Download Cisco Certified Network Associate (200-301 CCNA).200-301.Marks4Sure.2022-01-14.218q.vcex
| Vendor: | Cisco |
| Exam Code: | 200-301 |
| Exam Name: | Cisco Certified Network Associate (200-301 CCNA) |
| Date: | Jan 14, 2022 |
| File Size: | 14 MB |
| Downloads: | 6 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Which action is taken by a switch port enabled for PoE power classification override?
- When a powered device begins drawing power from a PoE switch port a syslog message is generated
- As power usage on a PoE switch port is checked data flow to the connected device is temporarily paused
- If a switch determines that a device is using less than the minimum configured power it assumes the device has failed and disconnects
- Should a monitored port exceeds the maximum administrative value for power, the port is shutdown and err-disabled
Correct answer: D
Question 2
How öoes the dynamically-learned MAC address feature function?
- The CAM table is empty until ingress traffic arrives at each port
- Switches dynamically learn MAC addresses of each connecting CAM table.
- The ports are restricted and learn up to a maximum of 10 dynamically-learned addresses
- It requires a minimum number of secure MAC addresses to be filled dynamically
Correct answer: A
Question 3
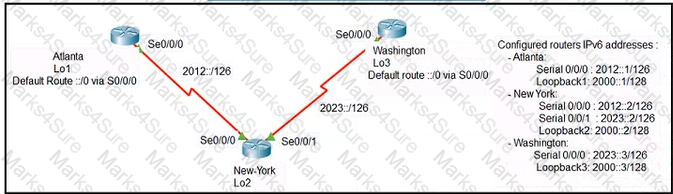
Refer to the exhibit The loopback1 interface of the Atlanta router must reach the loopback3 interface of the Washington router Which two static host routes must be configured on the New York router’ (Choose two)
- ipv6 route 2000::1/128 2012::1
- ipv6 route 2000::3/128 2023::3
- ipv6 route 2000::3/128 s0/0/0
- ipv6 route 2000::1/128 2012::2
- ipv6 route 2000::1/128 s0/0/1
Correct answer: AB
Question 4
Which action does the router take as it forwards a packet through the network?
- The router replaces the original source and destination MAC addresses with the sending router MAC address as the source and neighbor MAC address as the destination
- The router encapsulates the original packet and then includes a tag that identifies the source router MAC address and transmits it transparently to the destination
- The router encapsulates the source and destination IP addresses with the sending router IP address as the source and the neighbor IP address as the destination
- The router replaces the source and destination labels with the sending router interface label as a source and the next hop router label as a destination
Correct answer: A
Question 5
Which goal is achieved by the implementation of private IPv4 addressing on a network?
- provides an added level of protection against Internet exposure
- provides a reduction in size of the forwarding table on network routers
- allows communication across the Internet to other private networks
- allows servers and workstations to communicate across public network boundaries
Correct answer: A
Question 6
What are two benefits of controller-based networking compared to traditional networking? (Choose two)
- controller-based increases network bandwidth usage, while traditional lightens the load on the network.
- controller-based inflates software costs, while traditional decreases individual licensing costs
- Controller-based reduces network configuration complexity, while traditional increases the potential for errors
- Controller-based provides centralization of key IT functions. While traditional requires distributes management function
- controller-based allows for fewer network failure, while traditional increases failure rates.
Correct answer: CD
Question 7
A router running EIGRP has learned the same route from two different paths Which parameter does the router use to select the best path?
- cost
- adminstrative distance
- metric
- as-path
Correct answer: C
Explanation:
If a router learns two different paths for the same network from the same routing protocol, it has to decide which route is better and will be placed in the routing table. Metric is the measure used to decide which route is better (lower number is better). Each routing protocol uses its own metric.For example, RIP uses hop counts as a metric, while OSPF uses cost. If a router learns two different paths for the same network from the same routing protocol, it has to decide which route is better and will be placed in the routing table. Metric is the measure used to decide which route is better (lower number is better). Each routing protocol uses its own metric.For example, RIP uses hop counts as a metric, while OSPF uses cost.
Question 8
Which set of actions satisfy the requirement for multifactor authentication?
- The user swipes a key fob, then clicks through an email link
- The user enters a user name and password, and then clicks a notification in an authentication app on a mobile device
- The user enters a PIN into an RSA token, and then enters the displayed RSA key on a login screen
- The user enters a user name and password and then re-enters the credentials on a second screen
Correct answer: B
Explanation:
This is an example of how two-factor authentication (2FA) works:1. The user logs in to the website or service with their username and password.2. The password is validated by an authentication server and, if correct, the user becomes eligible for the second factor.3. The authentication server sends a unique code to the user’s second-factor method (such as a smartphone app).4. The user confirms their identity by providing the additional authentication for their second-factor method. This is an example of how two-factor authentication (2FA) works:1. The user logs in to the website or service with their username and password.2. The password is validated by an authentication server and, if correct, the user becomes eligible for the second factor.3. The authentication server sends a unique code to the user’s second-factor method (such as a smartphone app).4. The user confirms their identity by providing the additional authentication for their second-factor method.
Question 9
Why was the RFC 1918 address space defined?
- conserve public IPv4 addressing
- preserve public IPv6 address space
- reduce instances of overlapping IP addresses
- support the NAT protocol
Correct answer: A
Question 10
Which statement correctly compares traditional networks and controller-based networks?
- Only traditional networks offer a centralized control plane
- Only traditional networks natively support centralized management
- Traditional and controller-based networks abstract policies from device configurations
- Only controller-based networks decouple the control plane and the data plane
Correct answer: D
Explanation:
Most traditional devices use a distributed architecture, in which each control plane is resided in a networking device. Therefore they need to communicate with each other via messages to work correctly.In contrast to distributed architecture, centralized (or controller-based) architectures centralizes the control of networking devices into one device, called SDN controller Most traditional devices use a distributed architecture, in which each control plane is resided in a networking device. Therefore they need to communicate with each other via messages to work correctly.In contrast to distributed architecture, centralized (or controller-based) architectures centralizes the control of networking devices into one device, called SDN controller
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



