that the tunneling protocols that the jane user account can use will be inherited from a group policy that is associated with the jane user account. In this scenario, the jane user account is associated with the boson_grp group policy.To view the tunneling protocols that are associated with the boson_grp group policy in ASDM, you should click Configuration, click the Remote Access VPN button, expand Clientless SSL VPN Access, select Group Policies, and doubleclick boson_grp, which will open the Edit Internal Group Policy dialog box. The More Options section on the General pane displays the Tunneling Protocols entry. Only the Clientless SSL VPNoption is selected, as shown in the following exhibit: Reference:Cisco: General VPN Setup: Adding or Editing a Remote Access Internal Group Policy, General Attributes The jane user account will be able to use only the clientless Secure Sockets Layer (SSL) virtual private network (VPN) tunneling protocol when establishing a clientless SSL VPN connection by using the boson tunnel group. You can specify the tunneling protocols that can be used to establish a connection to a tunnel group, which is also known as a connection profile, either in a group policy or within a user account, depending on whether the tunneling protocol configuration should be applied to a group or to a single user.
When you configure a tunneling protocol, you can specify one or more of the following four options: Clientless SSL VPN, SSL VPN Client, IPSec, or L2TP/IPSec.
In this scenario, you can view the tunneling protocols that are configured for the jane user account by accessing her user account information in Cisco Adaptive Security Device Manager (ASDM) by clicking Configuration, clicking the Remote Access VPN button, expanding AAA/Local Users, clicking Local Users, and doubleclicking the jane user account, which will open the Edit User Account dialog box. You should then click VPN Policy, which will display a pane that includes a Tunneling Protocols entry. This entry for the jane user account is configured with the Inherit option, which means that the tunneling protocols that the jane user account can use will be inherited from a group policy that is associated with the jane user account. In this scenario, the jane user account is associated with the boson_grp group policy.
To view the tunneling protocols that are associated with the boson_grp group policy in ASDM, you should click Configuration, click the Remote Access VPN button, expand Clientless SSL VPN Access, select Group Policies, and doubleclick boson_grp, which will open the Edit Internal Group Policy dialog box. The More Options section on the General pane displays the Tunneling Protocols entry. Only the Clientless SSL VPNoption is selected, as shown in the following exhibit:
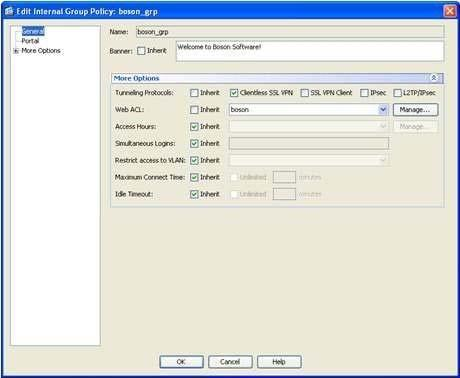
Reference:
Cisco: General VPN Setup: Adding or Editing a Remote Access Internal Group Policy, General Attributes
Question 2
You are using ASDM to verify a clientless SSL VPN configuration made by a junior administrator on an ASA.
Please click exhibit to answer the following questions.
Exhibit:

Which of the following connection profiles will use the boson_grp group policy? (Select the best answer.)
- only the boson connection profile
- only the DefaultRAGroup connection profile
- only the DefaultWEBVPNGroup connection profile
- both the boson connection profile and the DefaultWEBVPNGroup connection profile
- both the DefaultRAGroup connection profile and the DefaultWEBVPNGroup
Correct answer: A
Explanation:
Only the boson connection profile will use the boson_grp group policy. To determine which connection profiles will use the boson_grp group policy, you should access the Connection Profiles pane in Cisco Adaptive Security Device Manager (ASDM). To access this pane, you should click Configuration, click the Remote Access VPN button, expand Clientless SSL VPN Access, and click Connection Profiles, which will open the Connection Profiles configuration pane, as shown in the following exhibit: This pane displays a summary of the connection profiles that are configured on the Cisco Adaptive Security Appliance (ASA). In this scenario, there are three connection profiles. There are two default profiles, DefaultRAGroup and DefaultWEBVPNGroup, and one userspecified connection profile, boson. To view which group policy is associated with which connection profile, you should doubleclick the connection profiles to open the Edit Clientless SSL VPN Connection Profile dialog box. The default group policy that is associated with a connection profile is displayed on the Basic pane of this dialog box. By viewing this information, you can determine that only the boson connection profile uses the boson_grp group policy. The Basic pane of the boson connection profile is shown in the following exhibit: The two default connection profiles use the default group policy, which is DfltGrpPolicy.Reference:Cisco: Configuring Tunnel Groups, Group Policies, and Users: Connection Profiles Only the boson connection profile will use the boson_grp group policy. To determine which connection profiles will use the boson_grp group policy, you should access the Connection Profiles pane in Cisco Adaptive Security Device Manager (ASDM). To access this pane, you should click Configuration, click the Remote Access VPN button, expand Clientless SSL VPN Access, and click Connection Profiles, which will open the Connection Profiles configuration pane, as shown in the following exhibit:
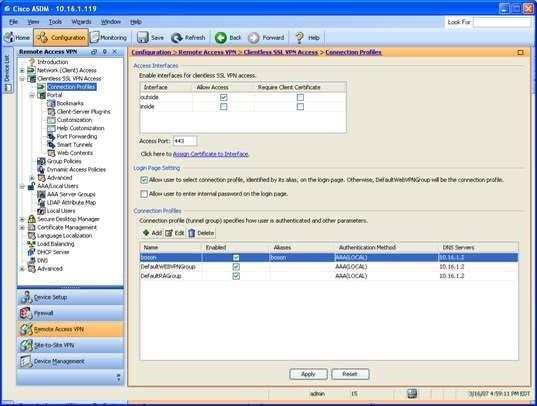
This pane displays a summary of the connection profiles that are configured on the Cisco Adaptive Security Appliance (ASA). In this scenario, there are three connection profiles. There are two default profiles, DefaultRAGroup and DefaultWEBVPNGroup, and one userspecified connection profile, boson. To view which group policy is associated with which connection profile, you should doubleclick the connection profiles to open the Edit Clientless SSL VPN Connection Profile dialog box. The default group policy that is associated with a connection profile is displayed on the Basic pane of this dialog box. By viewing this information, you can determine that only the boson connection profile uses the boson_grp group policy. The Basic pane of the boson connection profile is shown in the following exhibit:
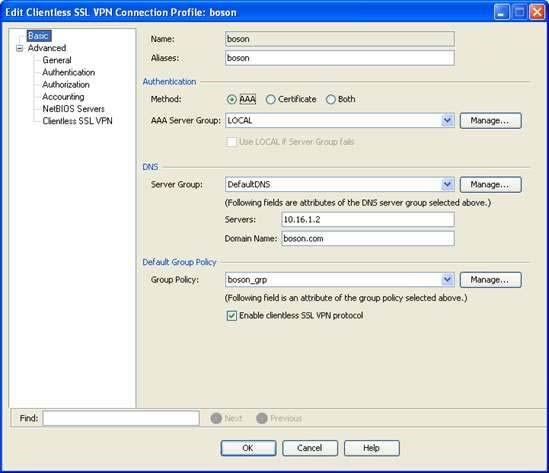
The two default connection profiles use the default group policy, which is DfltGrpPolicy.
Reference:
Cisco: Configuring Tunnel Groups, Group Policies, and Users: Connection Profiles
Question 3
Which of the following is typically used to manage a Cisco router in-band? (Select the best answer.)
- a VTY port
- a serial port
- a console port
- an auxiliary port
Correct answer: A
Explanation:
A virtual terminal (VTY) port is typically used to manage a Cisco router in-band. When a Cisco device is operating in its normal state, another device can connect to it by using VTY application protocols such as Telnet or Secure Shell (SSH). The use of VTY lines typically allows multiple administrators or management applications to concurrently access a device from more than one location.You would not use a console port or an auxiliary (AUX) port to manage a Cisco router in-band. You are most likely to use either an AUX port or a console port to manage a Cisco router out-of-band, such as when the router is in read-only memory (ROM) monitor (ROMmon) mode. The AUX port on a Cisco router is typically capable of supporting most of the features available on a console port. Cisco switches either do not have AUX ports or do not support certain features, such as system recovery, on their AUX ports if they have them. ROMmon is a management mode that Cisco routers and switches revert to when the system cannot find a software image, the software image is corrupted, or the configuration register has been set to manually enter ROMmon mode. Because ROMmon is an out-of-band management method, it can be used to recover system software images, passwords, or other configuration data even when the router or switch is in a state where it can no longer forward packets. You would not use a serial port to manage a Cisco router in-band. Serial ports and Ethernet ports are used to directly connect Cisco routers to other network devices. For example, you might use a serial port to directly connect a Cisco router to other data terminal equipment (DTE) or data circuit-terminating equipment (DCE) devices. You would also use a serial port to connect a router to a Channel Service Unit/Data Service Unit (CSU/DSU).Reference:Cisco: Cisco Guide to Harden Cisco IOS Devices: Management Interface Use A virtual terminal (VTY) port is typically used to manage a Cisco router in-band. When a Cisco device is operating in its normal state, another device can connect to it by using VTY application protocols such as Telnet or Secure Shell (SSH). The use of VTY lines typically allows multiple administrators or management applications to concurrently access a device from more than one location.
You would not use a console port or an auxiliary (AUX) port to manage a Cisco router in-band. You are most likely to use either an AUX port or a console port to manage a Cisco router out-of-band, such as when the router is in read-only memory (ROM) monitor (ROMmon) mode. The AUX port on a Cisco router is typically capable of supporting most of the features available on a console port. Cisco switches either do not have AUX ports or do not support certain features, such as system recovery, on their AUX ports if they have them.
ROMmon is a management mode that Cisco routers and switches revert to when the system cannot find a software image, the software image is corrupted, or the configuration register has been set to manually enter ROMmon mode. Because ROMmon is an out-of-band management method, it can be used to recover system software images, passwords, or other configuration data even when the router or switch is in a state where it can no longer forward packets.
You would not use a serial port to manage a Cisco router in-band. Serial ports and Ethernet ports are used to directly connect Cisco routers to other network devices. For example, you might use a serial port to directly connect a Cisco router to other data terminal equipment (DTE) or data circuit-terminating equipment (DCE) devices. You would also use a serial port to connect a router to a Channel Service Unit/Data Service Unit (CSU/DSU).
Reference:
Cisco: Cisco Guide to Harden Cisco IOS Devices: Management Interface Use
Question 4
Which of the following enables the validation of both user and device credentials in a single EAP transaction?
(Select the best answer.)
- PEAP
- EAP-FAST
- EAP-FAST with EAP chaining
- EAP-MD5
Correct answer: C
Explanation:
Extensible Authentication Protocol (EAP)Flexible Authentication via Secure Tunneling (FAST) with EAP chaining, which is also sometimes called EAPFAST version 2 (EAPFASTv2), enables the validation of both user and device credentials in a single EAP transaction. EAP chaining enables a Cisco security device to validate authentication credentials for both a user and the user’s device. In order to enable EAP chaining, both the Cisco security device and the supplicant device must support EAP chaining. The Cisco security device will assign a different level of authorization access depending on one of four success and failure possibilities, as shown in the following table: EAPFAST is an authentication protocol that can be used for point-to-point connections and for both wired and wireless links. The EAPFAST authentication process consists of three phases. The first phase, which is optional and is considered phase 0, consists of provisioning a client with a PAC, which is a digital credential that is used for authentication. A PAC can be manually configured on a client, in which case phase 0 is not required. The second phase, which is referred to as phase 1, involves creating a secure tunnel between the client and the server. The final phase, which is referred to as phase 2, involves authenticating the client. If the client is authenticated, the client will be able to access the network.EAPTransport Layer Security (TLS) is an Internet Engineering Task Force (IETF) standard that is defined in Request for Comments (RFC) 5216. It does not support EAP chaining. Protected EAP (PEAP) is an open standard developed by Cisco, Microsoft, and RSA? it does not support EAP chaining. EAPMessage Digest 5 (MD5) uses an MD5 hash function to provide security and is therefore considered weak when compared to later methods. EAP is an IETF standard that was originally defined in RFC 2284? it does not support EAP chaining.Reference:Cisco: Cisco Identity Services Engine Administrator Guide, Release 1.3: Allowed Protocols Extensible Authentication Protocol (EAP)Flexible Authentication via Secure Tunneling (FAST) with EAP chaining, which is also sometimes called EAPFAST version 2 (EAPFASTv2), enables the validation of both user and device credentials in a single EAP transaction. EAP chaining enables a Cisco security device to validate authentication credentials for both a user and the user’s device. In order to enable EAP chaining, both the Cisco security device and the supplicant device must support EAP chaining. The Cisco security device will assign a different level of authorization access depending on one of four success and failure possibilities, as shown in the following table:
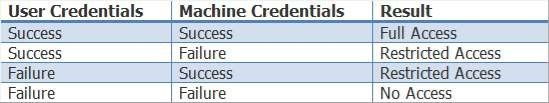
EAPFAST is an authentication protocol that can be used for point-to-point connections and for both wired and wireless links. The EAPFAST authentication process consists of three phases. The first phase, which is optional and is considered phase 0, consists of provisioning a client with a PAC, which is a digital credential that is used for authentication. A PAC can be manually configured on a client, in which case phase 0 is not required. The second phase, which is referred to as phase 1, involves creating a secure tunnel between the client and the server. The final phase, which is referred to as phase 2, involves authenticating the client. If the client is authenticated, the client will be able to access the network.
EAPTransport Layer Security (TLS) is an Internet Engineering Task Force (IETF) standard that is defined in Request for Comments (RFC) 5216. It does not support EAP chaining. Protected EAP (PEAP) is an open standard developed by Cisco, Microsoft, and RSA? it does not support EAP chaining.
EAPMessage Digest 5 (MD5) uses an MD5 hash function to provide security and is therefore considered weak when compared to later methods. EAP is an IETF standard that was originally defined in RFC 2284? it does not support EAP chaining.
Reference:
Cisco: Cisco Identity Services Engine Administrator Guide, Release 1.3: Allowed Protocols
Question 5
Which of the following features protects the control plane by classifying traffic into three separate control plane subinterfaces? (Select the best answer.)
- CoPP
- CPPr
- RBAC
- uRPF
Correct answer: B
Explanation:
Control Plane Protection (CPPr) protects the control plane by classifying control plane traffic into three separate subinterfaces: the host subinterface, the transit subinterface, and the Cisco Express Forwarding (CEF)exception subinterface. The host subinterface contains control plane IP traffic that is destined for a router interface, including traffic from the following sources and protocols:Terminating tunnelsSecure Shell (SSH)Simple Network Management Protocol (SNMP)Internal Border Gateway Protocol (iBGP)Enhanced Interior Gateway Routing Protocol (EIGRP)The transit subinterface contains control plane IP traffic that is traversing the router, including the following traffic:Nonterminating tunnel trafficTraffic that is softwareswitched by the route processorThe CEFexception subinterface contains control plane traffic that is redirected by CEF for process switching, as well as traffic from the following sources and protocols:NonIP hostsAddress Resolution Protocol (ARP) External BGP (eBGP)Open Shortest Path First (OSPF)Label Distribution Protocol (LDP)Layer 2 keepalivesCPPr is used to protect the control plane by filtering and rate limiting traffic in order to prevent excessive CPU and memory consumption. To configure CPPr, you must perform the following steps:Create access control lists (ACLs) to identify traffic.Create a traffic class.Create a traffic policy, and associate the traffic class to the policy- Apply the policy to the specific control plane subinterface.Control Plane Policing (CoPP) is similar to CPPr, except CoPP does not separate control plane traffic into three subinterfaces. To configure CoPP, you must perform the following steps:Create ACLs to identify traffic.Create a traffic class.Create a traffic policy, and associate the traffic class to the policy.Apply the policy to the control plane interface.Both CoPP and CPPr use class maps to filter and ratelimit traffic. However, CPPr separates control plane traffic into three subinterfaces: the host subinterface, the transit subinterface, and the Cisco Express Forwarding (CEF)exception subinterface. For this reason, Cisco recommends that you use CPPr instead of CoPP whenever possible.RoleBased Access Control (RBAC) does not protect the control plane. RBAC protects the management plane by granting limited access to administrators so that they can perform only the tasks required for their job. For example, you can configure permissions on an administrator's account so that the administrator can issue only certain commands, which will prevent the administrator from making unauthorized configuration changes or from viewing restricted information. Unicast Reverse Path Forwarding (uRPF) does not protect the control plane. uRPF protects the data plane by checking the source IP address of a packet to determine whether an inbound packet arrived on the best path back to the source based on routing table information. If the uRPF check passes, the packet is transmitted? if the uRPF check fails, the packet is dropped.Reference:Cisco: Control Plane Protection Control Plane Protection (CPPr) protects the control plane by classifying control plane traffic into three separate subinterfaces: the host subinterface, the transit subinterface, and the Cisco Express Forwarding (CEF)exception subinterface. The host subinterface contains control plane IP traffic that is destined for a router interface, including traffic from the following sources and protocols:
- Terminating tunnels
- Secure Shell (SSH)
- Simple Network Management Protocol (SNMP)
- Internal Border Gateway Protocol (iBGP)
- Enhanced Interior Gateway Routing Protocol (EIGRP)
The transit subinterface contains control plane IP traffic that is traversing the router, including the following traffic:
- Nonterminating tunnel traffic
- Traffic that is softwareswitched by the route processor
The CEFexception subinterface contains control plane traffic that is redirected by CEF for process switching, as well as traffic from the following sources and protocols:
- NonIP hosts
- Address Resolution Protocol (ARP)
- External BGP (eBGP)
- Open Shortest Path First (OSPF)
- Label Distribution Protocol (LDP)
- Layer 2 keepalives
CPPr is used to protect the control plane by filtering and rate limiting traffic in order to prevent excessive CPU and memory consumption. To configure CPPr, you must perform the following steps:
- Create access control lists (ACLs) to identify traffic.
- Create a traffic class.
- Create a traffic policy, and associate the traffic class to the policy
- Apply the policy to the specific control plane subinterface.
Control Plane Policing (CoPP) is similar to CPPr, except CoPP does not separate control plane traffic into three subinterfaces. To configure CoPP, you must perform the following steps:
- Create ACLs to identify traffic.
- Create a traffic class.
- Create a traffic policy, and associate the traffic class to the policy.
- Apply the policy to the control plane interface.
Both CoPP and CPPr use class maps to filter and ratelimit traffic. However, CPPr separates control plane traffic into three subinterfaces: the host subinterface, the transit subinterface, and the Cisco Express Forwarding (CEF)exception subinterface. For this reason, Cisco recommends that you use CPPr instead of CoPP whenever possible.
RoleBased Access Control (RBAC) does not protect the control plane. RBAC protects the management plane by granting limited access to administrators so that they can perform only the tasks required for their job. For example, you can configure permissions on an administrator's account so that the administrator can issue only certain commands, which will prevent the administrator from making unauthorized configuration changes or from viewing restricted information.
Unicast Reverse Path Forwarding (uRPF) does not protect the control plane. uRPF protects the data plane by checking the source IP address of a packet to determine whether an inbound packet arrived on the best path back to the source based on routing table information. If the uRPF check passes, the packet is transmitted? if the uRPF check fails, the packet is dropped.
Reference:
Cisco: Control Plane Protection
Question 6
Your company’s active ASA currently shares its stateful failover link with a regular data interface. Your supervisor asks you to configure a failover key on both the active ASA and the standby ASA.
Which of the following is most likely the reason? (Select the best answer.)
- so that the risk of exposure of VPN configuration information is mitigated
- so that both ASA devices forward traffic for a given group of security contexts
- so that the active ASA can monitor the status of the standby ASA
- so that the stateful failover link cannot use a regular data interface
Correct answer: A
Explanation:
Most likely, you would configure a failover key on both the active Cisco Adaptive Security Appliance (ASA) and the standby ASA so that the risk of exposure of virtual private network (VPN) configuration is mitigated. An ASA can share its stateful failover link with a regular data interface only when the unit is operating in single context, routed mode. However, Cisco strongly recommends using a dedicated Ethernet interface or sharing a LAN failover link instead because stateful failover traffic can increase the possibility of congestion and can negatively impact the performance of the shared data interface. In addition, all LAN failover and stateful failover information is transmitted as clear text by default. Therefore, sharing the stateful failover link with a regular data interface can unnecessarily expose VPN configuration information, such as user names, passwords, and preshared keys (PSKs) to malicious users on the shared network segment. You can mitigate this risk by configuring a failover key on both the active unit and the standby unit to protect failover information.You would not configure a failover key so that the active ASA can monitor the status of the standby ASA. An ASA can be configured to participate in either an active/standby or an active/active failover configuration. In an active/standby configuration, one ASA serves as the active unit and forwards traffic. A second ASA functions as a standby unit, which monitors the status of the active unit. If a failover event is triggered, the standby unit takes on the role of the active unit.You would not configure a failover key so that both ASA devices forward traffic for a given group of security contexts. An active/active failover configuration enables both ASAs to forward traffic for a select group of security contexts. With active/active failover, two failover groups exist as security contexts on each ASA. When a failover event is triggered, a failover group can become active on a standby unit or the entire standby unit can become the new active unit. Because an active/active failover configuration relies on security contexts, both ASAs must be in multiple context mode before active/active failover can be implemented. The failoverconfiguration for each unit in an active/active failover configuration is managed from within the system context.Unlike user contexts, the system context does not contain any normal data interfaces.You would not configure a failover key so that the stateful failover link cannot use a regular data interface.Instead, you would configure an ASA to operate in multiple context, routed mode or multiple context, transparent mode. An ASA operating in multiple context, routed mode or multiple context, transparent mode does not support using a regular data interface as the stateful failover link. When an ASA is operating in multiple context mode, the stateful failover link resides in the system context, which does not contain any regular data interfaces. Thus the stateful failover link cannot be a shared data link.The implementation of the failover process between the active and standby units can be either stateless or stateful. In a stateless failover implementation, the standby unit of a failover pair takes on the IP and Media Access Control (MAC) addresses of the old active unit during a failover event. This mechanism enablesnetwork clients to maintain their existing network configurations? however, because no network state information is retained, the clients must reestablish their network connections through the new active unit. By contrast, the active unit in a stateful failover implementation transmits certain types of state information through a stateful failover link to the standby unit. This exchange of state information ensures that the standby unit can preserve the state information for open connections during the failover process. Because the state information is preserved, the impact of a failover event on network hosts with open connections can be mitigated.Reference:Cisco: Information About High Availability: Stateful Failover Link Most likely, you would configure a failover key on both the active Cisco Adaptive Security Appliance (ASA) and the standby ASA so that the risk of exposure of virtual private network (VPN) configuration is mitigated. An ASA can share its stateful failover link with a regular data interface only when the unit is operating in single context, routed mode. However, Cisco strongly recommends using a dedicated Ethernet interface or sharing a LAN failover link instead because stateful failover traffic can increase the possibility of congestion and can negatively impact the performance of the shared data interface. In addition, all LAN failover and stateful failover information is transmitted as clear text by default. Therefore, sharing the stateful failover link with a regular data interface can unnecessarily expose VPN configuration information, such as user names, passwords, and preshared keys (PSKs) to malicious users on the shared network segment. You can mitigate this risk by configuring a failover key on both the active unit and the standby unit to protect failover information.
You would not configure a failover key so that the active ASA can monitor the status of the standby ASA. An ASA can be configured to participate in either an active/standby or an active/active failover configuration. In an active/standby configuration, one ASA serves as the active unit and forwards traffic. A second ASA functions as a standby unit, which monitors the status of the active unit. If a failover event is triggered, the standby unit takes on the role of the active unit.
You would not configure a failover key so that both ASA devices forward traffic for a given group of security contexts. An active/active failover configuration enables both ASAs to forward traffic for a select group of security contexts. With active/active failover, two failover groups exist as security contexts on each ASA. When a failover event is triggered, a failover group can become active on a standby unit or the entire standby unit can become the new active unit. Because an active/active failover configuration relies on security contexts, both ASAs must be in multiple context mode before active/active failover can be implemented. The failoverconfiguration for each unit in an active/active failover configuration is managed from within the system context.
Unlike user contexts, the system context does not contain any normal data interfaces.
You would not configure a failover key so that the stateful failover link cannot use a regular data interface.
Instead, you would configure an ASA to operate in multiple context, routed mode or multiple context, transparent mode. An ASA operating in multiple context, routed mode or multiple context, transparent mode does not support using a regular data interface as the stateful failover link. When an ASA is operating in multiple context mode, the stateful failover link resides in the system context, which does not contain any regular data interfaces. Thus the stateful failover link cannot be a shared data link.
The implementation of the failover process between the active and standby units can be either stateless or stateful. In a stateless failover implementation, the standby unit of a failover pair takes on the IP and Media Access Control (MAC) addresses of the old active unit during a failover event. This mechanism enablesnetwork clients to maintain their existing network configurations? however, because no network state information is retained, the clients must reestablish their network connections through the new active unit. By contrast, the active unit in a stateful failover implementation transmits certain types of state information through a stateful failover link to the standby unit. This exchange of state information ensures that the standby unit can preserve the state information for open connections during the failover process. Because the state information is preserved, the impact of a failover event on network hosts with open connections can be mitigated.
Reference:
Cisco: Information About High Availability: Stateful Failover Link
Question 7
You enable logging at the end of the session in Cisco FireSIGHT Management Center.
Which of the following is true? (Select the best answer.)
- The log will contain less information than at the beginning of the session.
- You will not be able to log connections handled by an SSL policy.
- Information will be based on only the first few packets of a connection.
- The log will contain information from throughout the course of a connection.
Correct answer: D
Explanation:
In Cisco FireSIGHT Management Center, the log will contain information from throughout the course of a connection if you enable logging at the end of the session, which is also known as endofconnection logging.Endofconnection events are generated when a connection closes, times out, or can no longer be tracked because of memory constraints. Endofconnection events contain significantly more information than beginningofconnection events because they can draw upon data collected throughout the course of a connection. This additional information can be used to create traffic profiles, generate connection summaries, or graphically represent connection data. In addition, the data can be used for detailed analysis or to trigger correlation rules based on session data. Endofconnection events are also required to log encrypted connections that are handled by a Secure Sockets Layer (SSL) policy because there is not enough information in the first few packets to indicate that a connection is encrypted.Beginningofconnection events contain less information than endofconnection events. Cisco FireSIGHT Management Center, which was formerly called Sourcefire Defense Center, can log beginningofconnection events and endofconnection events for various types of network traffic. Although most network traffic will generate both kinds of events, blocked or blacklisted traffic is typically denied without further processing and therefore only generates beginningofconnection events. Beginningofconnection events contain a limited amount of information because they are generated based on the information contained in the first few packets of a connection.Reference:Cisco: Logging Connections in Network Traffic: Logging the Beginning or End of Connections In Cisco FireSIGHT Management Center, the log will contain information from throughout the course of a connection if you enable logging at the end of the session, which is also known as endofconnection logging.
Endofconnection events are generated when a connection closes, times out, or can no longer be tracked because of memory constraints. Endofconnection events contain significantly more information than beginningofconnection events because they can draw upon data collected throughout the course of a connection. This additional information can be used to create traffic profiles, generate connection summaries, or graphically represent connection data. In addition, the data can be used for detailed analysis or to trigger correlation rules based on session data. Endofconnection events are also required to log encrypted connections that are handled by a Secure Sockets Layer (SSL) policy because there is not enough information in the first few packets to indicate that a connection is encrypted.
Beginningofconnection events contain less information than endofconnection events. Cisco FireSIGHT Management Center, which was formerly called Sourcefire Defense Center, can log beginningofconnection events and endofconnection events for various types of network traffic. Although most network traffic will generate both kinds of events, blocked or blacklisted traffic is typically denied without further processing and therefore only generates beginningofconnection events. Beginningofconnection events contain a limited amount of information because they are generated based on the information contained in the first few packets of a connection.
Reference:
Cisco: Logging Connections in Network Traffic: Logging the Beginning or End of Connections
Question 8
Which of the following MPF elements can be used to configure Application layer protocol inspection? (Select the best answer.)
- a class map
- a policy map
- a service policy
- a global policy
- an extended access list
- a standard access list
Correct answer: B
Explanation:
A policy map can be used to configure Application layer protocol inspection. Modular Policy Framework (MPF) is a Cisco Adaptive Security Appliance (ASA) feature that provides a flexible method of enabling security policies on an interface. This framework consists of three basic components: class maps, policy maps, and service policies. A class map identifies a specific flow of traffic, a policy map determines the action that will be performed on the traffic, and a service policy ties this action to a specific interface. Application inspection is one of the actions that can be applied to traffic with a policy map. Services that embed IP addresses in the packet or utilize dynamically assigned ports for secondary channels require deep packet inspection, which is provided by Application layer protocol inspection. Some traffic, such as File Transfer Protocol (FTP) traffic, might be dropped if inspection for that protocol is not enabled. Application inspection can be configured within the global service policy and within an interface service policy. Service policies can be applied to an individual interface or globally to all interfaces? if traffic matches both an interface policy and a global policy, only the interface policy will be applied to that particular traffic flow.A class map cannot be used to configure Application layer protocol inspection. Class maps identify traffic by matching a variable characteristic that you specify, such as traffic going to a unique IP address or traffic using a specific port. Generally, each class map can contain only a single match statement, and a packet can match only a single class map within the policy map of a particular feature type. For example, if a packet matched a class map for FTP inspection and a class map for traffic policing, the ASA would apply both policy map actions to the packet. However, if a packet matched a class map for FTP inspection and a second, different class map that included FTP inspection, the ASA would apply only the actions of the first matching policy map. Class maps are assigned to a policy map, which defines the action or actions to be performed on the traffic.A service policy cannot be used to configure Application layer protocol inspection. Service policies tie the policy map to the interface and can be applied to an individual interface or globally to all interfaces? if traffic matches both an interface policy and a global policy, only the interface policy will be applied to that particular traffic flow. Service policies can be configured by using Cisco Adaptive Security Device Manager (ASDM) or by commandline interface (CLI) configuration. Neither an extended access list nor a standard access list can be used to configure Application layer protocol inspection. Access control lists (ACLs) can be used to filter traffic based on a set of configured rules. You can create either standard or extended ACLs. Whereas standard ACLs can be used to filter based only on source IP addresses, extended ACLs can be used to filter based on source and destination IP addresses, protocols, and ports. A class map can match traffic to an extended ACL that is specified as a parameter to the accesslist keyword in a match statement.Reference:Cisco: Using Modular Policy Framework: Information About Inspection Policy MapsCisco: Getting Started With Application Layer Protocol Inspection: Configuring Application Layer Protocol Inspection A policy map can be used to configure Application layer protocol inspection. Modular Policy Framework (MPF) is a Cisco Adaptive Security Appliance (ASA) feature that provides a flexible method of enabling security policies on an interface. This framework consists of three basic components: class maps, policy maps, and service policies. A class map identifies a specific flow of traffic, a policy map determines the action that will be performed on the traffic, and a service policy ties this action to a specific interface. Application inspection is one of the actions that can be applied to traffic with a policy map. Services that embed IP addresses in the packet or utilize dynamically assigned ports for secondary channels require deep packet inspection, which is provided by Application layer protocol inspection. Some traffic, such as File Transfer Protocol (FTP) traffic, might be dropped if inspection for that protocol is not enabled. Application inspection can be configured within the global service policy and within an interface service policy. Service policies can be applied to an individual interface or globally to all interfaces? if traffic matches both an interface policy and a global policy, only the interface policy will be applied to that particular traffic flow.
A class map cannot be used to configure Application layer protocol inspection. Class maps identify traffic by matching a variable characteristic that you specify, such as traffic going to a unique IP address or traffic using a specific port. Generally, each class map can contain only a single match statement, and a packet can match only a single class map within the policy map of a particular feature type. For example, if a packet matched a class map for FTP inspection and a class map for traffic policing, the ASA would apply both policy map actions to the packet. However, if a packet matched a class map for FTP inspection and a second, different class map that included FTP inspection, the ASA would apply only the actions of the first matching policy map. Class maps are assigned to a policy map, which defines the action or actions to be performed on the traffic.
A service policy cannot be used to configure Application layer protocol inspection. Service policies tie the policy map to the interface and can be applied to an individual interface or globally to all interfaces? if traffic matches both an interface policy and a global policy, only the interface policy will be applied to that particular traffic flow. Service policies can be configured by using Cisco Adaptive Security Device Manager (ASDM) or by commandline interface (CLI) configuration. Neither an extended access list nor a standard access list can be used to configure Application layer protocol inspection. Access control lists (ACLs) can be used to filter traffic based on a set of configured rules. You can create either standard or extended ACLs. Whereas standard ACLs can be used to filter based only on source IP addresses, extended ACLs can be used to filter based on source and destination IP addresses, protocols, and ports. A class map can match traffic to an extended ACL that is specified as a parameter to the accesslist keyword in a match statement.
Reference:
Cisco: Using Modular Policy Framework: Information About Inspection Policy Maps
Cisco: Getting Started With Application Layer Protocol Inspection: Configuring Application Layer Protocol Inspection
Question 9
To which of the following are you most likely to connect to manage a Cisco router in ROMmon mode? (Select 2 choices.)
- an auxiliary port
- a console port
- a serial port
- an Ethernet port
- a VTY port
Correct answer: AB
Explanation:
Of the available choices, you are most likely to use either an auxiliary (AUX) port or a console port to manage a Cisco router in readonly memory (ROM) monitor (ROMmon) mode. ROMmon is a management mode that Cisco routers and switches revert to when the system cannot find a software image, the software image is corrupted, or the configuration register has been set to manually enter ROMmon mode. Because ROMmon is an outofband management method, it can be used to recover system software images, passwords, or other configuration data even when the router or switch is in a state where it can no longer forward packets. On a Cisco router, you could use either the console port or the AUX port for outofband access if the router is in ROMmon mode. The AUX port on a Cisco router is typically capable of supporting most of the features available on a console port. Cisco switches either do not have AUX ports or do not support certain features, such as system recovery, on their AUX ports if they have them.You are not likely to use a serial port, an Ethernet port, or a virtual terminal (VTY) port to manage a Cisco router in ROMmon mode. Serial ports and Ethernet ports are used to directly connect Cisco routers to other network devices. However, you cannot access ROMmon mode by using any of these ports. Management applications and administrators who want to manage a Cisco device when it is operating in its normal state could connect to the device by using VTY application protocols such as telnet or Secure Shell (SSH). Reference:Cisco: ROM Monitor: Entering the ROM Monitor Of the available choices, you are most likely to use either an auxiliary (AUX) port or a console port to manage a Cisco router in readonly memory (ROM) monitor (ROMmon) mode. ROMmon is a management mode that Cisco routers and switches revert to when the system cannot find a software image, the software image is corrupted, or the configuration register has been set to manually enter ROMmon mode. Because ROMmon is an outofband management method, it can be used to recover system software images, passwords, or other configuration data even when the router or switch is in a state where it can no longer forward packets. On a Cisco router, you could use either the console port or the AUX port for outofband access if the router is in ROMmon mode. The AUX port on a Cisco router is typically capable of supporting most of the features available on a console port. Cisco switches either do not have AUX ports or do not support certain features, such as system recovery, on their AUX ports if they have them.
You are not likely to use a serial port, an Ethernet port, or a virtual terminal (VTY) port to manage a Cisco router in ROMmon mode. Serial ports and Ethernet ports are used to directly connect Cisco routers to other network devices. However, you cannot access ROMmon mode by using any of these ports. Management applications and administrators who want to manage a Cisco device when it is operating in its normal state could connect to the device by using VTY application protocols such as telnet or Secure Shell (SSH).
Reference:
Cisco: ROM Monitor: Entering the ROM Monitor
Question 10
RADIUS and TACACS+ have which of the following in common? (Select the best answer.)
- They communicate by using the same transport protocol.
- They are AAA protocols.
- They are Ciscoproprietary protocols.
- They encrypt the entire packet.
Correct answer: B
Explanation:
Terminal Access Controller Access Control System Plus (TACACS+) and Remote Authentication DialIn User Service (RADIUS) are both Authentication, Authorization, and Accounting (AAA) protocols. However, there are some important differences between TACACS+ and RADIUS.TACACS+ encrypts the entire body of a packet and provides router command authorization capabilities.TACACS+ is a Ciscoproprietary protocol that uses Transmission Control Protocol (TCP) for transport during AAA operations. TACACS+ provides more security and flexibility than other authentication protocols, such as RADIUS, which is an open standard protocol commonly used as an alternative to TACACS+. Because TACACS+ can be used to encrypt the entire body of a packet, users who intercept the encrypted packet cannot view the user name or contents of the packet. In addition, TACACS+ provides flexibility by separating the authentication, authorization, and accounting functions of AAA. This enables granular control of access to resources. For example, TACACS+ gives administrators control over access to configuration commands?users can be permitted or denied access to specific configuration commands. Because of this flexibility, TACACS+ is used with Cisco Secure Access Control Server (ACS), which is a software tool that is used to manage user authorization for router access.RADIUS was developed as an Internet Engineering Task Force (IETF) standard protocol. Like TACACS+, RADIUS is a protocol used with AAA operations. However, RADIUS uses User Datagram Protocol (UDP) for packet delivery and is less secure and less flexible than TACACS+. RADIUS encrypts only the password of a packet? the rest of the packet would be viewable if the packet were intercepted by a malicious user. With RADIUS, the authentication and authorization functions of AAA are combined into a single function, which limits the flexibility that administrators have when configuring these functions. Furthermore, RADIUS does not provide router command authorization capabilities.Reference:Cisco: TACACS+ and RADIUS Comparison: Compare TACACS+ and RADIUS Terminal Access Controller Access Control System Plus (TACACS+) and Remote Authentication DialIn User Service (RADIUS) are both Authentication, Authorization, and Accounting (AAA) protocols. However, there are some important differences between TACACS+ and RADIUS.
TACACS+ encrypts the entire body of a packet and provides router command authorization capabilities.
TACACS+ is a Ciscoproprietary protocol that uses Transmission Control Protocol (TCP) for transport during AAA operations. TACACS+ provides more security and flexibility than other authentication protocols, such as RADIUS, which is an open standard protocol commonly used as an alternative to TACACS+. Because TACACS+ can be used to encrypt the entire body of a packet, users who intercept the encrypted packet cannot view the user name or contents of the packet. In addition, TACACS+ provides flexibility by separating the authentication, authorization, and accounting functions of AAA. This enables granular control of access to resources. For example, TACACS+ gives administrators control over access to configuration commands?
users can be permitted or denied access to specific configuration commands. Because of this flexibility, TACACS+ is used with Cisco Secure Access Control Server (ACS), which is a software tool that is used to manage user authorization for router access.
RADIUS was developed as an Internet Engineering Task Force (IETF) standard protocol. Like TACACS+, RADIUS is a protocol used with AAA operations. However, RADIUS uses User Datagram Protocol (UDP) for packet delivery and is less secure and less flexible than TACACS+. RADIUS encrypts only the password of a packet? the rest of the packet would be viewable if the packet were intercepted by a malicious user. With RADIUS, the authentication and authorization functions of AAA are combined into a single function, which limits the flexibility that administrators have when configuring these functions. Furthermore, RADIUS does not provide router command authorization capabilities.
Reference:
Cisco: TACACS+ and RADIUS Comparison: Compare TACACS+ and RADIUS
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



