Download Certified Ethical Hacker (312-50v9).312-50.PracticeTest.2017-04-22.425q.vcex
| Vendor: | ECCouncil |
| Exam Code: | 312-50 |
| Exam Name: | Certified Ethical Hacker (312-50v9) |
| Date: | Apr 22, 2017 |
| File Size: | 512 KB |
| Downloads: | 1 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
Which of the following is a hardware requirement that either an IDS/IPS system or a proxy server must have in order to properly function?
- Fast processor to help with network traffic analysis
- They must be dual-homed
- Similar RAM requirements
- Fast network interface cards
Correct answer: B
Explanation:
Dual-homed or dual-homing can refer to either an Ethernet device that has more than one network interface, for redundancy purposes, or in firewall technology, dual-homed is one of the firewall architectures, such as an IDS/IPS system, for implementing preventive security. References: https://en.wikipedia.org/wiki/Dual-homed Dual-homed or dual-homing can refer to either an Ethernet device that has more than one network interface, for redundancy purposes, or in firewall technology, dual-homed is one of the firewall architectures, such as an IDS/IPS system, for implementing preventive security.
References: https://en.wikipedia.org/wiki/Dual-homed
Question 2
In order to show improvement of security over time, what must be developed?
- Reports
- Testing tools
- Metrics
- Taxonomy of vulnerabilities
Correct answer: C
Explanation:
Today, management demands metrics to get a clearer view of security. Metrics that measure participation, effectiveness, and window of exposure, however, offer information the organization can use to make plans and improve programs. References: http://www.infoworld.com/article/2974642/security/4-security-metrics-that-matter.html Today, management demands metrics to get a clearer view of security.
Metrics that measure participation, effectiveness, and window of exposure, however, offer information the organization can use to make plans and improve programs.
References: http://www.infoworld.com/article/2974642/security/4-security-metrics-that-matter.html
Question 3
Passive reconnaissance involves collecting information through which of the following?
- Social engineering
- Network traffic sniffing
- Man in the middle attacks
- Publicly accessible sources
Correct answer: D
Question 4
How can rainbow tables be defeated?
- Password salting
- Use of non-dictionary words
- All uppercase character passwords
- Lockout accounts under brute force password cracking attempts
Correct answer: A
Question 5
The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106:
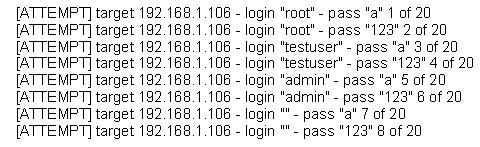
What is most likely taking place?
- Ping sweep of the 192.168.1.106 network
- Remote service brute force attempt
- Port scan of 192.168.1.106
- Denial of service attack on 192.168.1.106
Correct answer: B
Question 6
An NMAP scan of a server shows port 25 is open. What risk could this pose?
- Open printer sharing
- Web portal data leak
- Clear text authentication
- Active mail relay
Correct answer: D
Question 7
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?
Starting NMAP 5.21 at 2011-03-15 11:06
NMAP scan report for 172.16.40.65
Host is up (1.00s latency).
Not shown: 993 closed ports
PORT STATE SERVICE
21/tcp open ftp
23/tcp open telnet
80/tcp open http
139/tcp open netbios-ssn
515/tcp open
631/tcp open ipp
9100/tcp open
MAC Address: 00:00:48:0D:EE:89
- The host is likely a Windows machine.
- The host is likely a Linux machine.
- The host is likely a router.
- The host is likely a printer.
Correct answer: D
Question 8
What type of OS fingerprinting technique sends specially crafted packets to the remote OS and analyzes the received response?
- Passive
- Reflective
- Active
- Distributive
Correct answer: C
Question 9
Which of the following lists are valid data-gathering activities associated with a risk assessment?
- Threat identification, vulnerability identification, control analysis
- Threat identification, response identification, mitigation identification
- Attack profile, defense profile, loss profile
- System profile, vulnerability identification, security determination
Correct answer: A
Question 10
Which system consists of a publicly available set of databases that contain domain name registration contact information?
- WHOIS
- IANA
- CAPTCHA
- IETF
Correct answer: A
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!



