Download Cisco Certified Network Associate (200-301 CCNA).200-301.PassGuide.2020-01-09.27q.vcex
| Vendor: | Cisco |
| Exam Code: | 200-301 |
| Exam Name: | Cisco Certified Network Associate (200-301 CCNA) |
| Date: | Jan 09, 2020 |
| File Size: | 234 KB |
| Downloads: | 4 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
All 30 users on a single floor of a building are complaining about network slowness. After investigating the access switch, the network administrator notices that the MAC address table is full (10,000 entries) and all traffic is being flooded out of every port. Which action can the administrator take to prevent this from occurring?
- Configure port-security to limit the number of mac-addresses allowed on each port
- Upgrade the switch to one that can handle 20,000 entries
- Configure private-vlans to prevent hosts from communicating with one another
- Enable storm-control to limit the traffic rate
- Configure a VACL to block all IP traffic except traffic to and from that subnet
Correct answer: A
Question 2
Which two keying mechanisms are available within MACsec? (Choose two.)
- IKE
- GDOI
- SAP
- MKA
- Diffie-Hellman
Correct answer: CD
Explanation:
Reference: https://www.cisco.com/c/dam/en/us/solutions/collateral/enterprise/design-zone-security/how_to_intro_macsec_ndac_guide.pdf Reference: https://www.cisco.com/c/dam/en/us/solutions/collateral/enterprise/design-zone-security/how_to_intro_macsec_ndac_guide.pdf
Question 3
Which two features are supported on the Cisco Adaptive Security Virtual Appliance? (Choose two.)
- high availability
- EtherChannel
- site-to-site VPN
- PAK-based licensing
- multiple contexts
- clustering
Correct answer: AC
Explanation:
Reference: https://www.cisco.com/c/en/us/products/collateral/security/adaptive-security-virtual-appliance-asav/datasheet-c78-733399.html Reference: https://www.cisco.com/c/en/us/products/collateral/security/adaptive-security-virtual-appliance-asav/datasheet-c78-733399.html
Question 4
Which type of authentication and encryption does SNMPv3 use at the authPriv security level?
- username authentication with MD5 or SHA encryption
- MD5 or SHA authentication with DES encryption
- username authentication with DES encryption
- DES authentication with MD5 or SHA encryption
Correct answer: B
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/snmp/configuration/xe-3se/3850/snmp-xe-3se-3850-book/nm-snmp-snmpv3.pdf Reference: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/snmp/configuration/xe-3se/3850/snmp-xe-3se-3850-book/nm-snmp-snmpv3.pdf
Question 5
Which identity store option allows you to modify the directory services that run on TCP/IP?
- Lightweight Directory Access Protocol
- RSA SecurID server
- RADIUS
- Active Directory
Correct answer: A
Question 6
Which statement about system time and NTP server configuration with Cisco ISE is true?
- The system time and NTP server settings can be configured centrally on the Cisco ISE.
- The system time can be configured centrally on the Cisco ISE, but NTP server settings must be configured individually on each ISE node.
- NTP server settings can be configured centrally on the Cisco ISE, but the system time must be configured individually on each ISE node.
- The system time and NTP server settings must be configured individually on each ISE node.
Correct answer: D
Question 7
Which option is required for inline security group tag propagation?
- Cisco Secure Access Control System
- hardware support
- Security Group Tag Exchange Protocol (SXP) v4
- Cisco Identity Services Engine
Correct answer: B
Question 8
Which protocol sends authentication and accounting in different requests?
- RADIUS
- TACACS+
- EAP-Chaining
- PEAP
- EAP-TLS
Correct answer: B
Question 9
Your company network security policy requires that all network traffic be tunneled to the corporate office. End users must be able to access local LAN resources when they connect to the corporate network. Which two configurations do you implement in Cisco AnyConnect? (Choose two.)
- split-exclude tunneling
- local LAN access
- static routes
- Client Bypass Protocol
- tunnel all
Correct answer: BE
Question 10
Refer to the exhibit. Which type of VPN is used in the configuration?
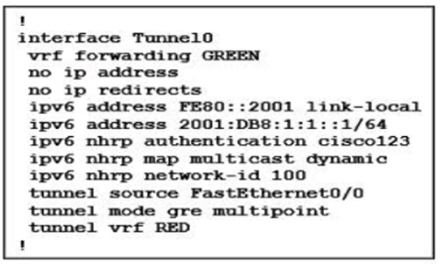
- DMVPN
- FlexVPN
- SSL VPN
- Cisco GET VPN
Correct answer: A
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



